This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Technical Discussions
- Network Architecture & Design
- I need one device to have a specific ip default ro...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
I need one device to have a specific ip default route to another firewall
I need one device to have a specific ip default route to another firewall
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-14-2015 02:32 PM
Hi I have a remote site that connects through our hub via LAN and they have their own independent Firewall connection for internet. They communicate to a few devices on our network and everything else is blocked via access-list but they need to have a server on our LAN. Now I need to move their server and host it on our network 172.16.x.x but they need it to use their Firewall for internet access. The only thing I can think of is create an access-list on our Firewall uplink to allow everything but their server and add the server to the access-list that connects to their LAN with addition to add another IP default route inside my hub. That’s the only thing I can think of at the moment, does anyone have a better solution?
19 REPLIES 19
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-19-2015 01:18 PM
Hi Everyone,
So far what I have done is I just added a VLAN on my network that extendeds there so I can keep the servers within there own subnet. I'm able to get passed the ACL that resides on they're port uplink but I cannot default route through it. Is there where I need to apply a PBR somewhere?
My Business HUB Customer HUB
17216.0.0 /16 192.168.0.0/24
ACL
Source Destination
VLAN A - 172.16.0.0/16 Deny 192.168.0.0/24
VLAN B - 192.168.2.1 Permit 192.168.0.0/24
Lab address Permit ANY (Succesful)
192.168.2.4
Ping 8.8.8.8 from 192.168.2.4 (Request Timed out)
Next step is I would assume I create a PBR ACL under VLAN B that default routes to their Firewall? The reason for this is because the VLAN resides on my network?
So far what I have done is I just added a VLAN on my network that extendeds there so I can keep the servers within there own subnet. I'm able to get passed the ACL that resides on they're port uplink but I cannot default route through it. Is there where I need to apply a PBR somewhere?
My Business HUB Customer HUB
17216.0.0 /16 192.168.0.0/24
ACL
Source Destination
VLAN A - 172.16.0.0/16 Deny 192.168.0.0/24
VLAN B - 192.168.2.1 Permit 192.168.0.0/24
Lab address Permit ANY (Succesful)
192.168.2.4
Ping 8.8.8.8 from 192.168.2.4 (Request Timed out)
Next step is I would assume I create a PBR ACL under VLAN B that default routes to their Firewall? The reason for this is because the VLAN resides on my network?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-14-2015 03:09 PM
Update
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-14-2015 03:09 PM
you have to create the policy with:
edit policy pbr (policy name)
that will open a vi editor
http://gtacknowledge.extremenetworks.com/articles/How_To/How-to-create-and-apply-an-ACL-in-EXOS/?q=e...
edit policy pbr (policy name)
that will open a vi editor
http://gtacknowledge.extremenetworks.com/articles/How_To/How-to-create-and-apply-an-ACL-in-EXOS/?q=e...
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-14-2015 03:09 PM
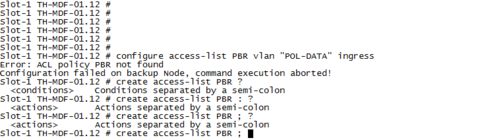
I attempted to create the PBR policy on the switch but I was unsuccessful because I couldn't figure out the next entry. Please see attachment. PS I have a x450a series Summit switch.