This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (WiNG)
- Wing RFS4000 Routing
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Wing RFS4000 Routing
Wing RFS4000 Routing
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-29-2017 10:45 AM
Hi community
I finally got my hands on some of the Wing products.
I now have a requirement form a client and require some assistance. (Still new to the product)
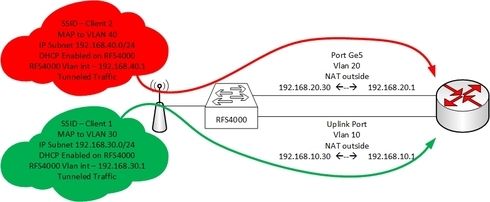
The Client currently has a RFS4000 with some AP's deployed.
He is running a Corporate SSID that is natted to the "Uplink port" on the RFS4000
The clients connecting to this Corporate SSID receives a IP from the RFS4000 in the VLAN.
The RFS4000 then NATS the wireless client traffic to the internal LAN via the Uplink port on the RFS4000
The client now wants to add another SSID for guests, this will be a open SSID with not authentication (The client will implement a upstream captive portal). The client wants to route the guest traffic over a completely seperate uplink (ge5) that will ge connected to the same router used for corporate but on a different interface.
This wireless guest traffic must also be natted to this uplink (ge5).
The network diagram below
First question can I specify more than one interface as "NAT outside"?
I have tested using PBR but it seems to always route via the uplink port vlan...
Any suggestions/advice....
I finally got my hands on some of the Wing products.
I now have a requirement form a client and require some assistance. (Still new to the product)
The Client currently has a RFS4000 with some AP's deployed.
He is running a Corporate SSID that is natted to the "Uplink port" on the RFS4000
The clients connecting to this Corporate SSID receives a IP from the RFS4000 in the VLAN.
The RFS4000 then NATS the wireless client traffic to the internal LAN via the Uplink port on the RFS4000
The client now wants to add another SSID for guests, this will be a open SSID with not authentication (The client will implement a upstream captive portal). The client wants to route the guest traffic over a completely seperate uplink (ge5) that will ge connected to the same router used for corporate but on a different interface.
This wireless guest traffic must also be natted to this uplink (ge5).
The network diagram below
First question can I specify more than one interface as "NAT outside"?
I have tested using PBR but it seems to always route via the uplink port vlan...
Any suggestions/advice....
5 REPLIES 5
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-05-2017 11:36 AM
Hi Daniel
Thank you for the config this worked as expected.
I then added a Policy based route to route both WLAN networks to different gateways.
Thx for the feedback
Thank you for the config this worked as expected.
I then added a Policy based route to route both WLAN networks to different gateways.
Thx for the feedback
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-30-2017 09:22 PM
I haven't tried this, so I don't know if it will work, but here's what I would do...
Create two "outside" VLANs:
- VLAN100
- VLAN200
Enable dhcp in both of them and configure them as ip nat outside.
config self interface vlan100 ip address dhcp ip nat outside interface vlan200 ip address dhcp ip nat outside exit
Create your "inside" vlans:
- VLAN10
- VLAN40
Configure their local IP addresses and configure them as ip nat inside
config self interface vlan10 ip address 192.168.10.1/24 ip nat inside interface vlan40 ip address 192.168.40.1/24 ip nat inside exit
Configure interface ge1 as trunk including vlans 100 & 200 tagged
config self interface ge1 switchport mode trunk switchport trunk native vlan 1 no switchport trunk native tagged switchport trunk allowed vlan 1,100,200 exit
Create two Access lists:
- nat1-rule: allows ip addresses from vlan 10
- nat2-rule: allows ip addresses from vlan 40
config ip access-list nat1-rule permit ip 192.168.10.0/24 any rule-precedence 10 ip access-list nat2-rule permit ip 192.168.40.0/24 any rule-precedence 10 exit
Create a rule that allows nat from addresses in nat1-rule to vlan100
Create a rule that allows nat from addresses in nat2-rule to vlan200
config self ip nat inside source list nat1-rule precedence 1 interface vlan100 overload ip nat inside source list nat2-rule precedence 2 interface vlan200 overload exit
If everything works as expected, vlan 10 addresses should nat using vlan 100 ip address, and addresses from vlan 40 should nat using vlan 200 ip address.
Let me know if this works as expected.
All CLI commands to do this:
! ip access-list nat1-rule permit ip 192.168.10.0/24 any rule-precedence 10 ! ip access-list nat2-rule permit ip 192.168.40.0/24 any rule-precedence 10 ! vx9000 00-0C-29-CA-0E-38 interface ge1 switchport mode trunk switchport trunk native vlan 1 no switchport trunk native tagged switchport trunk allowed vlan 1,100,200 interface vlan1 ip address 10.1.1.70/24 interface vlan10 ip address 192.168.10.1/24 ip nat inside interface vlan40 ip address 192.168.40.1/24 ip nat inside interface vlan100 ip address dhcp ip nat outside interface vlan200 ip address dhcp ip nat outside
ip nat inside source list nat1-rule precedence 1 interface vlan100 overload ip nat inside source list nat2-rule precedence 2 interface vlan200 overload
Create two "outside" VLANs:
- VLAN100
- VLAN200
Enable dhcp in both of them and configure them as ip nat outside.
config self interface vlan100 ip address dhcp ip nat outside interface vlan200 ip address dhcp ip nat outside exit
Create your "inside" vlans:
- VLAN10
- VLAN40
Configure their local IP addresses and configure them as ip nat inside
config self interface vlan10 ip address 192.168.10.1/24 ip nat inside interface vlan40 ip address 192.168.40.1/24 ip nat inside exit
Configure interface ge1 as trunk including vlans 100 & 200 tagged
config self interface ge1 switchport mode trunk switchport trunk native vlan 1 no switchport trunk native tagged switchport trunk allowed vlan 1,100,200 exit
Create two Access lists:
- nat1-rule: allows ip addresses from vlan 10
- nat2-rule: allows ip addresses from vlan 40
config ip access-list nat1-rule permit ip 192.168.10.0/24 any rule-precedence 10 ip access-list nat2-rule permit ip 192.168.40.0/24 any rule-precedence 10 exit
Create a rule that allows nat from addresses in nat1-rule to vlan100
Create a rule that allows nat from addresses in nat2-rule to vlan200
config self ip nat inside source list nat1-rule precedence 1 interface vlan100 overload ip nat inside source list nat2-rule precedence 2 interface vlan200 overload exit
If everything works as expected, vlan 10 addresses should nat using vlan 100 ip address, and addresses from vlan 40 should nat using vlan 200 ip address.
Let me know if this works as expected.
All CLI commands to do this:
! ip access-list nat1-rule permit ip 192.168.10.0/24 any rule-precedence 10 ! ip access-list nat2-rule permit ip 192.168.40.0/24 any rule-precedence 10 ! vx9000 00-0C-29-CA-0E-38 interface ge1 switchport mode trunk switchport trunk native vlan 1 no switchport trunk native tagged switchport trunk allowed vlan 1,100,200 interface vlan1 ip address 10.1.1.70/24 interface vlan10 ip address 192.168.10.1/24 ip nat inside interface vlan40 ip address 192.168.40.1/24 ip nat inside interface vlan100 ip address dhcp ip nat outside interface vlan200 ip address dhcp ip nat outside
ip nat inside source list nat1-rule precedence 1 interface vlan100 overload ip nat inside source list nat2-rule precedence 2 interface vlan200 overload
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-29-2017 12:03 PM
Thx for the feedback Andrew
I will play around any let you guys know how it goes.
I will play around any let you guys know how it goes.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-29-2017 11:24 AM
The main challenge is that the RFS does not have multiple virtual routers (Extreme: This would be an awesome add-on to the data-plane), meaning that all layer 3 traffic, unless prohibited by ACLs is visible between subnets. (ie: vlan 10 and vlan 20 can "see" each other).
This also explains why NAT outside doesn't do what you expect it to. The router instance in the RFS can only have one default gateway, and PBR is just a kludge to get around the fact that there aren't multiple virtual-routers.
There are several ways to tackle the problem, and Extreme has lots of docs about their captive portal functionality, etc, but personally, I find it much easier to treat any guest traffic as layer 2 only and allow other upstream devices (routers/firewalls/portals) to take care of the nuts and bolts of the layer 3 portion (dhcp/dns/etc). This way, it is completely isolated from the corporate environment. Call me paranoid, but I don't trust the guests and don't want to offer them any exposure to the infrastructure, beyond transporting their traffic at layer 2.
That being said, in your scenario, I would tackle it in one of two ways, preferring the second way as it does not create a bottleneck at the controller :
This also explains why NAT outside doesn't do what you expect it to. The router instance in the RFS can only have one default gateway, and PBR is just a kludge to get around the fact that there aren't multiple virtual-routers.
There are several ways to tackle the problem, and Extreme has lots of docs about their captive portal functionality, etc, but personally, I find it much easier to treat any guest traffic as layer 2 only and allow other upstream devices (routers/firewalls/portals) to take care of the nuts and bolts of the layer 3 portion (dhcp/dns/etc). This way, it is completely isolated from the corporate environment. Call me paranoid, but I don't trust the guests and don't want to offer them any exposure to the infrastructure, beyond transporting their traffic at layer 2.
That being said, in your scenario, I would tackle it in one of two ways, preferring the second way as it does not create a bottleneck at the controller :
- Tunnel the guest SSID back to the RFS on its own VLAN, and then configure ge5 to be an access port on that particular vlan. This will forward the layer 2 traffic out ge5 and into the router/portal/firewall which would provide the DHCP and NAT services.
- Bridge the guest SSID into its own VLAN that is back-hauled through your infrastructure and configure an appropriate switch port in access mode on that VLAN and connect it to the router/portal/firewall interface, which would provide the DHCP and NAT services.