- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Re: Custom Alarm Email Notification
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Custom Alarm Email Notification
Custom Alarm Email Notification
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-28-2022 10:36 AM
I have created an alarm configuration to send me an email if a switch experiences a SpanGuard event the locks out a port on my EOS switches.
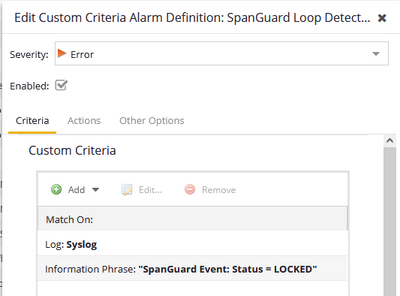
I have the alarm definition setup as follows:
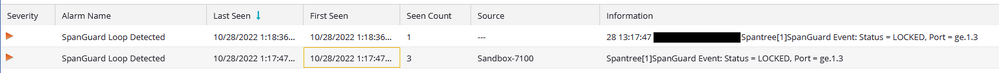
The email comes through fine, but I get 3 copies of one email and a single copy of another email with the same alert. You can see the Information column below is the email I see and the "Seen Count" is the number of emails that are sent to me.
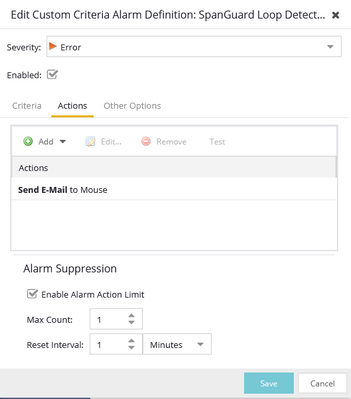
I have gotten the second alarm to only send me a single email by setting up the Alarm Suppression rule in the Actions tab of the rule creation window
I still get the top alarm emailed to me though and I cant figure out how to eliminate multiple emails from being sent.
I also feel there is probably a better way to filter the rule so that the second alert isnt "seen" 3 times.
I have tried altering the Match On: Log: criteria field to include or exclue Syslog and the other, but have not found anything that works. Its almost like XIQ-SE is getting 4 syslog events evertime I reproduce the issue.
Thanks for any guidance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-03-2022 01:44 PM
Can you confirm:
- There is one syslog message from a switch and you get number of emails based on the "Seen count"
- What is the version of ExtremeCloud IQ - Site Engine
What you can try is to get rid of those special characters ":" and "=" in the alarm condition
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-29-2022 03:10 AM - edited 10-30-2022 10:08 PM
Regardless, it's exquisite information. Investigating from gifted music makers is a really fulfilling experience regardless considering the way that they have staff to help with heaps of assessment, changing, etc.
@Michael_M Panorama Charter Login wrote:I have created an alarm configuration to send me an email if a switch experiences a SpanGuard event the locks out a port on my EOS switches.
I have the alarm definition setup as follows:The email comes through fine, but I get 3 copies of one email and a single copy of another email with the same alert. You can see the Information column below is the email I see and the "Seen Count" is the number of emails that are sent to me.
I have gotten the second alarm to only send me a single email by setting up the Alarm Suppression rule in the Actions tab of the rule creation window
I still get the top alarm emailed to me though and I cant figure out how to eliminate multiple emails from being sent.
I also feel there is probably a better way to filter the rule so that the second alert isnt "seen" 3 times.
I have tried altering the Match On: Log: criteria field to include or exclue Syslog and the other, but have not found anything that works. Its almost like XIQ-SE is getting 4 syslog events evertime I reproduce the issue.Thanks for any guidance.