This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (WiNG)
- RE: KRACK attack on WPA2
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
KRACK attack on WPA2
KRACK attack on WPA2
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-16-2017 04:47 AM
Hello everyone,
I have some questions due to the expected disclosure today on the attack possible on WPA2 SSIDs.
Link: https://arstechnica.com/information-technology/2017/10/severe-flaw-in-wpa2-protocol-leaves-wi-fi-tra...
- Is Extreme aware of this?
- Are Fixes ready to be released?
- Is a software fix sufficient or does hardware need to be replaced?
Thanks and best regards,
Johannes
I have some questions due to the expected disclosure today on the attack possible on WPA2 SSIDs.
US-CERT has become aware of several key management vulnerabilities in the 4-way handshake of the Wi-Fi Protected Access II (WPA2) security protocol. The impact of exploiting these vulnerabilities includes decryption, packet replay, TCP connection hijacking, HTTP content injection, and others. Note that as protocol-level issues, most or all correct implementations of the standard will be affected. The CERT/CC and the reporting researcher KU Leuven, will be publicly disclosing these vulnerabilities on 16 October 2017.
Link: https://arstechnica.com/information-technology/2017/10/severe-flaw-in-wpa2-protocol-leaves-wi-fi-tra...
- Is Extreme aware of this?
- Are Fixes ready to be released?
- Is a software fix sufficient or does hardware need to be replaced?
Thanks and best regards,
Johannes
82 REPLIES 82
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-26-2017 12:48 AM
Hi Guys, independently of the above mentioned, I also decided to perform a full testing of the provided images with positive results for both 5.8.6.7-002R and 5.9.0.2-001R. Images for AP6532 also work for AP650, images for AP6522 work for AP622 as well as the AP6521 images work for AP621. Of course this is also the case with AP75xx platforms using only 1 image (7522,7532,7562). For AP platforms, if something goes wrong, there is always a possibility to directly upgrade the firmware via console/ssh with the available images (of course for individual AP's not on a larger scale)...So, in the end, good thing, the differences in written statements in both Release Notes and here on portal play for us and our customers Have a nice weekend and good sleep everyone, The only looser here seems to be the RFS7000.. but in the end, this can be easily replaced by RFS6000 or VX9000 if the implementation scenario allows that (tunelled vs localy bridged wlans, etc.).
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-26-2017 12:48 AM
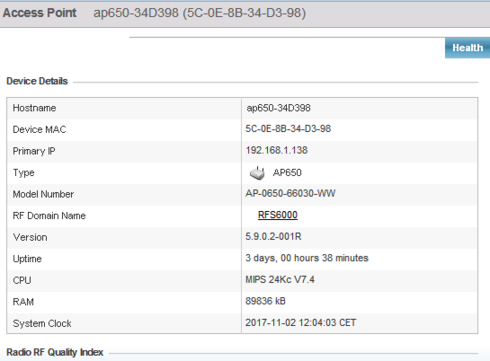
For Kees ,
never forget that AP650 is quite an AP0632 as it should works same way..
an image is better tahn words or claiming :
never forget that AP650 is quite an AP0632 as it should works same way..
an image is better tahn words or claiming :
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-26-2017 12:48 AM
Hi Geovane,
Forget to update one more thing to you.
802.11r and broadcast key rotation for WPA2/CCMP WLANs are disabled (disabled by default on WiNG 5). Both settings are within the WLAN configuration (broadcast key rotation is under WLAN/Security and 802.11r/Fast BSS Transition is under WLAN/Advanced).
It means
WING-36014 WPA2 KRACK: 802.11r FT Handshake vulnerability (CVE-2017-13082) WING-36016 WPA2 KRACK: MCX PSK 4-way key updated to avoid WPA2 KRACK vulnerability.
Best regards,
Bin
Forget to update one more thing to you.
802.11r and broadcast key rotation for WPA2/CCMP WLANs are disabled (disabled by default on WiNG 5). Both settings are within the WLAN configuration (broadcast key rotation is under WLAN/Security and 802.11r/Fast BSS Transition is under WLAN/Advanced).
It means
- disable broadcast key rotation to migrate WING-36013
- disable 802.11r to migrate WING-36014
- disable MeshConnx to migrate WING-36016
WING-36014 WPA2 KRACK: 802.11r FT Handshake vulnerability (CVE-2017-13082) WING-36016 WPA2 KRACK: MCX PSK 4-way key updated to avoid WPA2 KRACK vulnerability.
Best regards,
Bin
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-26-2017 12:48 AM
Hello Geovane,
Very understand your request. Please contact our local sale team and let them know your and our customer's concern. Our sale team may help you push our engineer team to develop the new patch for RFS7000.
At this moment, I did not have any information to say that we will provide extending support for RFS7000. Very sorry about that.
Best regards,
Bin
Very understand your request. Please contact our local sale team and let them know your and our customer's concern. Our sale team may help you push our engineer team to develop the new patch for RFS7000.
At this moment, I did not have any information to say that we will provide extending support for RFS7000. Very sorry about that.
Best regards,
Bin
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-26-2017 12:48 AM
Thanks for the tip, Pierre, but according to the release notes of the versions the AP650 is EOL and end of engineering.
Are you using any of these versions with the AP650?
Are you using any of these versions with the AP650?