This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Applications
- Analytics & Visibility
- RE: Script for RADIUS certificate monitoring
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Script for RADIUS certificate monitoring
Script for RADIUS certificate monitoring
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-21-2015 01:07 PM
Dear Community,
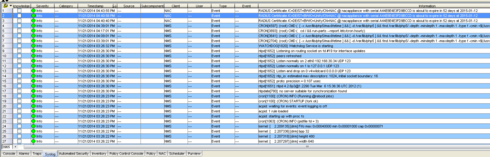
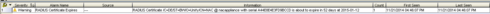
as currently NAC does not have any certificate monitoring (see: https://community.extremenetworks.com/extreme/topics/nac_alarm_if_radius_certificate_is_about_to_exp...) I wrote a script to monitor the RADIUS certificate which I want to share with you. Feel free to use it but please respect the author naming
I realized two types of "alarming".
1) (Aktive): Syslog message to NetSight Server
2) OneFabric API: logEvent. (For this a credentialfile is necessary
3) Alammanager Config.
To use the sciprt:
1) Copy Script to NAC Appliance eg. /root/custom/
2) Set permissions chmod 744 /root/custom/checkcert.sh
3) Set automatic execution via crontab -e eg. 0 0 * * * /root/custom/checkcert.sh
If you have any ideas for improvement or any other comment please feel free to share 🙂
Best Regards
Michael
#!/bin/bash#####################################################
# Author: Michael Kirchner, Unify GmbH & Co. KG #
# E-Mail: michael.kirchner@unify.com #
# This script is free to use with the limitation #
# of naming the author. #
# Description: This script is used to monitor the #
# RADIUS certificate of the NAC Appliance #
#####################################################
#Date: 01/21/2015
# Usage:
# 1) Copy Script to NAC Appliance eg. /root/custom/
# 2) Set permissions chmod 744 /root/custom/checkcert.sh
# 3) Set automatic execution via crontab -e eg. 0 0 * * * /root/custom/checkcert.sh
DATEDIFF=0
CERTDATE=0
CERTDATE1=0
CERTDATE2=0
CERTSFILE=0
TODAY=$(date '+%s')
WARNLEVEL=100 # 100 Days before Certificate expires
SUBJECT=0
SERIAL=0
CONFIG=/opt/nac/server/config/config.properties # Path of the NAC Config
RADIUSPATH=/opt/nac/radius/raddb/certs/external_server.pem # Path of the RADIUS Certificate
#OFCONNECTPATH=/axis/services/BasicReporting/logEvent # OneFabric Connect Path for LogEvent
NSSERVER="" # NetSight Server
NACHOST="" # NAC Appliance Hostname
#USER="" # used for OneFabric Connect API
#PASS="" # used for OneFabric Connect API
#CREDFILE=./cred # Credential File used for OneFabric Connect API
MESSAGE=""
#Function extracts Date from Certificate File
function extractEndDate()
{
CERTDATE=$(openssl x509 -in $CERTSFILE -noout -enddate | cut -f2 -d=)
CERTDATE1=$(date --date="$CERTDATE" '+%s')
CERTDATE2=$(date --date="$CERTDATE" '+%Y-%m-%d')
}
#Function extracts the Subject of the Certificate File
function extractSubject()
{
SUBJECT=$(openssl x509 -in $CERTSFILE -noout -subject | cut -f2 -d" ")
}
#Function extracts the Serialnumber of the Certificate File
function extractSerial()
{
SERIAL=$(openssl x509 -in $CERTSFILE -noout -serial | cut -f2 -d=)
}
# Abort
function die()
{
echo ERROR: $1
exit 1
}
#Function gets Information (NetSight Server, NAC Appliance Hostname)
function getInfos()
{
NSSERVER=$(cat $CONFIG | grep NETSIGHT_SERVER | cut -d"=" -f2)
NACHOST=$(cat $CONFIG | grep NACHOSTNAME | cut -d"=" -f2)
#USER=$(cat $CREDFILE | grep USER | cut -d"=" -f2)
#PASS=$(cat $CREDFILE | grep PASSWORD | cut -d"=" -f2)
}
function warn()
{
echo "WARNING: $1"
}
CERTSFILE=$RADIUSPATH
# Test if file exists, if so then print the expiration date of certificate.
if [ -e $CERTSFILE ] ;
then
extractEndDate $CERTSFILE
DATEDIFF=$(( ($CERTDATE1 - $TODAY) / 86400 ))
extractSubject
extractSerial
getInfos
if [ $WARNLEVEL -gt $DATEDIFF ]
then
if [ $DATEDIFF -gt 0 ]
then
MESSAGE="NAC NAC RADIUS Certificate $SUBJECT @ $NACHOST with serial $SERIAL is about to expire in $DATEDIFF days at $CERTDATE2"
else
MESSAGE="NAC NAC RADIUS Certificate $SUBJECT @ $NACHOST is expired"
fi
else
MESSAGE="NAC NAC RADIUS Certificate $SUBJECT @ $NACHOST serial $SERIAL is valid. Expiry Date: $CERTDATE2 (still $DATEDIFF left)"
fi
#OneFabric Connect
#$(curl --insecure --data "category=NAC Alert&source=$NACHOST&title=RADIUS Certificate Alert&message=$MESSAGE" https://$USER:$PASS@$NSSERVER:8443$OFCONNECTPATH)
#Generation of a Syslog Message to NetSight Server
nc -w0 -u $NSSERVER 514 <<< "<14>$MESSAGE"
else
die $CERTSFILE" file does not exist."
exit 2
fi
exit 0
as currently NAC does not have any certificate monitoring (see: https://community.extremenetworks.com/extreme/topics/nac_alarm_if_radius_certificate_is_about_to_exp...) I wrote a script to monitor the RADIUS certificate which I want to share with you. Feel free to use it but please respect the author naming
I realized two types of "alarming".
1) (Aktive): Syslog message to NetSight Server
2) OneFabric API: logEvent. (For this a credentialfile is necessary
3) Alammanager Config.
To use the sciprt:
1) Copy Script to NAC Appliance eg. /root/custom/
2) Set permissions chmod 744 /root/custom/checkcert.sh
3) Set automatic execution via crontab -e eg. 0 0 * * * /root/custom/checkcert.sh
If you have any ideas for improvement or any other comment please feel free to share 🙂
Best Regards
Michael
#!/bin/bash#####################################################
# Author: Michael Kirchner, Unify GmbH & Co. KG #
# E-Mail: michael.kirchner@unify.com #
# This script is free to use with the limitation #
# of naming the author. #
# Description: This script is used to monitor the #
# RADIUS certificate of the NAC Appliance #
#####################################################
#Date: 01/21/2015
# Usage:
# 1) Copy Script to NAC Appliance eg. /root/custom/
# 2) Set permissions chmod 744 /root/custom/checkcert.sh
# 3) Set automatic execution via crontab -e eg. 0 0 * * * /root/custom/checkcert.sh
DATEDIFF=0
CERTDATE=0
CERTDATE1=0
CERTDATE2=0
CERTSFILE=0
TODAY=$(date '+%s')
WARNLEVEL=100 # 100 Days before Certificate expires
SUBJECT=0
SERIAL=0
CONFIG=/opt/nac/server/config/config.properties # Path of the NAC Config
RADIUSPATH=/opt/nac/radius/raddb/certs/external_server.pem # Path of the RADIUS Certificate
#OFCONNECTPATH=/axis/services/BasicReporting/logEvent # OneFabric Connect Path for LogEvent
NSSERVER="" # NetSight Server
NACHOST="" # NAC Appliance Hostname
#USER="" # used for OneFabric Connect API
#PASS="" # used for OneFabric Connect API
#CREDFILE=./cred # Credential File used for OneFabric Connect API
MESSAGE=""
#Function extracts Date from Certificate File
function extractEndDate()
{
CERTDATE=$(openssl x509 -in $CERTSFILE -noout -enddate | cut -f2 -d=)
CERTDATE1=$(date --date="$CERTDATE" '+%s')
CERTDATE2=$(date --date="$CERTDATE" '+%Y-%m-%d')
}
#Function extracts the Subject of the Certificate File
function extractSubject()
{
SUBJECT=$(openssl x509 -in $CERTSFILE -noout -subject | cut -f2 -d" ")
}
#Function extracts the Serialnumber of the Certificate File
function extractSerial()
{
SERIAL=$(openssl x509 -in $CERTSFILE -noout -serial | cut -f2 -d=)
}
# Abort
function die()
{
echo ERROR: $1
exit 1
}
#Function gets Information (NetSight Server, NAC Appliance Hostname)
function getInfos()
{
NSSERVER=$(cat $CONFIG | grep NETSIGHT_SERVER | cut -d"=" -f2)
NACHOST=$(cat $CONFIG | grep NACHOSTNAME | cut -d"=" -f2)
#USER=$(cat $CREDFILE | grep USER | cut -d"=" -f2)
#PASS=$(cat $CREDFILE | grep PASSWORD | cut -d"=" -f2)
}
function warn()
{
echo "WARNING: $1"
}
CERTSFILE=$RADIUSPATH
# Test if file exists, if so then print the expiration date of certificate.
if [ -e $CERTSFILE ] ;
then
extractEndDate $CERTSFILE
DATEDIFF=$(( ($CERTDATE1 - $TODAY) / 86400 ))
extractSubject
extractSerial
getInfos
if [ $WARNLEVEL -gt $DATEDIFF ]
then
if [ $DATEDIFF -gt 0 ]
then
MESSAGE="NAC NAC RADIUS Certificate $SUBJECT @ $NACHOST with serial $SERIAL is about to expire in $DATEDIFF days at $CERTDATE2"
else
MESSAGE="NAC NAC RADIUS Certificate $SUBJECT @ $NACHOST is expired"
fi
else
MESSAGE="NAC NAC RADIUS Certificate $SUBJECT @ $NACHOST serial $SERIAL is valid. Expiry Date: $CERTDATE2 (still $DATEDIFF left)"
fi
#OneFabric Connect
#$(curl --insecure --data "category=NAC Alert&source=$NACHOST&title=RADIUS Certificate Alert&message=$MESSAGE" https://$USER:$PASS@$NSSERVER:8443$OFCONNECTPATH)
#Generation of a Syslog Message to NetSight Server
nc -w0 -u $NSSERVER 514 <<< "<14>$MESSAGE"
else
die $CERTSFILE" file does not exist."
exit 2
fi
exit 0
4 REPLIES 4
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-22-2015 06:32 AM
Hello Michael,
very helpful. Thanks a lot.
Stephan
very helpful. Thanks a lot.
Stephan
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-21-2015 07:25 PM
This is exactly the kind of post we like to see here. Thanks for sharing!
-Drew
-Drew
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-21-2015 01:38 PM
I agree - great work and absolutely useful! Thanks for sharing it!
Kurt
Kurt
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-21-2015 01:19 PM
Hi Michael,
great work this helps a lot 😉
Cheers!
great work this helps a lot 😉
Cheers!