This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Alarm Manager - Override Content error
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Alarm Manager - Override Content error
Alarm Manager - Override Content error
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-24-2017 08:05 AM
Hi,
I'm configuring Alarm manager to run as action a custom php script and I want to Override Content in manner to pass to the script a list of custom arguments, but if I execute the script from command line, this works correctly, instead if executed from Alarm Manager goes in error and in the log file /usr/local/Extreme_Networks/NetSight/appdata/logs/server.log
I see the following error:
2017-07-21 16:24:00,962 ERROR [com.enterasys.netsight.api.notification.NotifyActionContent] Error deserializing loadFromXml xml blob
My php script is:
//********************************************************************************************************
//var_dump($argc); //number of arguments passed
//var_dump($argv); //the arguments passed
//********************************************************************************************************
//
//command to execute example: php Distributed_IPS.php "root" "password" $message "/(?<=src: )(.*)(?=; dst:)/" "CK infected" "192.168.30.34" "8443" "Distributed_IPS"
//
//
//
$username = $argv[1]; //the username is passes as first argument of the script
$password = $argv[2]; //the password is passes as second argument of the script
$message = $argv[3]; //the variable $message is passes as third argument of the script (it contain the checkpoint syslog entire message where extract the source ip address to put in the Distributed_IPS endSystemGroup)
$pattern = $argv[4]; //the pattern to use in the regex expression is passed as fourth argument of the script ( for extract the source ip address is "/(?<=src: )(.*)(?=; dst:)/" )
$errmessage = $argv[5]; //the error message to use in the description is passed as fifth argument of the script
$emcipaddress = $argv[6]; //the ip address of the EMC server is passed as sixth argument of the script
$port = $argv[7]; //the port of the EMC server is passed as seventh argument of the script (default port is 8443)
$endsystemgroup = $argv[8]; //the endSystemGroup where put the offender src ip address is passed as eighth argument of the script (ex: Distributed_IPS)
if (preg_match($pattern, $message, $matches)) {
$ip_address = $matches[0];
//line used for debug ...commend in production
// echo $ip_address.PHP_EOL; // print out the source ip address of the offender client as indicated as src ip address in the check point log message
//remote url to execute for block the offender client
$remote_url = 'https://' . urlencode($username) . ':' . urlencode($password) . '@' . urlencode($emcipaddress) . ':' . urlencode($port) . '/axis/services/NACWebService/addIPToEndSystemGroup?endSystemGroup=' . urlencode($endsystemgroup) . '&ipAddress=' . urlencode($ip_address) . '&description=' . urlencode($errmessage) . '&reauthenticate=true&removeFromOtherGroups=true';
//create a stream context
$opts = array(
'http'=>array(
'method'=>"GET",
'header' => "Authorization: Basic " . base64_encode("$username:$password")
)
);
$context = stream_context_create($opts);
//***********************************example with simple HTTP GET request***************************************************************************************************************************
//*************************************************************************************************************************************************************************************************
$response = file_get_contents($remote_url, false, $context);
// print_r($response); //used for debug
}
else{
echo "No source ip address is present in the checkpoint log message";
}
?>
If I execute this script from command line with the following list of custom arguments:
"root" "password" "mmmmm src: 192.168.10.78; dst: 212.10.10.10; mmmmmm" "/(?<=src: )(.*)(?=; dst:)/" "CK infected" "192.168.30.34" "8443" "Distributed_IPS"
the scripts works as expected.
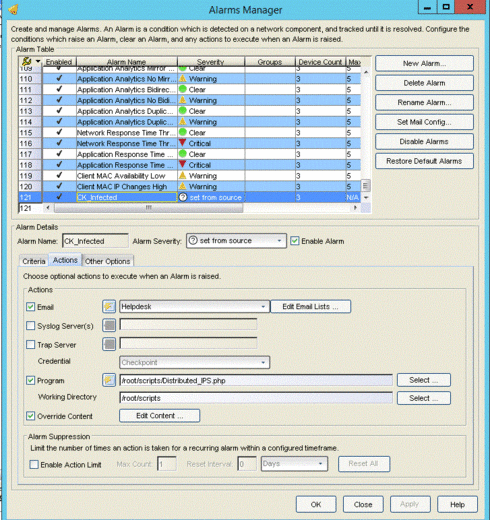
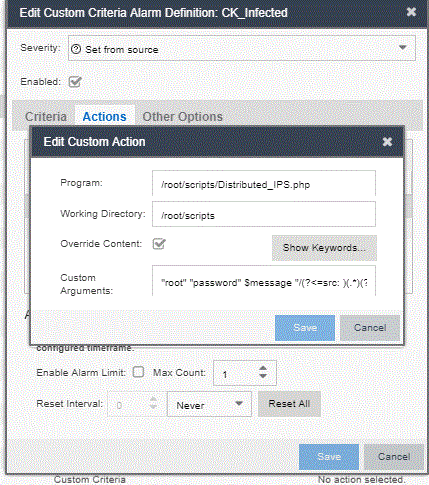
In action manager I configure it as follow:
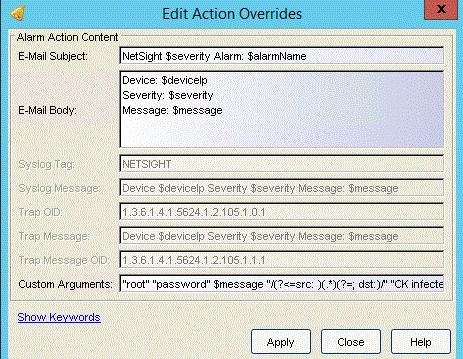
I use in this case the following list of custom arguments as Override Content:
"root" "password" $message "/(?<=src: )(.*)(?=; dst:)/" "CK infected" "192.168.30.34" "8443" "Distributed_IPS"
where I pass to the script the $message of the event.
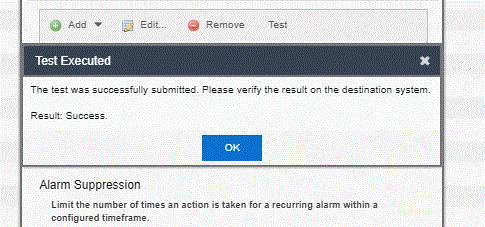
In this case, when the script is executed, despite the Test executed successfully window, the script doesn't work and the error in the server.log file is as descripted above:
2017-07-21 16:24:00,962 ERROR [com.enterasys.netsight.api.notification.NotifyActionContent] Error deserializing loadFromXml xml blob
Why this errro message?
I'm configuring Alarm manager to run as action a custom php script and I want to Override Content in manner to pass to the script a list of custom arguments, but if I execute the script from command line, this works correctly, instead if executed from Alarm Manager goes in error and in the log file /usr/local/Extreme_Networks/NetSight/appdata/logs/server.log
I see the following error:
2017-07-21 16:24:00,962 ERROR [com.enterasys.netsight.api.notification.NotifyActionContent] Error deserializing loadFromXml xml blob
My php script is:
//********************************************************************************************************
//var_dump($argc); //number of arguments passed
//var_dump($argv); //the arguments passed
//********************************************************************************************************
//
//command to execute example: php Distributed_IPS.php "root" "password" $message "/(?<=src: )(.*)(?=; dst:)/" "CK infected" "192.168.30.34" "8443" "Distributed_IPS"
//
//
//
$username = $argv[1]; //the username is passes as first argument of the script
$password = $argv[2]; //the password is passes as second argument of the script
$message = $argv[3]; //the variable $message is passes as third argument of the script (it contain the checkpoint syslog entire message where extract the source ip address to put in the Distributed_IPS endSystemGroup)
$pattern = $argv[4]; //the pattern to use in the regex expression is passed as fourth argument of the script ( for extract the source ip address is "/(?<=src: )(.*)(?=; dst:)/" )
$errmessage = $argv[5]; //the error message to use in the description is passed as fifth argument of the script
$emcipaddress = $argv[6]; //the ip address of the EMC server is passed as sixth argument of the script
$port = $argv[7]; //the port of the EMC server is passed as seventh argument of the script (default port is 8443)
$endsystemgroup = $argv[8]; //the endSystemGroup where put the offender src ip address is passed as eighth argument of the script (ex: Distributed_IPS)
if (preg_match($pattern, $message, $matches)) {
$ip_address = $matches[0];
//line used for debug ...commend in production
// echo $ip_address.PHP_EOL; // print out the source ip address of the offender client as indicated as src ip address in the check point log message
//remote url to execute for block the offender client
$remote_url = 'https://' . urlencode($username) . ':' . urlencode($password) . '@' . urlencode($emcipaddress) . ':' . urlencode($port) . '/axis/services/NACWebService/addIPToEndSystemGroup?endSystemGroup=' . urlencode($endsystemgroup) . '&ipAddress=' . urlencode($ip_address) . '&description=' . urlencode($errmessage) . '&reauthenticate=true&removeFromOtherGroups=true';
//create a stream context
$opts = array(
'http'=>array(
'method'=>"GET",
'header' => "Authorization: Basic " . base64_encode("$username:$password")
)
);
$context = stream_context_create($opts);
//***********************************example with simple HTTP GET request***************************************************************************************************************************
//*************************************************************************************************************************************************************************************************
$response = file_get_contents($remote_url, false, $context);
// print_r($response); //used for debug
}
else{
echo "No source ip address is present in the checkpoint log message";
}
?>
If I execute this script from command line with the following list of custom arguments:
"root" "password" "mmmmm src: 192.168.10.78; dst: 212.10.10.10; mmmmmm" "/(?<=src: )(.*)(?=; dst:)/" "CK infected" "192.168.30.34" "8443" "Distributed_IPS"
the scripts works as expected.
In action manager I configure it as follow:
I use in this case the following list of custom arguments as Override Content:
"root" "password" $message "/(?<=src: )(.*)(?=; dst:)/" "CK infected" "192.168.30.34" "8443" "Distributed_IPS"
where I pass to the script the $message of the event.
In this case, when the script is executed, despite the Test executed successfully window, the script doesn't work and the error in the server.log file is as descripted above:
2017-07-21 16:24:00,962 ERROR [com.enterasys.netsight.api.notification.NotifyActionContent] Error deserializing loadFromXml xml blob
Why this errro message?
3 REPLIES 3
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-24-2017 08:49 AM
I can send you a guide that might help. Please send me an email to my extreme email (ksemba...)
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-24-2017 08:44 AM
Hi Kurt,
I've tried to use the connect module "Distributed IPS", but I'm not able to configure it for Check Point firewall, the sense that in the Connect module asks for the snmpv3 credentials and after I've filled this fields, nothing happens..
If I send snmp traps from Check Point to EMC, I receive the traps, but these are not captured by the connect module...do you have more detailed configurations for the Check Point integration?
The method I've used is a workaround for the connect module.
I've tried to use the connect module "Distributed IPS", but I'm not able to configure it for Check Point firewall, the sense that in the Connect module asks for the snmpv3 credentials and after I've filled this fields, nothing happens..
If I send snmp traps from Check Point to EMC, I receive the traps, but these are not captured by the connect module...do you have more detailed configurations for the Check Point integration?
The method I've used is a workaround for the connect module.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-24-2017 08:21 AM
Hi Antonio,
what is it that you are trying to achieve? If you have an advanced license on EMC (NetSight) you have access to all Connect integration. Of of which is a so called "Distributed IPS". It allows you to forward messages from any security system (IPS, firewall, etc.) to EMC, parse the message and then push the malicious/infected end-system into a restrictive policy within Access Control (NAC).
If this is what you need, I would recommend following that path.
Thanks
what is it that you are trying to achieve? If you have an advanced license on EMC (NetSight) you have access to all Connect integration. Of of which is a so called "Distributed IPS". It allows you to forward messages from any security system (IPS, firewall, etc.) to EMC, parse the message and then push the malicious/infected end-system into a restrictive policy within Access Control (NAC).
If this is what you need, I would recommend following that path.
Thanks