This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- RE: Netlogin - Dot1X and Mac authentication on the...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Netlogin - Dot1X and Mac authentication on the same port
Netlogin - Dot1X and Mac authentication on the same port
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-20-2017 02:05 PM
I have netlogin successfully working with 802.1x and MAC-based when a single device is connected.
I am now trying to combine this in the form of an Avaya handset - a port is configured with Netlogin:
- tagged VLAN for voice (with MAC auth)
- untagged VLAN for ethernet pass-through on the handset (802.1X auth).
The handset authenticates successfully using MAC-based auth but then it appears the untagged client is forced to use MAC-based as well (rather than try with 802.1x) according to the radius logs.
Has anyone got any suggestions on how to get this working?
Sample config:create vlan "data"
create vlan "voice"
configure vlan data tag 1
configure vlan voice tag 24
create vlan "nt_login"
configure vlan data add ports 7 tagged
configure vlan data add ports 1 untagged
configure vlan voice add ports 1,7 tagged
configure vlan data ipaddress x.x.x.y 255.255.255.0 enable ipforwarding vlan data
configure netlogin vlan nt_login
enable netlogin dot1x mac
configure netlogin mac authentication database-order radius
configure netlogin add mac-list ff:ff:ff:ff:ff:ff 48
configure netlogin mac timers reauth-period 3600
enable netlogin ports 1 dot1x
enable netlogin ports 1 mac
configure netlogin ports 1 mode port-based-vlans
configure netlogin ports 1 no-restart
configure radius netlogin primary server x.x.x.x 1812 client-ip x.x.x.y vr VR-Default
configure radius netlogin primary shared-secret encrypted "..."
enable radius netlogin
I am now trying to combine this in the form of an Avaya handset - a port is configured with Netlogin:
- tagged VLAN for voice (with MAC auth)
- untagged VLAN for ethernet pass-through on the handset (802.1X auth).
The handset authenticates successfully using MAC-based auth but then it appears the untagged client is forced to use MAC-based as well (rather than try with 802.1x) according to the radius logs.
Has anyone got any suggestions on how to get this working?
Sample config:create vlan "data"
create vlan "voice"
configure vlan data tag 1
configure vlan voice tag 24
create vlan "nt_login"
configure vlan data add ports 7 tagged
configure vlan data add ports 1 untagged
configure vlan voice add ports 1,7 tagged
configure vlan data ipaddress x.x.x.y 255.255.255.0 enable ipforwarding vlan data
configure netlogin vlan nt_login
enable netlogin dot1x mac
configure netlogin mac authentication database-order radius
configure netlogin add mac-list ff:ff:ff:ff:ff:ff 48
configure netlogin mac timers reauth-period 3600
enable netlogin ports 1 dot1x
enable netlogin ports 1 mac
configure netlogin ports 1 mode port-based-vlans
configure netlogin ports 1 no-restart
configure radius netlogin primary server x.x.x.x 1812 client-ip x.x.x.y vr VR-Default
configure radius netlogin primary shared-secret encrypted "..."
enable radius netlogin
4 REPLIES 4
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-19-2017 07:47 PM
Sorry, i am sort of having exactly the same issue, how did you solve it? What do you mean by the pass through policy in the Radius server? I have mac policy for the phones and dot1x policy for the pc
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-21-2017 02:44 PM
I seem to have made progress - the "pass-through" policy in the radius server was sending a VSA to assign the unatgged VLAN when the port was already assigned on the switch to the same VLAN untagged - removing the VSA fixed the issue.
A general question - is dot1x point-to-point, i.e. if there are any further switches in between or maybe it is a virtual machine as the supplicant, can this still work?
A general question - is dot1x point-to-point, i.e. if there are any further switches in between or maybe it is a virtual machine as the supplicant, can this still work?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-21-2017 06:40 AM
Hi,
I did try this method also with assigning both the untaged and tagged in the same policy.
I've re-tried where I only assign the tagged vlan when a matched OUI comes through to the radius server.
I also have the existing dot1x policy in place that should place the pass-through client onto the untagged vlan for that particular port.
However, I still get the following in the switch log:
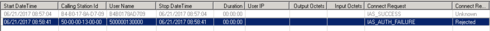
Authentication failed for Netowrk Login MAC user 500000130000 Mac 50:00:00:13:00:00 port 1 Network Login MAC user B4B0178AD709 logged in MAC B4:B0:17:8A:D7:09 port 1 VLAN(s) "voice", authentication Radius From the Radius server logs:
As you can see from the radius logs, it's still receiving the username as a MAC address rather than the windows username.
I have also made sure that the avaya handset has been set to DOT1X Passthrough (tried with passthrough and passthrough with logoff).
If I plug the end client in directly to the switch, it will authenticate as normal using DOT1X using the windows username and password.
I did try this method also with assigning both the untaged and tagged in the same policy.
I've re-tried where I only assign the tagged vlan when a matched OUI comes through to the radius server.
I also have the existing dot1x policy in place that should place the pass-through client onto the untagged vlan for that particular port.
However, I still get the following in the switch log:
Authentication failed for Netowrk Login MAC user 500000130000 Mac 50:00:00:13:00:00 port 1 Network Login MAC user B4B0178AD709 logged in MAC B4:B0:17:8A:D7:09 port 1 VLAN(s) "voice", authentication Radius From the Radius server logs:
As you can see from the radius logs, it's still receiving the username as a MAC address rather than the windows username.
I have also made sure that the avaya handset has been set to DOT1X Passthrough (tried with passthrough and passthrough with logoff).
If I plug the end client in directly to the switch, it will authenticate as normal using DOT1X using the windows username and password.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-21-2017 03:34 AM
Hi ,
I see that you have port 1 untagged in data vlan and tagged in Voice Vlan.
I believe the since the mac authentication is enabled for both the voice and data, the traffic initially would be considered as untagged and then the authentication is successful and the traffic is still in untagged vlan.
This could be avoided by dynamic vlan assignment after the netlogin authentication. The port can be removed from the vlans and the vlan assignment can be done by the radius server after authentication.
Please refer the article below and let us know if it helps!
https://gtacknowledge.extremenetworks.com/articles/How_To/How-to-configure-802-1x-based-Netlogin-wit...
I see that you have port 1 untagged in data vlan and tagged in Voice Vlan.
I believe the since the mac authentication is enabled for both the voice and data, the traffic initially would be considered as untagged and then the authentication is successful and the traffic is still in untagged vlan.
This could be avoided by dynamic vlan assignment after the netlogin authentication. The port can be removed from the vlans and the vlan assignment can be done by the radius server after authentication.
Please refer the article below and let us know if it helps!
https://gtacknowledge.extremenetworks.com/articles/How_To/How-to-configure-802-1x-based-Netlogin-wit...