This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (WiNG)
- NAC with WiNG Wireless
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NAC with WiNG Wireless
NAC with WiNG Wireless
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-02-2017 04:21 PM
Hi,
we are setting up test environment for 802.1x for wireless users using NAC and WiNG wireless solution before implementing to production.
we have 4 groups:
Corporate
Consultants
Guest
BYOD
we only used 1 SSID and dynamically assigned the VLAN based on this groups.
Corporate - VLAN 5
Consultants - VLAN 10
Guest - VLAN 15
BYOD - VLAN 20
Corporate requirements are the device is domain computer and the user is domain user (LDAP)
Consultants - user is domain user (LDAP) and MAC address white listed in NAC
Guest - Local users in NAC only
BYOD - user is domain user (LDAP) and any device
Corporate,Consultants and BYOD is working very well. the rule hits, LDAP is working fine, authentication is passed and dynamically assigned to right VLAN based on groups.
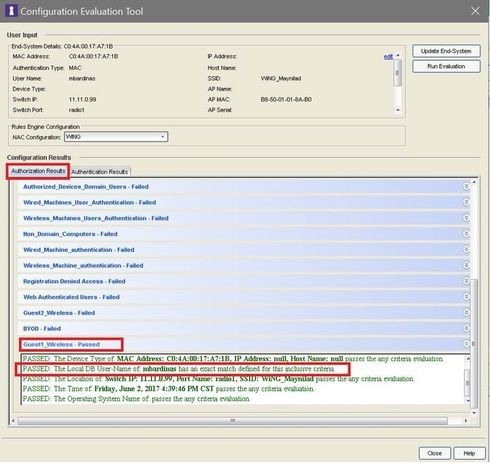
but we have issue with Guest Group. in screenshot below, user hit the right rule (Guest1_Wireless)
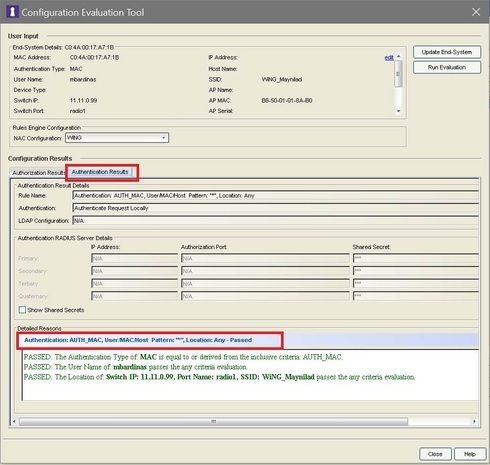
below screenshot is the Authentication results, user also passed the authentication
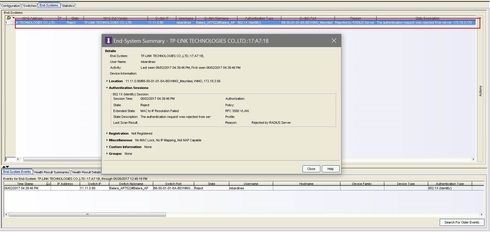
but the user is still rejected due to "the authentication is rejected by radius server" (proxy). as you can see the screenshot above, the authentication is already passed with "Authentication request locally" so no need to forward the authentication request to radius server, but NAC still forward it to radius server which will naturally reject the request.
why NAC still forward the authentication request to Radius server? it's already hit the first Authentication rule which is "Authenticate request locally".
we are setting up test environment for 802.1x for wireless users using NAC and WiNG wireless solution before implementing to production.
we have 4 groups:
Corporate
Consultants
Guest
BYOD
we only used 1 SSID and dynamically assigned the VLAN based on this groups.
Corporate - VLAN 5
Consultants - VLAN 10
Guest - VLAN 15
BYOD - VLAN 20
Corporate requirements are the device is domain computer and the user is domain user (LDAP)
Consultants - user is domain user (LDAP) and MAC address white listed in NAC
Guest - Local users in NAC only
BYOD - user is domain user (LDAP) and any device
Corporate,Consultants and BYOD is working very well. the rule hits, LDAP is working fine, authentication is passed and dynamically assigned to right VLAN based on groups.
but we have issue with Guest Group. in screenshot below, user hit the right rule (Guest1_Wireless)
below screenshot is the Authentication results, user also passed the authentication
but the user is still rejected due to "the authentication is rejected by radius server" (proxy). as you can see the screenshot above, the authentication is already passed with "Authentication request locally" so no need to forward the authentication request to radius server, but NAC still forward it to radius server which will naturally reject the request.
why NAC still forward the authentication request to Radius server? it's already hit the first Authentication rule which is "Authenticate request locally".
3 REPLIES 3
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-03-2017 03:02 PM
Thanks Scott and Ryan.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-03-2017 02:16 PM
Hello Marlon,
The configuration evaluation screenshots you have pasted were done on the end system when it was in a MAC authenticated state. The "Authentication" type is set to "MAC" authentication in the first two screenshots. MAC authentication by default is set to be processed locally, and there are no requirements for MAC authentication so it has been accepted, as expected.
The reject message authentication type is 802.1x. As Scott said above AAA configuration will determine what method is used to authenticate the user, so since you have a line in the 802.1x authentication line in the AAA configuration when the user is attempting to authentication via 802.1x it will be sent to the back end radius server.
Do guests have a username/password that would be accepted by NPS? One of the issues with with guest access on an 802.1x network is that they don't have working credentials, and will be presented with a prompt to put in credentials, which will always be rejected because they don't have any.
You may be able to utilize "secure guest access" portal feature, where you have an open SSID were a user registers and EAC will dynamically create and send them credentials to use on the 802.1x SSID.
Thanks Marlon
-Ryan
The configuration evaluation screenshots you have pasted were done on the end system when it was in a MAC authenticated state. The "Authentication" type is set to "MAC" authentication in the first two screenshots. MAC authentication by default is set to be processed locally, and there are no requirements for MAC authentication so it has been accepted, as expected.
The reject message authentication type is 802.1x. As Scott said above AAA configuration will determine what method is used to authenticate the user, so since you have a line in the 802.1x authentication line in the AAA configuration when the user is attempting to authentication via 802.1x it will be sent to the back end radius server.
Do guests have a username/password that would be accepted by NPS? One of the issues with with guest access on an 802.1x network is that they don't have working credentials, and will be presented with a prompt to put in credentials, which will always be rejected because they don't have any.
You may be able to utilize "secure guest access" portal feature, where you have an open SSID were a user registers and EAC will dynamically create and send them credentials to use on the 802.1x SSID.
Thanks Marlon
-Ryan
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-02-2017 04:35 PM
Hello,
The Rules Engine should not pertain to the proxy RADIUS logic, but rather, the AAA Config. The Config EVAL Tool is something you'd want to rule out here for now, and use the NAC debug to troubleshoot instead.
NAC will proxy RADIUS traffic if your AAA Config is such that it is setup for Proxy RADIUS and also if a Local Authentication line higher in the AAA Config did not match. We'd need to see the NAC database and NAC debug to determine this in most cases. You can use this article to assist and you may also want to open a case with GTAC.
https://gtacknowledge.extremenetworks.com/articles/How_To/NAC-Troubleshooting-Tips-Debug-methodology...
Regards,
Scott Keene
NMS/NAC Support
The Rules Engine should not pertain to the proxy RADIUS logic, but rather, the AAA Config. The Config EVAL Tool is something you'd want to rule out here for now, and use the NAC debug to troubleshoot instead.
NAC will proxy RADIUS traffic if your AAA Config is such that it is setup for Proxy RADIUS and also if a Local Authentication line higher in the AAA Config did not match. We'd need to see the NAC database and NAC debug to determine this in most cases. You can use this article to assist and you may also want to open a case with GTAC.
https://gtacknowledge.extremenetworks.com/articles/How_To/NAC-Troubleshooting-Tips-Debug-methodology...
Regards,
Scott Keene
NMS/NAC Support