- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- VLAN help on X440's
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VLAN help on X440's
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-10-2021 07:00 PM
I am pretty new to setting up VLANS and I am needing to setup some on one of my networks. Here is what I have come up with so far.
Total of 6 VLANS
Mgmt
Defualt
Services 10.20.0.1/24 VLAN 2 (Shared resources, Printers, File, Print and Data servers)
Staff 10.20.2.1/24 VLAN 3
Student 10.20.4.1/22 VLAN 4
Guest 10.20.8.1/22 VLAN 5
I am using a Fortigate for Firewall and some routing but I would rather the switches handle all the routing between VLANS. I do not want any of the VLANS to talk to each other with the exception of staff and student talking to services. We are Windows environment using Windows DHCP and DNS for clients.
My question is what would be the best way of handling this?
Do I Trunk the server ports and the Fortigate ports?
How to I keep Staff, Student talking only to services and not each other?
The guest VLAN is for Internet only, that one I my just Trunk to the Fortigate and let it handle it since I do not want it talking to anything but the the Fortigate.
Could I put another Trunk for the Fortigate into the services VLAN for Internet access?
A lot of questions, I know, but I would rather get them all out there instead of making this a long drawn thread.
Thanks
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-10-2021 08:43 PM
Hi Kenny,
depending on the amound of traffic / needed throughput it might be better/easier to let FortiGate handle the routing between the VLANs as it is easier to implement new policies for access between the vlans. In this case the switch does not need any IP-Addresses in the VLANs (except one for Management).
If you still want to do it via the switch, you have to do the following:
- You need one central switch that acts as the router
- Remove the IP-Address for Guest VLAN from this central switch. Move this VLAN + IP-Address to the fortigate. (by doing this, Guest VLAN is separated from the other VLANs)
- Enable ipforwarding on Services, Staff and Student and configure the IP-Addresses that you mentioned above
- Configure DHCP-Relay (How To: How to Configure Bootprelay (DHCP Relay/IP-Helper) in EXOS | Extreme Portal (force.com))
- Create a new VLAN to connect the switch to the fortigate (e.g. 10.20.100.0/29)
- On the Switch create a default route to the fortigate via this new VLAN (e.g. configure iproute add default 10.20.100.1)
- On the fortigate create a route for Student, Services and Staff subnet. Next-Hop: Switch IP-Address of this new VLAN (e.g. Route to 10.20.4.0/22 via 10.20.100.2)
- Create a ACL on the switch that denies traffic between Staff and Student VLAN (How To: How to create and apply an ACL in EXOS | Extreme Portal (force.com))
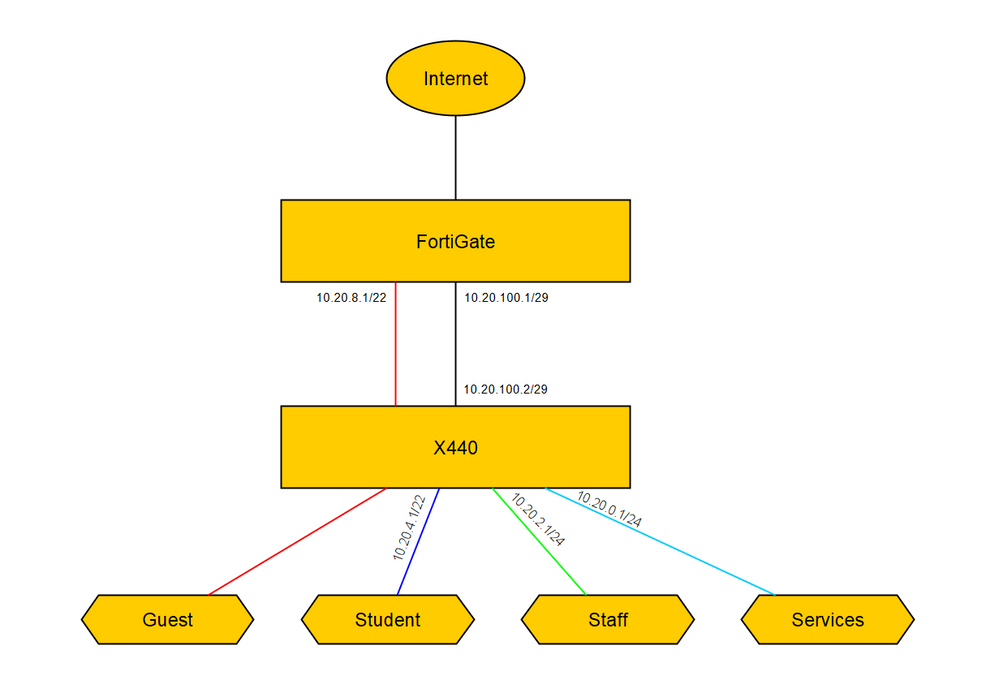
This is it (very) basically. If you have any further questions, feel free to ask.
Best regards
Stefan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-16-2021 03:02 PM
Good to hear!
No there are no issues. Tagged-Frames can be switches between EXOS and EOS devices without problems. If you use STP there might be some things to consider.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-16-2021 02:58 PM
I decided to let the Fortigate handle the routing and it is working out pretty good so far. I do have another question. I have a couple of Enterasys D series switches as well as a one C series. Is there any issue with VLANS going between the Extreme switches and the Enterasys switches?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-10-2021 08:43 PM
Hi Kenny,
depending on the amound of traffic / needed throughput it might be better/easier to let FortiGate handle the routing between the VLANs as it is easier to implement new policies for access between the vlans. In this case the switch does not need any IP-Addresses in the VLANs (except one for Management).
If you still want to do it via the switch, you have to do the following:
- You need one central switch that acts as the router
- Remove the IP-Address for Guest VLAN from this central switch. Move this VLAN + IP-Address to the fortigate. (by doing this, Guest VLAN is separated from the other VLANs)
- Enable ipforwarding on Services, Staff and Student and configure the IP-Addresses that you mentioned above
- Configure DHCP-Relay (How To: How to Configure Bootprelay (DHCP Relay/IP-Helper) in EXOS | Extreme Portal (force.com))
- Create a new VLAN to connect the switch to the fortigate (e.g. 10.20.100.0/29)
- On the Switch create a default route to the fortigate via this new VLAN (e.g. configure iproute add default 10.20.100.1)
- On the fortigate create a route for Student, Services and Staff subnet. Next-Hop: Switch IP-Address of this new VLAN (e.g. Route to 10.20.4.0/22 via 10.20.100.2)
- Create a ACL on the switch that denies traffic between Staff and Student VLAN (How To: How to create and apply an ACL in EXOS | Extreme Portal (force.com))

This is it (very) basically. If you have any further questions, feel free to ask.
Best regards
Stefan
