- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- RE: MLAG y VRRP (Active/Backup) Error change role
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
MLAG y VRRP (Active/Backup) Error change role
MLAG y VRRP (Active/Backup) Error change role
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-12-2019 10:35 PM
Hello:
I am currently conducting an operation laboratory for MLAG and VRRP, for which I have 3 x440-G2 switches all with firmware version 22.5.1.7 patch1-3. Having the following scheme:
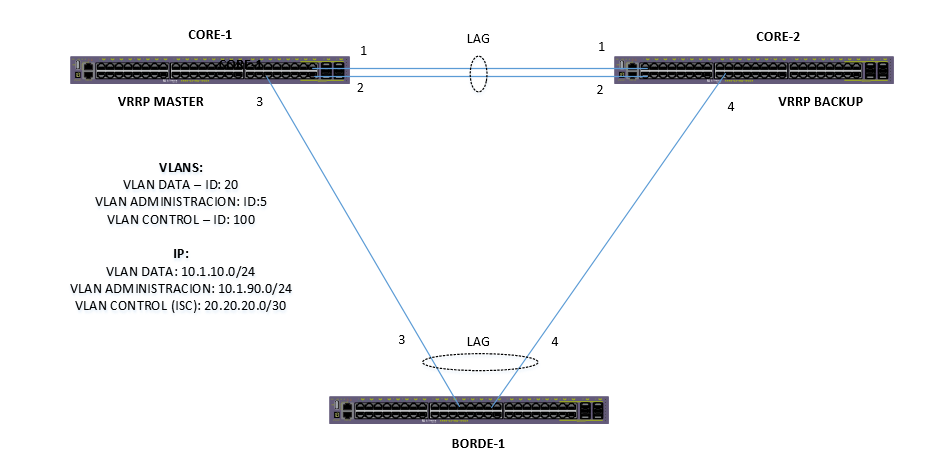
All links are formed through LACP L2, I have the inconvenience that when I disable ports 1-2 of the LAG, both remain as an ACTIVE / ACTIVE role within the VRRP. According to what I understand multicast packages should be propagated through the MLAG ports (these being 3 and 4) to exchange the information of the roles.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-13-2019 10:38 AM
Could you perhaps post the relevant snippets of your configuration?
I’m assuming the port 1+2 LAG is an ISC-style share/vlan?
For each switch, what are the “share” and “mlag” configs?
For each switch which ports are in what vlan?
My hunch is that there may be something in your config that isn’t quite how it’s supposed to be. I have pretty much the same setup, but I have to admit that I also never killed ports 1 and 2 both.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-13-2019 03:11 PM
Usually the vrrp propagates itself via MC, there you are correct.
Could you provide config snippets of Port/Vlan assignments and tagging/untagged as well as the VRRP and MLAG/ISC config snippets?
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-13-2019 04:03 PM
HI:
I enclose the configuration of all switches:
============
BORDE-1
============
create vlan "Administracion"
configure vlan Administracon tag 5
create vlan "Data"
configure vlan Data tag 20
enable sharing 3 grouping 3-4 algorithm address-based L2 lacp
configure vlan Administracon add ports 3 tagged
configure vlan Administracon add ports 7 untagged (PORT USERS)
configure vlan Data add ports 3 tagged
configure vlan Data add ports 9 untagged (PORT USERS)
configure vlan Administracon ipaddress 10.16.46.10 255.255.255.0
================
CORE-2
================
create vlan "administracion"
configure vlan administracion tag 5
create vlan "control"
configure vlan control tag 100
create vlan "data"
configure vlan data tag 20
enable sharing 1 grouping 1-2 algorithm address-based L2 lacp
enable sharing 4 grouping 4 algorithm address-based L2 lacp
configure vlan administracion add ports 1,4 tagged
configure vlan control add ports 1 tagged
configure vlan data add ports 1,4 tagged
configure vlan data ipaddress 10.20.0.3 255.255.255.0
enable ipforwarding vlan data
configure vlan administracion ipaddress 10.1.90.3 255.255.255.0
enable ipforwarding vlan administracion
configure vlan control ipaddress 20.20.20.2 255.255.255.252
create vrrp vlan data vrid 20
configure vrrp vlan data vrid 20 preempt delay 3
create vrrp vlan administracion vrid 6
configure vrrp vlan administracion vrid 6 preempt delay 3
configure vrrp vlan data vrid 20 add 10.20.0.1
configure vrrp vlan administracion vrid 6 add 10.1.90.1
enable vrrp vlan data vrid 20
enable vrrp vlan voz vrid 5
enable vrrp vlan administracion vrid 6
create mlag peer "CORE-1"
configure mlag peer "CORE-1" ipaddress 20.20.20.1
enable mlag port 4 peer "CORE-1" id 1
================
CORE-1
================
create vlan "administracion"
configure vlan administracion tag 5
create vlan "control"
configure vlan control tag 100
create vlan "data"
configure vlan data tag 20
enable sharing 1 grouping 1-2 algorithm address-based L2 lacp
enable sharing 3 grouping 3 algorithm address-based L2 lacp
configure vlan administracion add ports 1,3 tagged
configure vlan control add ports 1 tagged
configure vlan data add ports 1,3 tagged
configure vlan data ipaddress 10.20.0.2 255.255.255.0
enable ipforwarding vlan data
configure vlan administracion ipaddress 10.1.90.2 255.255.255.0
enable ipforwarding vlan administracion
configure vlan control ipaddress 20.20.20.1 255.255.255.252
create vrrp vlan data vrid 20
configure vrrp vlan data vrid 20 priority 200
configure vrrp vlan data vrid 20 preempt delay 3
create vrrp vlan administracion vrid 6
configure vrrp vlan administracion vrid 6 priority 200
configure vrrp vlan administracion vrid 6 preempt delay 3
configure vrrp vlan data vrid 20 add 10.20.0.1
configure vrrp vlan administracion vrid 6 add 10.1.90.1
enable vrrp vlan data vrid 20
enable vrrp vlan administracion vrid 6
create mlag peer "CORE-2"
configure mlag peer "CORE-2" ipaddress 20.20.20.2
enable mlag port 3 peer "CORE-2" id 1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-14-2019 08:37 AM
Hello Kevin,
this somehow looks like an issue “by software design”………………………..
Setup alike yours except that I changed the IP of the border device (same vlan Administr. but different subnet, hardly good to troubleshoot).
Now I deactivated the ISC and started to continously ping from 10.1.90.3 to the border 10.1.9.10 (incoming on port 4 of sharing 3).
But all the traffic back (echo/ping reply) goes up the port 3 of sharing 3 which then arrives at the 10.1.90.2 (getting deny/not-found packet back).
I also tested with different algorithms (l2,l3,l3-4) with lacp on and off on all sides. Please bear in mind that usually the “How to config” guides for MLAG and sharing are referring to the algorithm L3_L4 (LACP).
Does not matter in this case.
As well as Backup-Master (Fabric-Routing) feature; Does not matter whether Off or On in this scenario.
The ARPs as well only get learned to the master port of the sharing on the border. Which is okay.
What is not okay is that those seem to always go out on the master sharing port first.
After a while of configuring working (ISC active…..) and mostly not-working conditions, my border device delivers this output. Just a hint; Look at the differene in Tx Pkt/Tx Byte of Port 3 and 4…..
_________________________________________________________________________________________________
show ports 3-4 statistics port-number
Port Statistics Thu Nov 14 08:12:54 2019
Port Link Tx Pkt Tx Byte Rx Pkt Rx Byte Rx Pkt Rx Pkt Tx Pkt Tx Pkt
State Count Count Count Count Bcast Mcast Bcast Mcast
========= ===== =========== =========== =========== =========== =========== =========== =========== ===========
3 A 2369 231446 7849 554744 31 7383 32 1054
4 A 166 33107 7896 557606 874 6959 0 102
_________________________________________________________________________________________________
show fdb ports 3-4
MAC VLAN Name( Tag) Age Flags Port / Virtual Port List
------------------------------------------------------------------------------------------------------
00:00:5e:00:01:06 Administracion(0005) 0000 d mi 3
00:00:5e:00:01:14 Data(0020) 0016 d m 3
00:04:96:7e:26:36 Administracion(0005) 0000 d mi 3
00:04:96:7e:26:36 Data(0020) 0014 d m 3
00:04:96:7e:26:3f Administracion(0005) 0000 d mi 3
00:04:96:7e:26:3f Data(0020) 0011 d m 3
_________________________________________________________________________________________________
show iparp
VR Destination Mac Age Static VLAN VID Port
VR-Default 10.1.90.1 00:00:5e:00:01:06 0 NO Administracion 5 3
VR-Default 10.1.90.2 00:04:96:7e:26:36 6 NO Administracion 5 3
VR-Default 10.1.90.3 00:04:96:7e:26:3f 7 NO Administracion 5 3
debug hal show fdb
Hardware-learned entries:
MAC VlanId Flags Port HIT TYPE
===================================================
00:04:96:7e:26:3f 5 00001021 3 TRUE L2
00:04:96:7e:26:3f 20 00001021 3 TRUE L2
00:04:96:7e:26:36 5 00001021 3 TRUE L2
00:04:96:7e:26:36 20 00001021 3 TRUE L2
00:00:5e:00:01:14 20 00001021 3 TRUE L2
00:00:5e:00:01:06 5 00001021 3 TRUE L2
Software-learned for "e"-series In-use count: 1
Hardware-learned entries:
MAC VlanId Flags Port HIT TYPE
===================================================
00:04:96:7e:26:3f 5 00001021 3 TRUE L2
00:04:96:7e:26:3f 20 00001021 3 TRUE L2
00:04:96:7e:26:36 5 00001021 3 TRUE L2
00:04:96:7e:26:36 20 00001021 3 TRUE L2
00:00:5e:00:01:14 20 00001021 3 TRUE L2
00:00:5e:00:01:06 5 00001021 3 TRUE L2
Hardware-learned In-use count: 6
Num of msgs from FDB : 351
Bearing the switches I only could use your configs for this setup:
Cores: Summit x670v - V.16.2.5.4-patch1-3
Border: x440-G2 - V.22.7.1.2-patch1-11
I hope my little tests could provide you with any help, though I do not have a proper solution for you except: Do not on purpose turn off the entire ISC. Calculate with enough redundancy so you won’t have this issue by one or two link/cable failure. Sorry 😞
Could you keep us posted about progress, maybe even about any GTAC case you may open?
Best regards
