This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- RE: Integration of trend Micro Control Manager sol...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Integration of trend Micro Control Manager solution with Extreme Networks through the Distributed IPS Connect module
Integration of trend Micro Control Manager solution with Extreme Networks through the Distributed IPS Connect module
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-07-2017 02:44 PM
I've done a lab on the integration between the TMMC and the Extreme Networks solution using the Distributed IPS connect module present on the EMC server.
Lab environment
Extreme Management Center (EMC) version 8.0.4
ExtremeControl version 8.0.4
Trend Micro Control Manager version 6.0 Build 1327
Trend Micro Officescan version 12.1
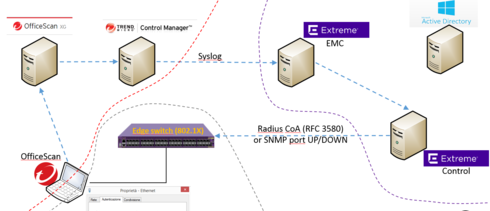
Lab network: actors and data flows
All conversations beetween different vendor are done using standard protocols: Trend Micro TMCM speaks with EMC using syslog and EMC speaks with switches using Radius or SNMP.
Lab configurations
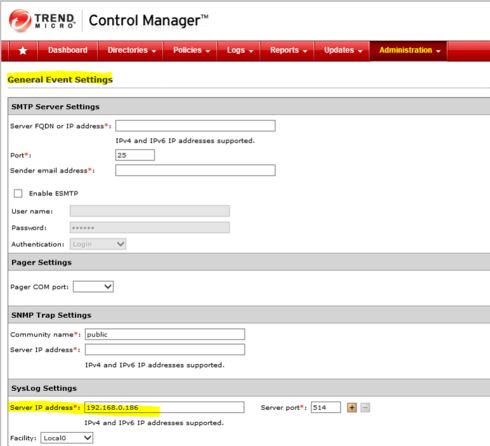
First of all I have configured TMCM to export via syslog the relevant security events to EMC server:
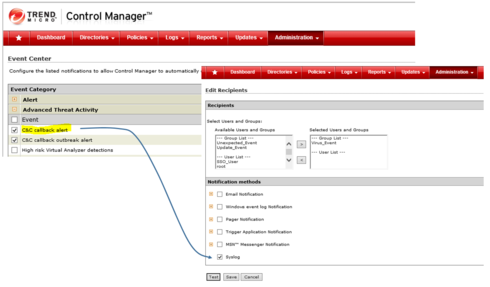
This is a global configuration. After that I have configured TMCM to send only some kind of syslog messages to the EMC (for example C&C botnet callback):
In my lab I have configured TMCM in order to not send messages related to blocked malware.
This is all for TMCM.
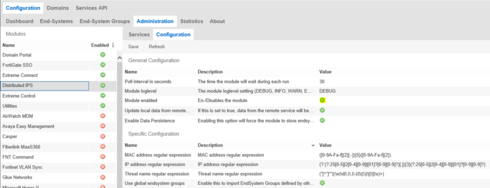
After that I have configured EMC Distributed IPS Connect module. I have enabled the module:
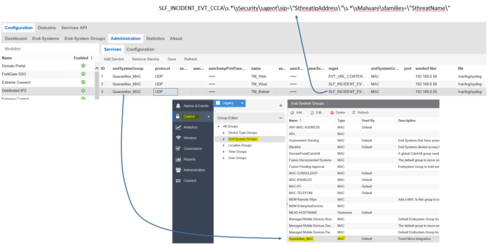
and then I have configured the rules to add infected or hacked host to the Quarantine_MAC group:
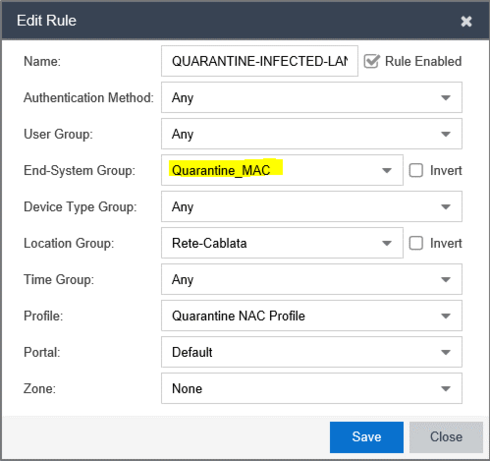
And finally, I have created a NAC rule to move the hosts in Quarantine_MAC Group in a quarantine VLAN. This rule should be placed before other client rules:
Lab environment
Extreme Management Center (EMC) version 8.0.4
ExtremeControl version 8.0.4
Trend Micro Control Manager version 6.0 Build 1327
Trend Micro Officescan version 12.1
Lab network: actors and data flows
All conversations beetween different vendor are done using standard protocols: Trend Micro TMCM speaks with EMC using syslog and EMC speaks with switches using Radius or SNMP.
Lab configurations
First of all I have configured TMCM to export via syslog the relevant security events to EMC server:
This is a global configuration. After that I have configured TMCM to send only some kind of syslog messages to the EMC (for example C&C botnet callback):
In my lab I have configured TMCM in order to not send messages related to blocked malware.
This is all for TMCM.
After that I have configured EMC Distributed IPS Connect module. I have enabled the module:
and then I have configured the rules to add infected or hacked host to the Quarantine_MAC group:
And finally, I have created a NAC rule to move the hosts in Quarantine_MAC Group in a quarantine VLAN. This rule should be placed before other client rules:
2 REPLIES 2
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-11-2017 06:56 AM
The simplest way to test it is uning the C&C botnet callback (as I used).
Once configured, you can simple using a web browser to go to a C&C server like
http://www.antibasic.ga/
This will cause the event triggering
Have a nice day
Once configured, you can simple using a web browser to go to a C&C server like
http://www.antibasic.ga/
This will cause the event triggering
Have a nice day
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-07-2017 08:56 PM
Hi Luca,
Were you able to simulate any TMCM events to test?
Were you able to simulate any TMCM events to test?