This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (Identifi)
- RE: IdentiFi; Is there a way to Block MU to MU tra...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IdentiFi; Is there a way to Block MU to MU traffic with B@AP in the same Virtual Network or Wlan Services?
IdentiFi; Is there a way to Block MU to MU traffic with B@AP in the same Virtual Network or Wlan Services?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-16-2015 08:46 AM
We are installing a new Identify installation for a customer with several locations, ( +/- 200)
the Wlan on the remote locations are going to use by Employees and customers. because of the expensive WAN connections we want that the customers are the internet connections on the remote site, so we configure B@AP. And we also want to block the customer mobile unit to mobile unit traffic.
Is there a way to block MU to MU traffic at the AP?
Thank you for your help
Rien van Maurik
the Wlan on the remote locations are going to use by Employees and customers. because of the expensive WAN connections we want that the customers are the internet connections on the remote site, so we configure B@AP. And we also want to block the customer mobile unit to mobile unit traffic.
Is there a way to block MU to MU traffic at the AP?
Thank you for your help
Rien van Maurik
8 REPLIES 8
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-16-2015 11:46 AM
Hi Hartmut
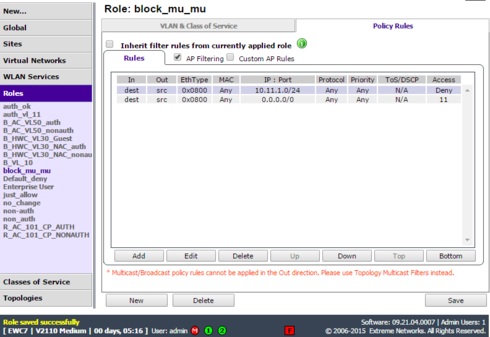
Sure, in its simplest form, here is my lab rule:
I know the article says to allow to the subnets default gateway but I don't see a reason to do that, generally traffic is passing through the default gateway, not directly to it.
I just tested the above in my lab and it works.
-Gareth
Sure, in its simplest form, here is my lab rule:
I know the article says to allow to the subnets default gateway but I don't see a reason to do that, generally traffic is passing through the default gateway, not directly to it.
I just tested the above in my lab and it works.
-Gareth
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-16-2015 11:46 AM
The DNS is in another subnet. But you are right, i should add DNS and DHCP, too.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-16-2015 11:46 AM
Is your DNS server in the same IP range as your clients? The deny might have blocked DNS traffic. I usually allow DNS, DHCP server and client ports first, then start blocking local subnets in the rule sequence.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-16-2015 11:46 AM
Hello Garath,
could you please post an example of this solution? It tried to configure it, but after adding the second rule to deny MU-to-MU traffic communication to the internet stopped working, to.
Could post a screenshot for this or a compareable example: client subnet 192.168.100.0/24 and gateway 192.168.100.254.
Best Regards
Hartmut
could you please post an example of this solution? It tried to configure it, but after adding the second rule to deny MU-to-MU traffic communication to the internet stopped working, to.
Could post a screenshot for this or a compareable example: client subnet 192.168.100.0/24 and gateway 192.168.100.254.
Best Regards
Hartmut