- Extreme Networks
- Community List
- Legacy
- Aerohive Migrated Content
- Re: Question about setting up the internal firewal...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Question about setting up the internal firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-27-2018 10:28 AM
We have 2 AP230's, running in a separate subnet (192.168.23.*).
This subnet has full access to our wired network (192.168.11.*). Our Cisco firewall is configured to make this work.
This way, clients connected through WiFi can connect to our server.
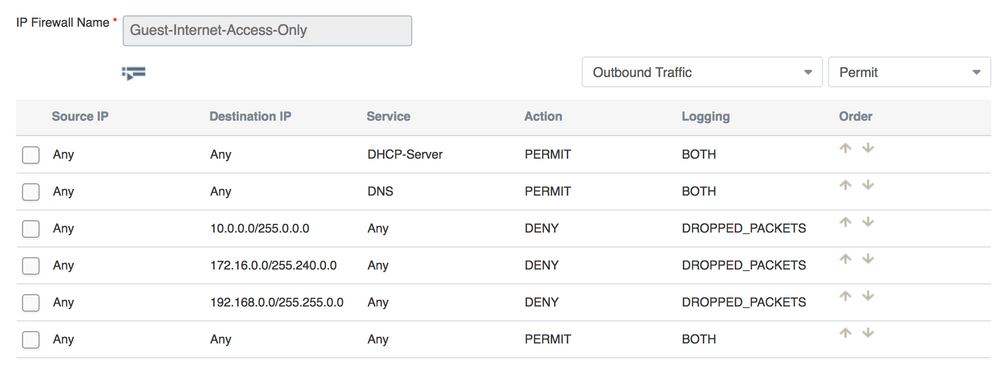
In Hivemanager we have a separate Guests user profile set in Network Policies (Apply a different user profile to various clients and user groups.) This profile is using the Guest-Internet-Access-Only Firewall rules (no idea if this is a default)
As far as I understand, it basically only allows DHCP and DNS traffic between the networks and denies everything else.
My challenge is the following. We have a new presentation screen that allows wireless connections through the WiFi. But it also must connect to our servers.
I have both AP's connected to a switch (that is connected to the 192.168.23.* range). I was thinking about plugging the new screen into that switch, giving it access to our 192.168.11.* range.
And in Hivemanager I want to open up the ports needed, so that guest WiFi users can connect to the screen (it looks like this is not possible at the moment).
What is the best way to open up the following ports? Should I create an application with the rules?
Any help is well appreciated
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-27-2018 03:45 PM
Hello, unless you are using one of our routers, we wouldn't affect ports one way or the other via the AP's configurations. Instead this would be determined by a router or firewall/content filter further upstream from the AP, before the default gateway.
The Guest-Internet-Access-Only firewall is indeed a default object. This will block guest users from connecting to anything in the 10.*.*.*, 172.16.*.*, and 192.168.*.* IP scopes. So, in your use case here, if the presentation screen is using an address from the 192.168.11.* range, the wireless clients on the guest network would not be able to access that screen per the IP firewall rules you have set up on the AP. Users on your internal wireless SSID that are not using this IP firewall policy should be able to reach the presentation screen as far as the APs are concerned.
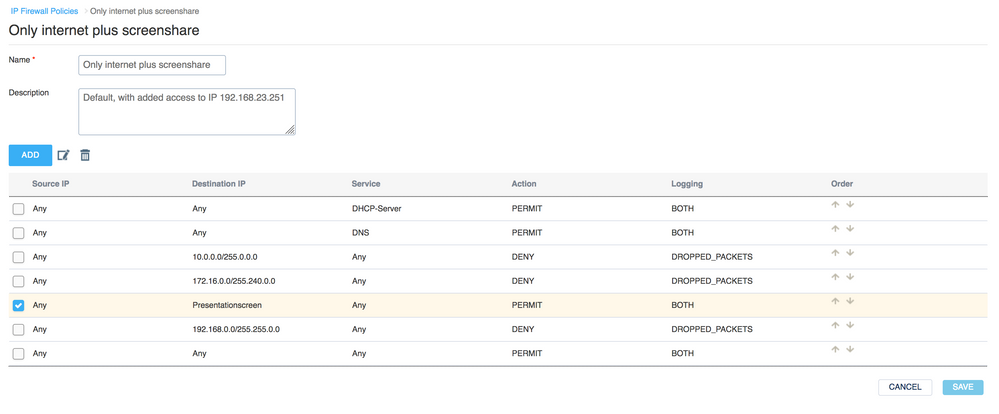
If you'd like to keep using most of the settings in the Guest-Internet-Access-Only firewall, you could clone it by going to Common Objects, then add a rule below DNS but above the first IP scope denial rule, and add a rule that allows traffic to the IP of the presentation screen. The IP Firewall rules are applied in top down order, so the rule to allow traffic to that IP address will be applied before the rule to deny traffic to the 192.168.*.* will be applied. All other internal traffic will still be denied.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-27-2018 04:07 PM
Awesome, that saves me adding exception rules per port. Thanks for the help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-27-2018 04:04 PM
You got it! That should limit guest users to only that single internal address and a normal internet connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-27-2018 03:58 PM
Thank you for your reply Sam, I think it is all clear.
So if I add the following rule, all traffic from the guest internet, should only be allowed to our presentatioscreen (and nowhere else).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-27-2018 03:45 PM
Hello, unless you are using one of our routers, we wouldn't affect ports one way or the other via the AP's configurations. Instead this would be determined by a router or firewall/content filter further upstream from the AP, before the default gateway.
The Guest-Internet-Access-Only firewall is indeed a default object. This will block guest users from connecting to anything in the 10.*.*.*, 172.16.*.*, and 192.168.*.* IP scopes. So, in your use case here, if the presentation screen is using an address from the 192.168.11.* range, the wireless clients on the guest network would not be able to access that screen per the IP firewall rules you have set up on the AP. Users on your internal wireless SSID that are not using this IP firewall policy should be able to reach the presentation screen as far as the APs are concerned.
If you'd like to keep using most of the settings in the Guest-Internet-Access-Only firewall, you could clone it by going to Common Objects, then add a rule below DNS but above the first IP scope denial rule, and add a rule that allows traffic to the IP of the presentation screen. The IP Firewall rules are applied in top down order, so the rule to allow traffic to that IP address will be applied before the rule to deny traffic to the 192.168.*.* will be applied. All other internal traffic will still be denied.