- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- Re: EXOS Packet Capture
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
EXOS Packet Capture
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-18-2021 01:00 PM
Hello,
today I played around with the built-in packet capture of EXOS ( How To: How to perform a local packet capture on an EXOS switch | Extreme Portal (force.com) )
I’m able to capture packets and open the pcap file with wireshark, but I only see the following packets:
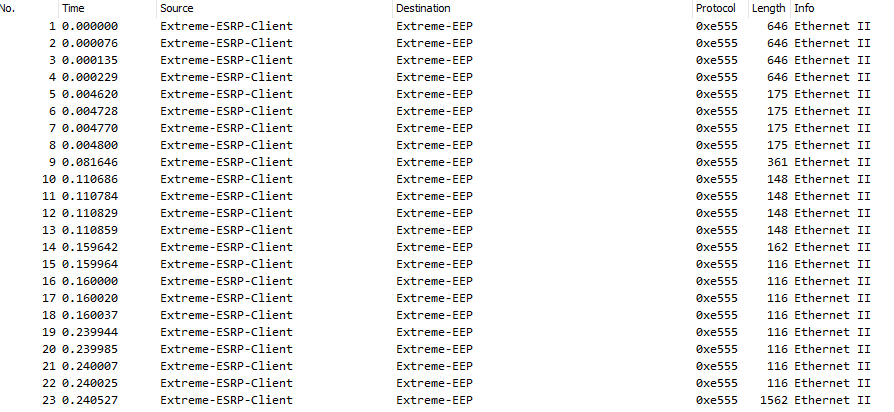
Wondering if I’m doing something wrong or if the feature is something else than I’m thinking. Any hints?
Best regards
Stefan
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-18-2021 03:54 PM
Hi,
You can use the editcap tool to remove the first 52 bytes. Mine looked something like below from Powershell:
PS C:\Program Files\Wireshark> .\editcap.exe -C 52 editcap.pcap newpcap.pcap
syntax below:
PS C:\Program Files\Wireshark> .\editcap.exe -C 52 <original pcap filename> <new pcap filename>Below is more on editcap:
https://www.wireshark.org/docs/man-pages/editcap.html
Before:
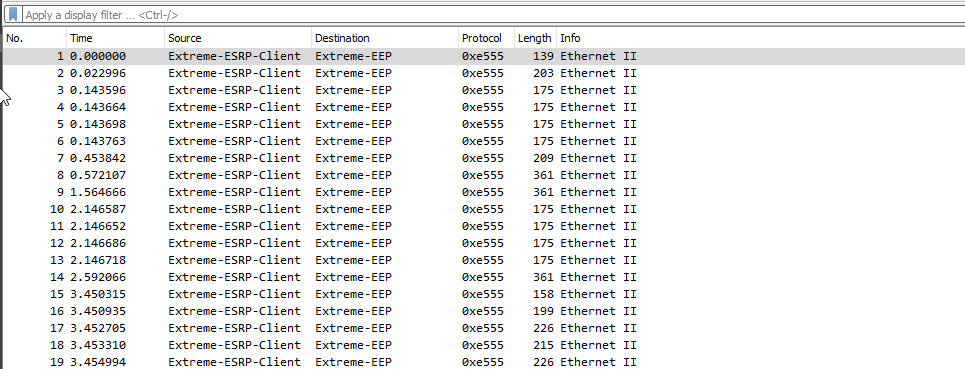
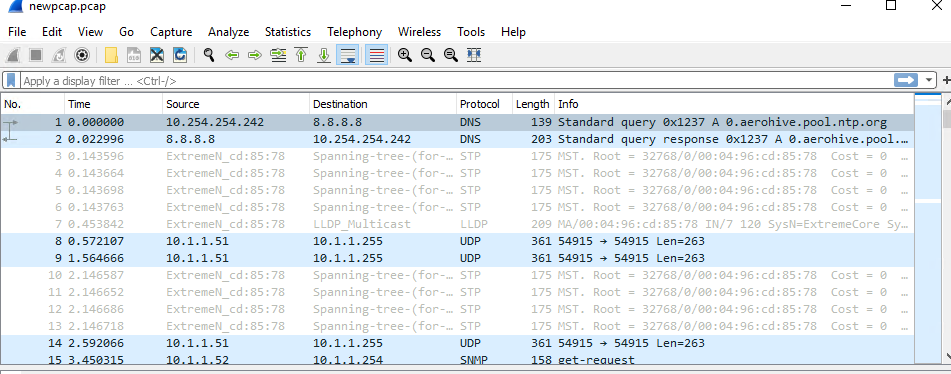
After:
Thanks,
Chris Thompson
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-18-2021 05:51 PM
Hi Stefan,
You bring upa good point(Stefan 1, Chris 0) so that article has been updated:
How To: How to perform a local packet capture on an EXOS switch | Extreme Portal (force.com)
Thanks again,
Chris Thompson
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-18-2021 05:13 PM
Hi Chris,
this worked like a charm, thank you very much! How much “trouble” some 52 bytes can cause… 🙂
Maybe this little information can be added to the GTAC articles?
Best regards
Stefan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-18-2021 03:54 PM
Hi,
You can use the editcap tool to remove the first 52 bytes. Mine looked something like below from Powershell:
PS C:\Program Files\Wireshark> .\editcap.exe -C 52 editcap.pcap newpcap.pcap
syntax below:
PS C:\Program Files\Wireshark> .\editcap.exe -C 52 <original pcap filename> <new pcap filename>Below is more on editcap:
https://www.wireshark.org/docs/man-pages/editcap.html
Before:

After:

Thanks,
Chris Thompson
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-18-2021 01:17 PM
Hi Chris,
thanks for your quick reply! I’m on 30.7.1.1-patch1-86. Switch is an X460-G2. I’m just doing some testing of this feature and don’t want to capture any specific traffic for now. But we might need this feature in the near future. (Troubleshooting at a customers site)
Best regards
Stefan
