This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- DOS protect log message
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
DOS protect log message
DOS protect log message
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-17-2016 08:49 PM
Hi, i have a problem... I see this messages in the log
I read in extreme documents but its not clear to my. in the ExtremeXOS 16.1 EMS Message Catalog i read what this messages is only informative and in the DOS protect log message article say what "Once the threshold is exceeded, it will stop the packets from reaching the CPU".
So my quetion is:
is there a locking action in the SW? or definitely is only information....
I read in extreme documents but its not clear to my. in the ExtremeXOS 16.1 EMS Message Catalog i read what this messages is only informative and in the DOS protect log message article say what "Once the threshold is exceeded, it will stop the packets from reaching the CPU".
So my quetion is:
is there a locking action in the SW? or definitely is only information....
4 REPLIES 4
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-17-2016 09:39 PM
Maybe this will help... here is a snip of log messages from a core IPTV switch that had an EAPS ring event and there was a flood of mcast joins when ring fails over which is processed by the cpu. You see the port affected and the ip address that was generating the traffic. In our case this did not affect network traffic as this was only mcast joins.... If this were a flood or broadcast storm where the links would be over run then it would still create and acl but it would not stop the traffic on the interface it only protects the traffic from over whelming the cpu...
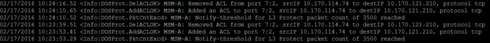
02/17/2016 14:36:41.77 MSM-A: Removed ACL from port 2:2, srcIP 172.16.150.60 to destIP 0.0.0.0, protocol udp02/17/2016 14:36:37.12
MSM-A: Notify-threshold for L3 Protect packet count of 3500 reached
02/17/2016 14:36:36.15 MSM-A: Added an ACL to port 2:2, srcIP 172.16.150.60 to destIP 0.0.0.0, protocol udp
02/17/2016 14:36:36.05 MSM-A: Notify-threshold for L3 Protect packet count of 3500 reached
02/17/2016 14:36:35.06 MSM-A: No traffic pattern found
02/17/2016 14:36:34.97 MSM-A: Notify-threshold for L3 Protect packet count of 3500 reached
If this were a bcast storm the destination address would be the bcast address for subnet and not 0.0.0.0 ...
02/17/2016 14:36:41.77 MSM-A: Removed ACL from port 2:2, srcIP 172.16.150.60 to destIP 0.0.0.0, protocol udp02/17/2016 14:36:37.12
MSM-A: Notify-threshold for L3 Protect packet count of 3500 reached
02/17/2016 14:36:36.15 MSM-A: Added an ACL to port 2:2, srcIP 172.16.150.60 to destIP 0.0.0.0, protocol udp
02/17/2016 14:36:36.05 MSM-A: Notify-threshold for L3 Protect packet count of 3500 reached
02/17/2016 14:36:35.06 MSM-A: No traffic pattern found
02/17/2016 14:36:34.97 MSM-A: Notify-threshold for L3 Protect packet count of 3500 reached
If this were a bcast storm the destination address would be the bcast address for subnet and not 0.0.0.0 ...
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-17-2016 08:57 PM
An important key to understanding how the DDOS to cpu works is knowing what packets are sent to the cpu versus switched in hardware. You can run this in active mode which will create the acl on the fly and block packets it is targeting in the acl from the cpu or you can run in simulated mode (we do this) where you get same traps but no acl is created. If you are lucky you get mac address or ip address in the info. This does not stop a flood on your interfaces it only protects the cpu from being overrun...
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-17-2016 08:54 PM
Hello Daniel,
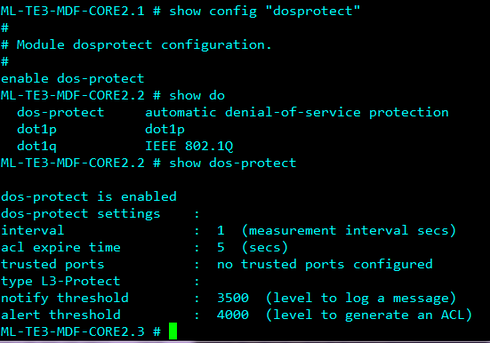
Dos-protect is a simulated process that will send packets to the CPU for examination based on the amount specified in the configuration (show configuration dosprotect). Once the configured amount is exceeded it will inform with log messages. Dos-protect checks a specified amount of packets for patterns. If none are found it will also notify of this in the log.
What type of locking action are you referring to? It will help if you can provided output to "show config dosprotoect".
Dos-protect is a simulated process that will send packets to the CPU for examination based on the amount specified in the configuration (show configuration dosprotect). Once the configured amount is exceeded it will inform with log messages. Dos-protect checks a specified amount of packets for patterns. If none are found it will also notify of this in the log.
What type of locking action are you referring to? It will help if you can provided output to "show config dosprotoect".
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-17-2016 08:54 PM
thanks for you commets... i'm referiring to blocking complete the LAN services for about 5 seg.