This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- Re: VMware ESXi guest segmentation with XOS
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VMware ESXi guest segmentation with XOS
VMware ESXi guest segmentation with XOS
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-03-2019 09:32 AM
Hi all,
Are there any features in the XOS series (X460, X590) to provide per guest policy based segmentation (ACLs) within the ESXi hypervisor?
ie ACL per guest on the v-switch ideally driven by ExtremeControl policy.
Thanks in advance for any advice.
Kent.
Are there any features in the XOS series (X460, X590) to provide per guest policy based segmentation (ACLs) within the ESXi hypervisor?
ie ACL per guest on the v-switch ideally driven by ExtremeControl policy.
Thanks in advance for any advice.
Kent.
3 REPLIES 3
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-11-2019 08:40 PM
Hi Antonio,
I didn't play with EAC-VMware integration personally, but another approach would be integrating EXOS with VMware with Direct Attach feature (aka EVB, VEPA), that would imply VM traffic going straight to an EXOS switch without being switched by a vSwitch so you have more EXOS-based control on the traffic - alongisde Policy, ACL and else. Have in mind per-switch and per-port scalability in terms of authentications and Policy roles.
Hope that helps,
Tomasz
I didn't play with EAC-VMware integration personally, but another approach would be integrating EXOS with VMware with Direct Attach feature (aka EVB, VEPA), that would imply VM traffic going straight to an EXOS switch without being switched by a vSwitch so you have more EXOS-based control on the traffic - alongisde Policy, ACL and else. Have in mind per-switch and per-port scalability in terms of authentications and Policy roles.
Hope that helps,
Tomasz
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-07-2019 08:46 AM
Is there an example on how use ExtremeControl for authorize the VMs in the integration with ExtremeControl?
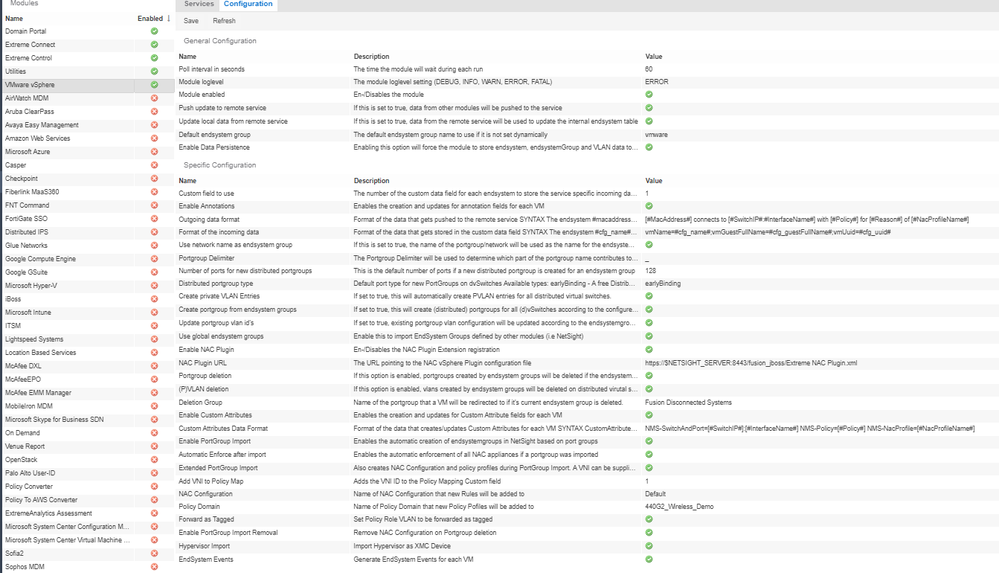
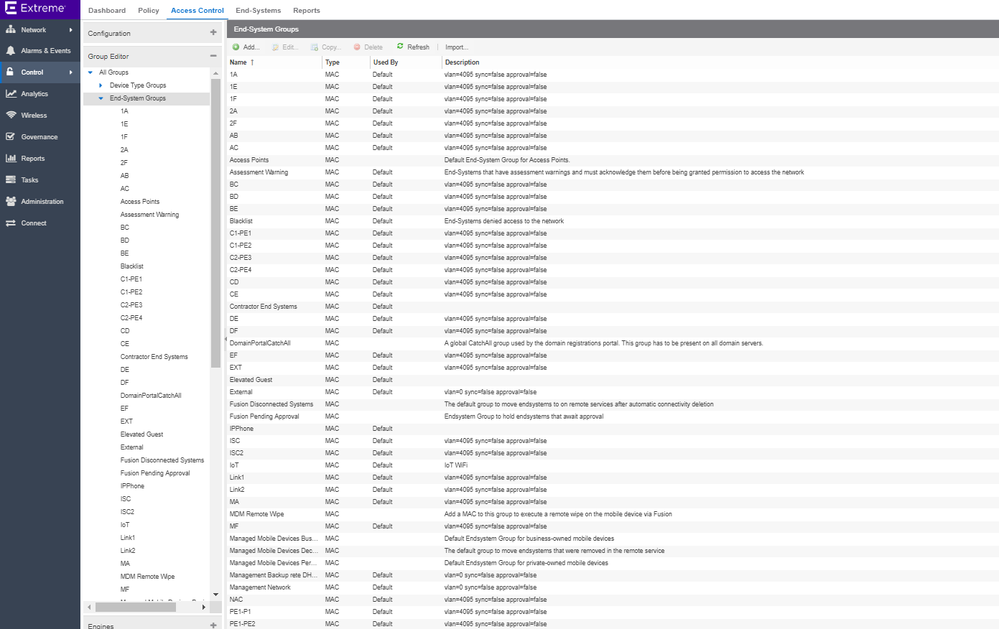
In my demolab based on demokit, I've configured the ExtremeConnect as follow
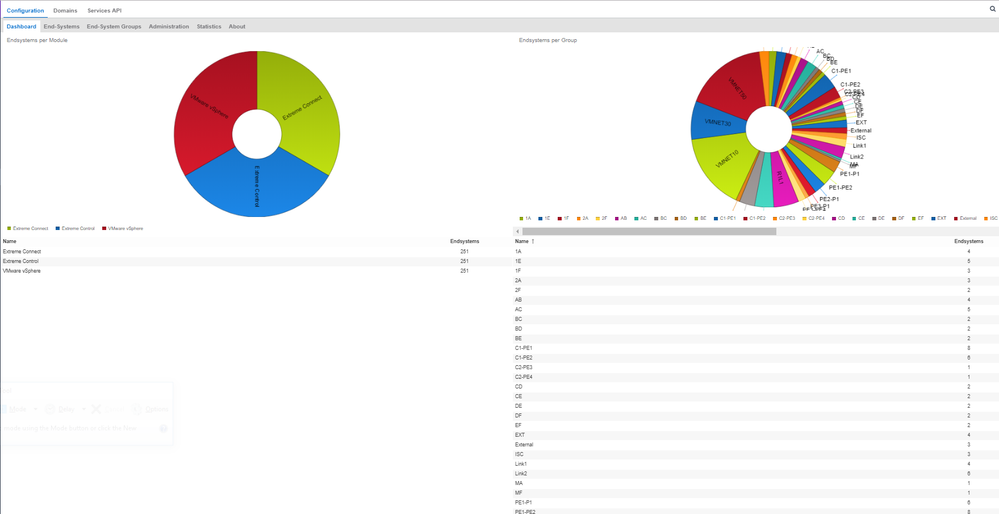
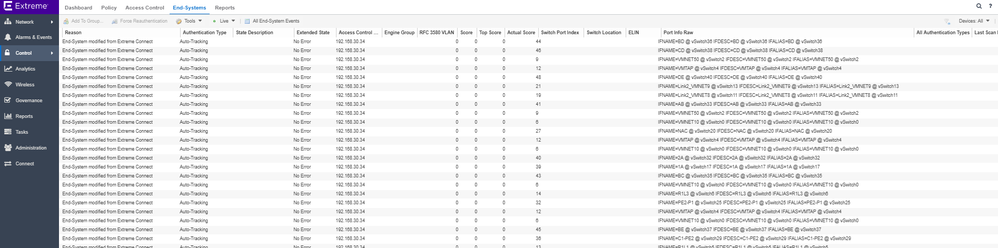
And I have the following viw in the dashboard:
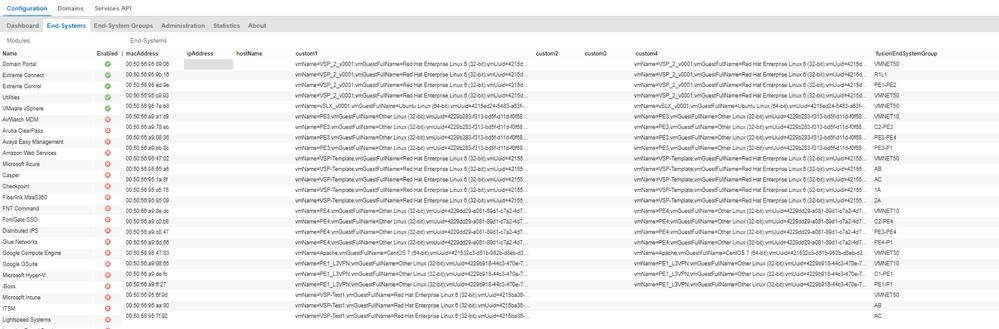
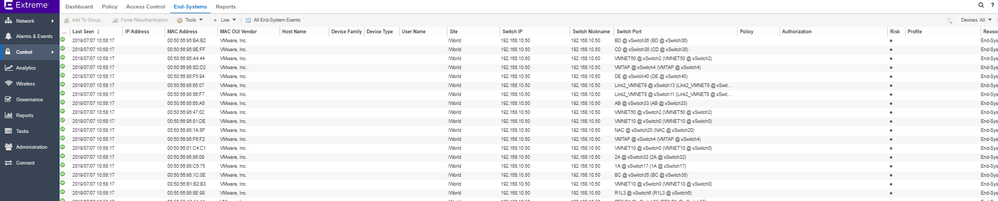
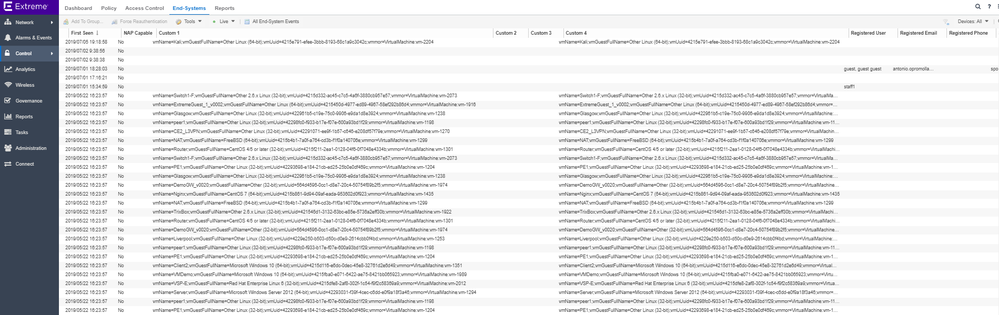
and the end-systems of my vmware host:
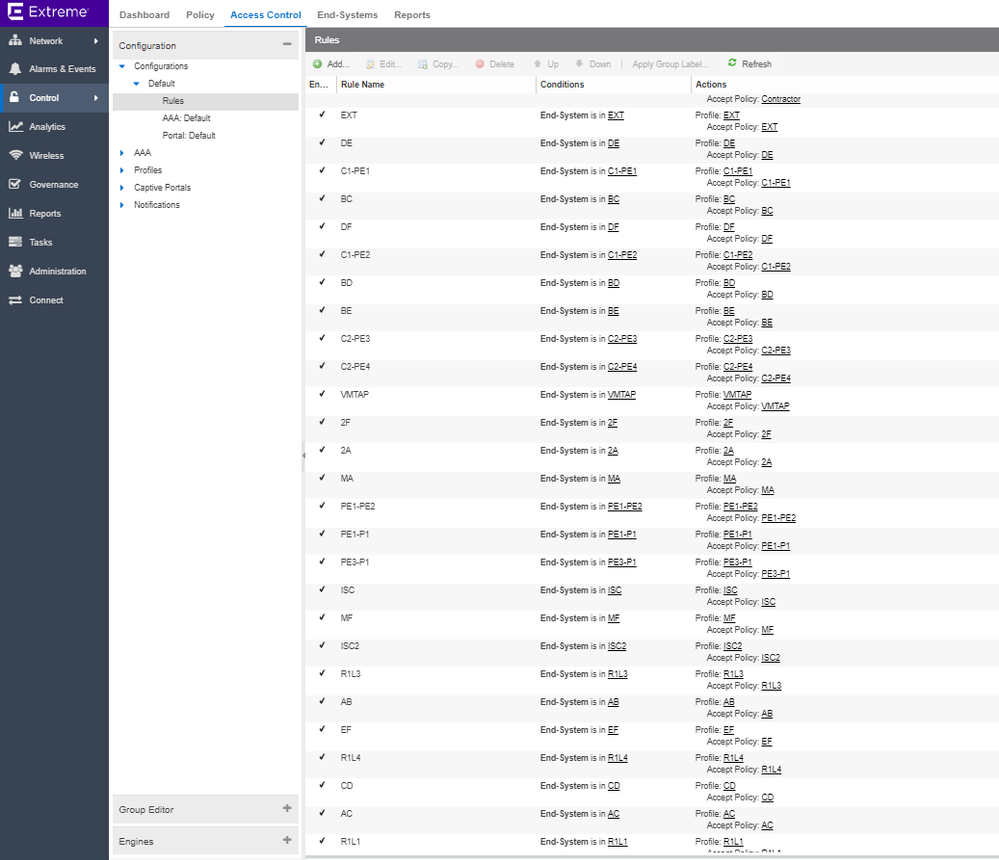
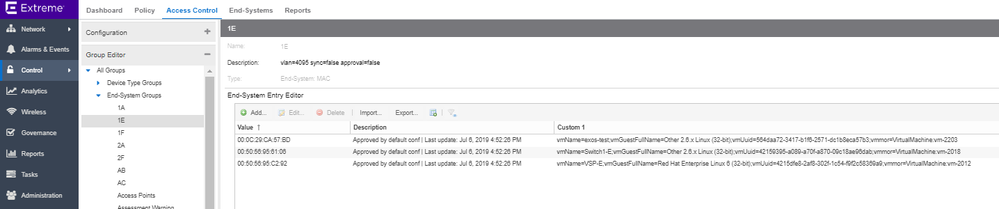
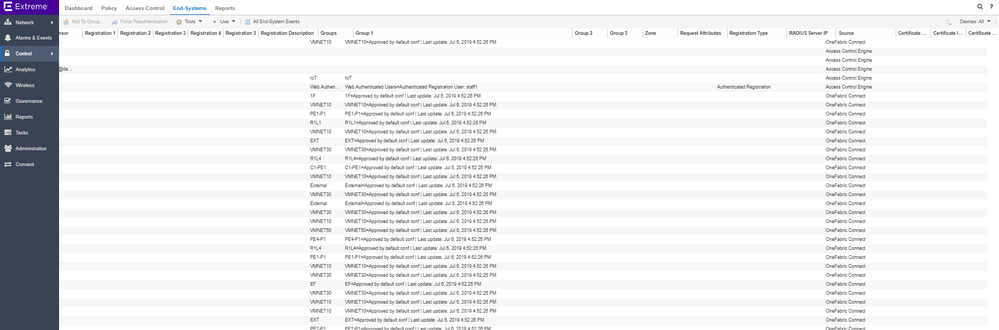
Based on the configuration made in my ExtremeConnect module for vsphere, in ExtremControl I've got now the following new rules, profiles, end-systems groups, automatically created from the ExtremeConnect module:
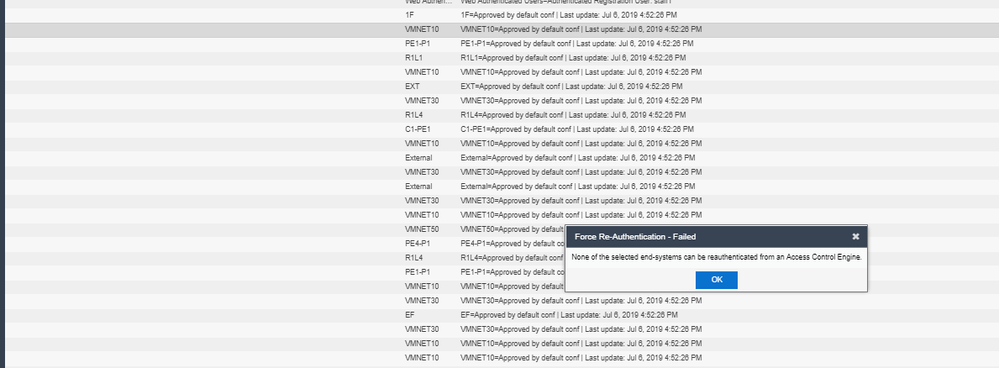
All these ed-systems have authentication set to Auto Tracking and I can't change anything. If for example I try to add an end-system in a different group, I have the following error:
The new authomatic rules are never matched in Access Control.
How can have control of the VM authentication in manner to build my own rules for the VM?
In my demolab based on demokit, I've configured the ExtremeConnect as follow
And I have the following viw in the dashboard:
and the end-systems of my vmware host:
Based on the configuration made in my ExtremeConnect module for vsphere, in ExtremControl I've got now the following new rules, profiles, end-systems groups, automatically created from the ExtremeConnect module:
All these ed-systems have authentication set to Auto Tracking and I can't change anything. If for example I try to add an end-system in a different group, I have the following error:
The new authomatic rules are never matched in Access Control.
How can have control of the VM authentication in manner to build my own rules for the VM?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-03-2019 11:16 AM
It's possible to integrate ESXi / vSphere with XMC and use ExtremeControl to authorize the VMs / users.
You integrate it with the ExtremeConnect module of XMC (part of Advanced version) and use NAC in conjunction with Policy Framework.
Kind regards
Christoph
You integrate it with the ExtremeConnect module of XMC (part of Advanced version) and use NAC in conjunction with Policy Framework.
Kind regards
Christoph