This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (WiNG)
- RE: How does WiNG Captive Portal (RADIUS) authenti...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How does WiNG Captive Portal (RADIUS) authentication work with locally bridged (self) mode and external captive portal web pages?
How does WiNG Captive Portal (RADIUS) authentication work with locally bridged (self) mode and external captive portal web pages?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-02-2017 06:57 PM
I'm operating a WiNG wireless controller to manage remote APs. I'm attempting to setup external captive portal pages, and in order to have the APs handle the captive portal capture and redirection process (and RADIUS authentication) without tunneling traffic through the controller.
So far, the setup works as expected, clients are getting redirected to the proper captive portal page by the AP.
The first question is, once the external pages perform their auth processes,
1) How does the authentication form submission work on the AP (or does it) in this configuration?
I'm currently testing form submission (POST) with these two endpoints:
https://1.1.1.1:444/cgi-bin/hslogin.cgi
http://1.1.1.1:880/cgi-bin/hslogin.cgi
and these parameters:
f_user =
f_pass =
f_Qv =
f_hs_server = 1.1.1.1
2) Is the script at 1.1.1.1 served by the AP, or is that supposed to supposed to be the controller?
3) Can I post to 880 when in http redirection mode and https mode or at all?
So far, the setup works as expected, clients are getting redirected to the proper captive portal page by the AP.
The first question is, once the external pages perform their auth processes,
1) How does the authentication form submission work on the AP (or does it) in this configuration?
I'm currently testing form submission (POST) with these two endpoints:
https://1.1.1.1:444/cgi-bin/hslogin.cgi
http://1.1.1.1:880/cgi-bin/hslogin.cgi
and these parameters:
f_user =
f_pass =
f_Qv =
f_hs_server = 1.1.1.1
2) Is the script at 1.1.1.1 served by the AP, or is that supposed to supposed to be the controller?
3) Can I post to 880 when in http redirection mode and https mode or at all?
17 REPLIES 17
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-06-2017 09:33 AM
Hi Jeff,
now couple of questions - the external page shall provide authentication / registration, right?
Are you using simple credentials authentication of full registration there?
Either or - you shall use RADIUS server / AAA policy for that also - either external or internal.
Captive portal, actually the AAA, rely on access-accept / reject to react as default option is "access-type radius".
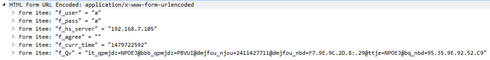
When using external portals we do expect getting response similar to attached picture
Be careful to abide sequence of f_user, f_pass, f_hs_server, f_curr_time and f_Qv - hslogin.cgi is little touchy here 🙂
I would strongly recommend to get some captures from controller using these two commands in CLI:
- remote-debug captive-portal hosts CP1 clients all max-events 5000 events all
- remote-debug wireless hosts CP2 clients all max-events 5000 events all
Here CP1 is device running captive portal service and CP2 is AP where test client connects.
Try to connect and browse with unauthenticated client and I'll tell you more having these.
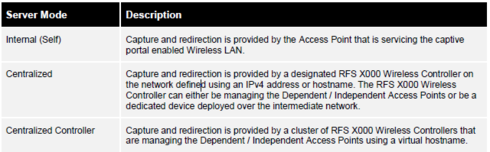
Also - server modes explained here
Regards,
Ondrej
now couple of questions - the external page shall provide authentication / registration, right?
Are you using simple credentials authentication of full registration there?
Either or - you shall use RADIUS server / AAA policy for that also - either external or internal.
Captive portal, actually the AAA, rely on access-accept / reject to react as default option is "access-type radius".
When using external portals we do expect getting response similar to attached picture
Be careful to abide sequence of f_user, f_pass, f_hs_server, f_curr_time and f_Qv - hslogin.cgi is little touchy here 🙂
I would strongly recommend to get some captures from controller using these two commands in CLI:
- remote-debug captive-portal hosts CP1 clients all max-events 5000 events all
- remote-debug wireless hosts CP2 clients all max-events 5000 events all
Here CP1 is device running captive portal service and CP2 is AP where test client connects.
Try to connect and browse with unauthenticated client and I'll tell you more having these.
Also - server modes explained here
Regards,
Ondrej
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-03-2017 05:13 PM
captive-portal CP-TEST inactivity-timeout 3600 server mode self webpage-location external webpage external login http://example.com/login webpage external welcome http://example.com/welcome webpage external fail http://example.com/failed webpage external no-service http://www.tide.com use aaa-policy CP-RADIUS use dns-whitelist CP-WHITELIST dns-whitelist CP-WHITELIST permit example.com permit someservice.com suffix wlan testwifinetwork vlan 680 bridging-mode local encryption-type none authentication-type none no answer-broadcast-probes radius vlan-assignment data-rates 2.4GHz gn use aaa-policy CP-RADIUS use captive-portal CP-TEST captive-portal-enforcement enforce-dhcp proxy-arp-mode strict broadcast-dhcp validate-offer service cred-cache clear-on-disconnect
Ondrej,
Here's what the config looks like...
We should be able to authenticate by POSTing credentials and the redirect token (from the WiNG captive portal guide example login.html) to:
https://1.1.1.1:444/cgi-bin/hslogin.cgi
or
http://1.1.1.1:880/cgi-bin/hslogin.cgi
And then, in this case, the AP would handle authentication with the RADIUS server using the parameters supplied, is that right?
Regarding other server modes, I was under the assumption that if we weren't using 'centralized' mode the server host would have to be a controller, is that not the case?
Thanks,
Jeff
Ondrej,
Here's what the config looks like...
We should be able to authenticate by POSTing credentials and the redirect token (from the WiNG captive portal guide example login.html) to:
https://1.1.1.1:444/cgi-bin/hslogin.cgi
or
http://1.1.1.1:880/cgi-bin/hslogin.cgi
And then, in this case, the AP would handle authentication with the RADIUS server using the parameters supplied, is that right?
Regarding other server modes, I was under the assumption that if we weren't using 'centralized' mode the server host would have to be a controller, is that not the case?
Thanks,
Jeff
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-03-2017 08:52 AM
Hi Jeff,
the thing is that with CP we need to redirect client's flow to a certain end-point (walled garden) so in case you do not specify a server (or use served mode self) AP acts as one - virtual IP 1.1.1.1.
Anyway, in case of external pages and local CP server you create kind of a Supplicant - Authenticator - Authentication Server scenario, when AP acts as authenticator and tunnels auth request to external pages..
Also, you can only select HTTP or HTTPS in CP - no special port redirection afaik.
If you have a specific config to discuss, please share it or raise a support case.
There is not-yet re-branded captive portal desing guide I would not like to post here.
Regards,
Ondrej
the thing is that with CP we need to redirect client's flow to a certain end-point (walled garden) so in case you do not specify a server (or use served mode self) AP acts as one - virtual IP 1.1.1.1.
Anyway, in case of external pages and local CP server you create kind of a Supplicant - Authenticator - Authentication Server scenario, when AP acts as authenticator and tunnels auth request to external pages..
Also, you can only select HTTP or HTTPS in CP - no special port redirection afaik.
If you have a specific config to discuss, please share it or raise a support case.
There is not-yet re-branded captive portal desing guide I would not like to post here.
Regards,
Ondrej