- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- EXOS ACL on VLAN Problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
EXOS ACL on VLAN Problem
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-29-2020 02:34 PM
Hi Everyone,
I am having a problem with my EXOS ACL Policy.
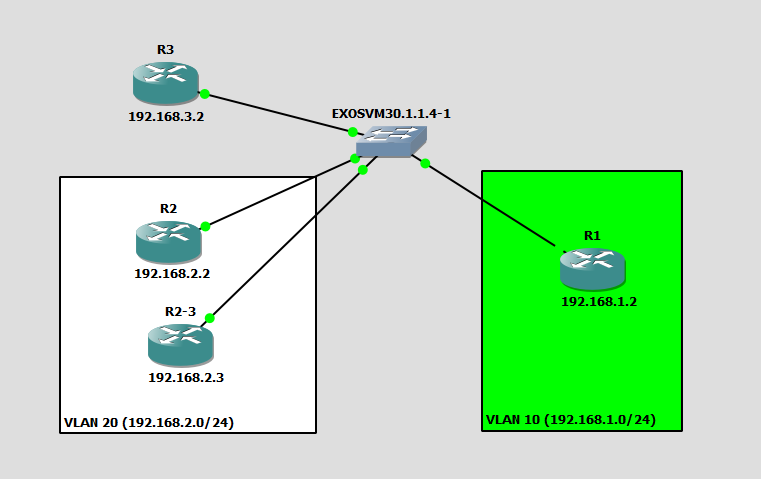
I have 2 VLANs (for lab purposes):
-VLAN 10 - 192.168.1.0/24
-VLAN 20- 192.168.2.0/24.
Objectives:
-VLAN 10 to deny all traffic coming from VLAN 20
-VLAN 20 to accept all traffic coming from VLAN 10
-VLAN 10 to deny only 1 IP from VLAN 20
Here is my topology, I am using a router to act as host, since I do not have any host on my GNS3 lab
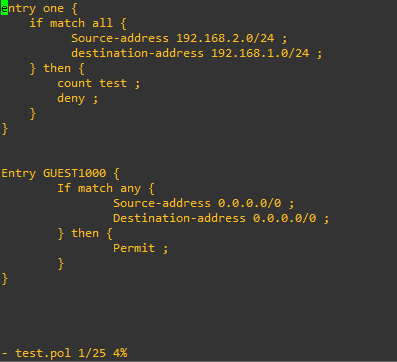
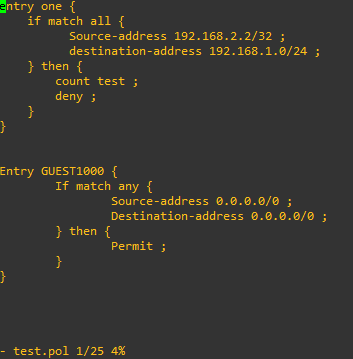
Policy created:
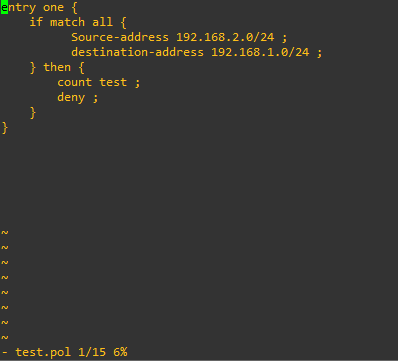
entry one {
if match all {
Source-address 192.168.2.0/24 ;
destination-address 192.168.1.0/24 ;
} then {
count test ;
deny ;
}
}
Scenario 1:
Objectives:
-VLAN 10 to deny all traffic coming from VLAN 20 (not working)
Scenario:
- I apply the policy to vlan10 ingress direction, but both router from vlan20 can still ping 192.168.1.2 router.
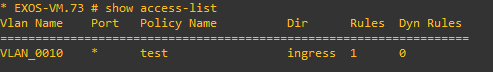
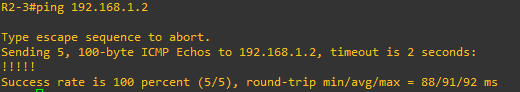
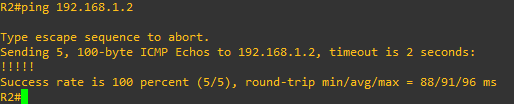
Scenario 2:
Objectives:
-VLAN 10 to deny all traffic coming from VLAN 20 (working)
-VLAN 20 to allow all traffic coming from VLAN 10 (not working)
Scenario:
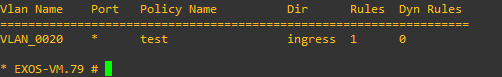
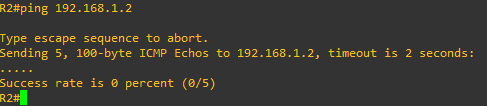
- I apply the policy to vlan20 ingress direction, and the ping was block, the problem now is vlan10 cannot ping vlan20 (even if I made a wildcard rule policy on the end.)
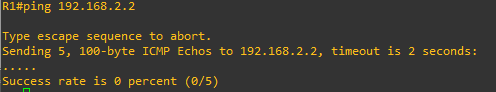
Scenario 3:
Objectives:
-VLAN 10 to deny only 1 IP from VLAN 20
Scenario:
- I apply the policy to vlan20 ingress direction.
- vlan10 blocking the whole vlan20 subnet


Please help me out on this thread. TAC recommendation is to apply the policy on both vlan which I already did. Extreme ACL is quite complicated for me. even tho I have background in programming, seems that extreme is having different perspective in applying ACL policy.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-30-2020 01:03 AM
I haven't personally worked with those policies, however two things come to mind:
1) VLANxxx is considered the interface. So if you want for example to deny traffic from V20->V10 then you have to put a rule denying src:192.168.2.x,dst:192.168.1.x on VLAN0020 ingress, or VLAN0010 egress. Think of ingress as the traffic coming from the cable into the port, only that in this case the port is the virtual VLAN port inside the switch/router.
2) These devices are not stateful firewalls, they are routers. These ACLs work just like that. They don't look at who initiated a communication in order to let a response pass. They just pass/deny exactly what you tell them, and in the direction you indicate, nothing more, nothing less.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-17-2020 08:41 AM
This is good information i understood well thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-30-2020 01:03 AM
I haven't personally worked with those policies, however two things come to mind:
1) VLANxxx is considered the interface. So if you want for example to deny traffic from V20->V10 then you have to put a rule denying src:192.168.2.x,dst:192.168.1.x on VLAN0020 ingress, or VLAN0010 egress. Think of ingress as the traffic coming from the cable into the port, only that in this case the port is the virtual VLAN port inside the switch/router.
2) These devices are not stateful firewalls, they are routers. These ACLs work just like that. They don't look at who initiated a communication in order to let a response pass. They just pass/deny exactly what you tell them, and in the direction you indicate, nothing more, nothing less.
