This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (General)
- RE: NAC EAP-TLS + Microsoft PKI - custom subject/c...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NAC EAP-TLS + Microsoft PKI - custom subject/common name not possible
NAC EAP-TLS + Microsoft PKI - custom subject/common name not possible
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-20-2018 08:41 AM
We have a working setup with Netsight/NAC + Microsoft Windows PKI 2012 R2
Our Clients get Certificates with Auto Enrollment, which they use to authenticate in the network.
Additionally we use LDAP User Groups to put the Clients into different Networks -> UserVLAN, AdminVLAN, InternetVLAN etc.
This works great, but we noticed a problem.
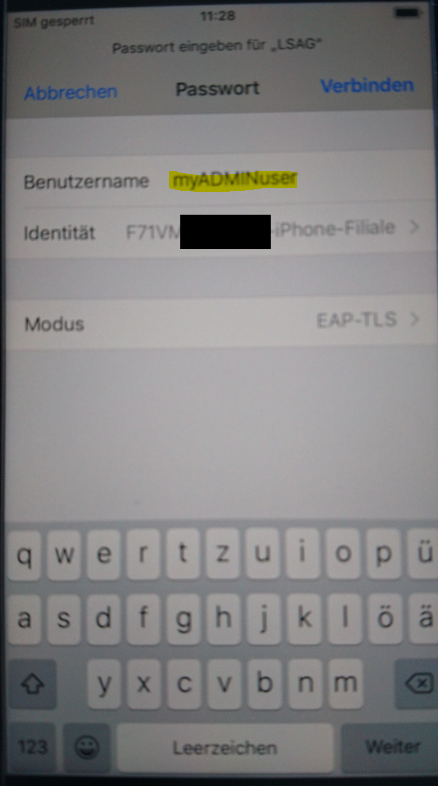
When using a non Windows Device it is possible to set a different Username/Identity that is sent to the Authentication Server.
This can be used to get into a different network than supposed to, if the Username/Identy is valid (eg. Admin)
In another area we used RADIUS User Group to seperate those client families, but this is not possible here because in the certificate from User and Admin there is nothing different than the hostname.
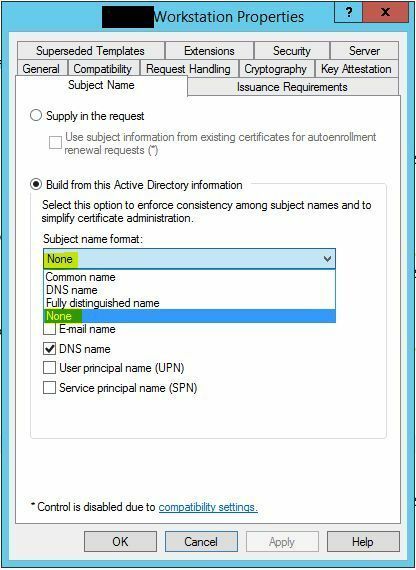
We thought of writing something in the Subject/common name of the Certificate/Template in the PKI. But we don't know how this can be achieved since there is no possibility to write CUSTOM Information.
Any MCSE knows how to deal with that? 😉
Our Clients get Certificates with Auto Enrollment, which they use to authenticate in the network.
Additionally we use LDAP User Groups to put the Clients into different Networks -> UserVLAN, AdminVLAN, InternetVLAN etc.
This works great, but we noticed a problem.
When using a non Windows Device it is possible to set a different Username/Identity that is sent to the Authentication Server.
This can be used to get into a different network than supposed to, if the Username/Identy is valid (eg. Admin)
In another area we used RADIUS User Group to seperate those client families, but this is not possible here because in the certificate from User and Admin there is nothing different than the hostname.
We thought of writing something in the Subject/common name of the Certificate/Template in the PKI. But we don't know how this can be achieved since there is no possibility to write CUSTOM Information.
Any MCSE knows how to deal with that? 😉
11 REPLIES 11
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-20-2018 10:31 AM
Hello Anton,
if you can write differen SANs (subject alt name) in the certificate you can use this as criteria.
If you can't do this with your certificate template on the Windows CA you can create a new template (enterprise server needed!) with SAN as attribute.
If this is not possible. You export the serial from Windows CA and import again in the NAC I think.
But therefore you have to dig deeper into the Windows Certificate command line.
if you can write differen SANs (subject alt name) in the certificate you can use this as criteria.
If you can't do this with your certificate template on the Windows CA you can create a new template (enterprise server needed!) with SAN as attribute.
If this is not possible. You export the serial from Windows CA and import again in the NAC I think.
But therefore you have to dig deeper into the Windows Certificate command line.
Regards
Stephan
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-20-2018 10:15 AM
hy stephan,
i know that article. we also used TLS-fields in RADIUS User Groups for other devices/areas
but in that case there is no TLS-field we can use, because the certificates are mostly the same.
except hostname/dns name, but i cannot build a rule from that
for example hostname1 is ADMIN hostname2 is USER
i thought to write in the subject of ther certificate hostname1-ADMIN so I can make a RADIUS User Group *-Admin
i know that article. we also used TLS-fields in RADIUS User Groups for other devices/areas
but in that case there is no TLS-field we can use, because the certificates are mostly the same.
except hostname/dns name, but i cannot build a rule from that
for example hostname1 is ADMIN hostname2 is USER
i thought to write in the subject of ther certificate hostname1-ADMIN so I can make a RADIUS User Group *-Admin
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-20-2018 10:09 AM
Anton,
if you need the CN as username read that:
https://gtacknowledge.extremenetworks.com/articles/How_To/Configure-NAC-To-Use-The-TLS-Client-Certif...
Best regards
Stephan
if you need the CN as username read that:
https://gtacknowledge.extremenetworks.com/articles/How_To/Configure-NAC-To-Use-The-TLS-Client-Certif...
Best regards
Stephan
Regards
Stephan
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-20-2018 10:05 AM
Hello Anton,
I think that article should help:
https://gtacknowledge.extremenetworks.com/articles/Solution/Using-TLS-Certificate-fields-for-authent...
Best regards
Stephan
I think that article should help:
https://gtacknowledge.extremenetworks.com/articles/Solution/Using-TLS-Certificate-fields-for-authent...
Best regards
Stephan
Regards
Stephan
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-20-2018 09:15 AM
I am not familure with Netsight, but on Identity Engines this could be written as part of the Authorization rule I believe.