- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (General)
- Using TLS Certificate fields for authentication ma...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Using TLS Certificate fields for authentication mapping
Using TLS Certificate fields for authentication mapping
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-08-2018 08:08 PM
Hello,
can I use TLS certificate fields like "TLS-Cert-Issuer" or "TLS-Cert-Common-Name" (or other fields mentioned here: https://extremeportal.force.com/ExtrArticleDetail?an=000064090) to do the authentication mapping in the NAC AAA configuration to e. g. switch between local authentication or proxy radius if I use 802.1x?
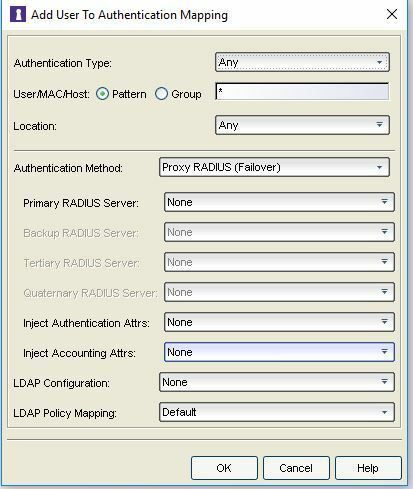
If yes, how can I do set? What do I have to enter in the fields (User/MAC/Host)?
Best regards
Stephan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-20-2018 01:31 PM
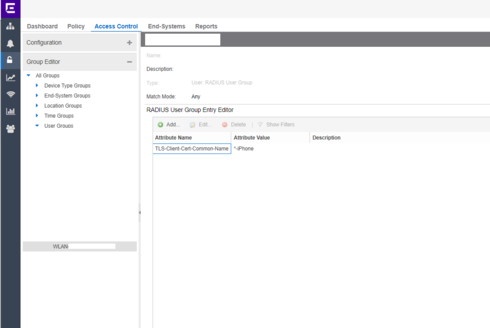
I can only show a screenshot in OneView.
You can make a User Group and Change it to RADIUS User Group, then you can rely on TLS Attributes.
We did it with TLS-Client-Cert-Common-Name, but others should also be possible.
Does anyone has a list of which attributes are possible?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-20-2018 01:31 PM
you will see the attributes in the KB article following the link in my first text above.
Best regards
Stephan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-12-2018 03:29 AM
the decision to proxy or not can be made based on Location (Switch, Port, SSID, AP, Zone), based on username (pattern or group membership, in case of certificates the name is CN), based on authentication type.
I suggest to terminate EAP-TLS locally and add more CA and more CRL to your configuration. The Access Control Engine can authorize based on more CA.
Regards
Z.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-12-2018 03:29 AM