- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Extreme Management Automatic Member / RADIUS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Extreme Management Automatic Member / RADIUS
Extreme Management Automatic Member / RADIUS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-31-2017 06:38 AM
Hi,
Having trouble with the NetSight RADIUS login to work how I would like it.
The intention is to have AD users login that are only part of a specific OU=ITStaff, so there are a couple of things that seems to mention this might be possible. The first is this GTAC knowledge article:
https://extremeportal.force.com/ExtrArticleDetail?an=000079877
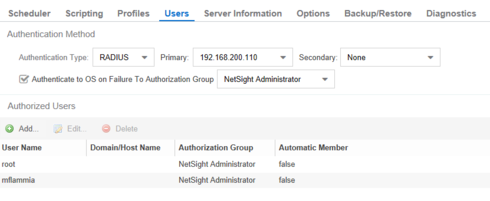
And the field in the authorised members section that shows 'Automatic Member', as per image below:
So I have configured this based on the GTAC article, which has worked OK but not quite how I wont it, and maybe a little contradictory - but that's probably just my interpretation.
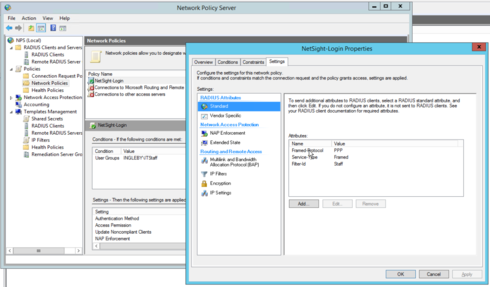
This is the configuration of NPS / RADIUS (Windows 2012), the user group added for ITStaff (which my AD user Mflammia belongs to) and a Filter-Id=staff:
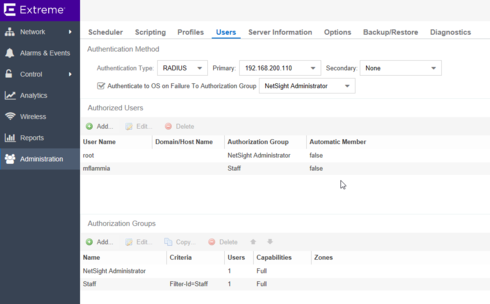
And this is shows me correctly logged in, with my AD account of 'mflamma' and correctly assigned the group of 'Staff'.
So here are the problems:
1) If I remove 'mflammia' from the 'Authorised Users' section I can not login - what I was hoping for since NPS is configured to only give a RADIUS accept back if a member belongs to the group ITStaff, and Filter-Id=Staff that the 'Automatic Member' field would kick in showing true for user mflammia and allow me in?
2) I have to specify 'mflammia' in the 'Authorised Users' section in the 'User Name' field and 'Staff' under the 'Authorisation Group' field, as they are mandatory. If I set the 'Authorisation Group' field to 'NetSight Administrator' instead, then the user will get that group when I login. So my question is, what's the point of setting a 'Criteria' in the 'Authorisation Group' section with a 'Filter-ID=Staff', if you have to manually set the authorisation group in the Authorised Users field anyway - its possibly that no user will ever get the staff authorisation group unless a Filter-ID of Staff is passed? Was hoping that passing the Filter-ID=Staff would mean that the authorisation group of Staff is then selected for that particular user?
Guess my ultimate goal is to have users automatically be able to log into NetSight if they belong to the AD group of ITStaff only, and those users get a authorisation group that is defined by the Filter-ID, instead of having to manually add each of those users into the Authorised Users section in NetSight.
Many thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-31-2017 08:51 AM
After some support it would seem the configuration detailed above was indeed correct and working as it should be. The problem seems to be the way I was logging in - which I was entering just my username as 'mflammia' and getting a message that I was not authorised to login.
When a new user was created in AD and entered in the same way, that user logged in without problem!
The recommended format of the user name should be entered using the UPN (User Principle Name), which in my case would be 'mflammia@ingleby.co.uk' or you could use 'ingleby\mflammia'. In each case when the username was entered in that format I was able to login.
Since trying again, I am now able to login using the username of just 'mflammia'. The reason it seems it didn't work before and works now, is either two possible things. One is that I may have possibly in the past used 'mflammia' as a local account and / or after logging in with the UPN the association to the username 'mflammia' is then made correctly to the domain.
So the answer is then really just to make sure you always login in using your UPN to login!
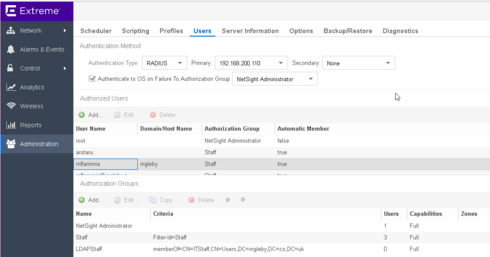
In addition I just wanted to share that you can configure this similarly using LDAP instead of RADIUS. You would need to configure your LDAP connection as usual but you would just need to replace the criteria in the Authorisation Group to use the memberOf (with a '=' instead of a 😅 attribute, as per the example below: