This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (WiNG)
- WiNG captive portal re-authentication timeout
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
WiNG captive portal re-authentication timeout
WiNG captive portal re-authentication timeout
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-15-2017 11:37 AM
Hi, I have setup a captive portal on a VX9000 and I noticed that every day the user has to re-enter the username and password. Is there a way to remain authenticated for as long as the user is valid? Also is there a way to un-authorize a certain user from the captive portal?
13 REPLIES 13
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-20-2017 10:01 AM
Hi Ondrej, Thank you for your detailed answer and testing. Really helpful information, good job! My use case is site visitors that are being handed out pre-printed vouchers with username/passwords in order to authenticate and being able to access the WLAN, so there is no previous knowledge of the MAC address, hence the first fork does not fit, please correct me if i am wrong. About the second fork, I can not download the document because it takes my to your sharepoint cloud server. So I need your aid with the following: 1. Does self registration allow anyone to access the WLAN? (That would be a problem in this case) 2. Is it possible to provide a username/password (CP) and then the user enter his own mac (AAA)? If the second is possible then the inactivity timeout of the RADIUS holding MAC addresses, would not be a problem since it happens automatically.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-20-2017 10:01 AM
Hi Konstantinos,
I setup scenario with AP adopted to a controller when AP had Captive Portal service and controller ran RADIUS service.
Captive Portal configuration as follows:
captive-portal RADIUS
access-time 10
inactivity-timeout 60
simultaneous-users 1
use aaa-policy RADIUS
bypass captive-portal-detection
WLAN configuration as follows:
wlan RADIUS
bridging-mode local
encryption-type none
authentication-type mac
use aaa-policy RADIUS
use captive-portal RADIUS
captive-portal-enforcement fall-back
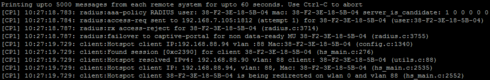
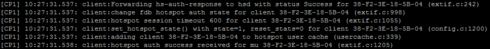
Then connecting to SSID I see in logs that system first tries to authenticate client against AAA / RADIUS and then failover to Captive Portal
Then successful authentication via Captive Portal pages against same RADIUS server
So in theory this will work fine as you see first attempt goes to RADIUS.
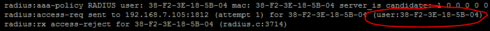
You might noticed a problem though - AAA policy asks to authenticate user 38-F2-3E-18-5B-04
This is result of having authentication method MAC.
So here we go with a fork:
Regards,
Ondrej
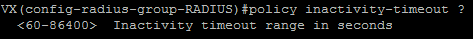
EDIT: Just checked RADIUS group policy for timeout options and I have some bad news - it is also limited to 86400 seconds
However RFC2865 does specify its maximum as 32-bit integer, we have limitation for a day in WiNG
I setup scenario with AP adopted to a controller when AP had Captive Portal service and controller ran RADIUS service.
Captive Portal configuration as follows:
captive-portal RADIUS
access-time 10
inactivity-timeout 60
simultaneous-users 1
use aaa-policy RADIUS
bypass captive-portal-detection
WLAN configuration as follows:
wlan RADIUS
bridging-mode local
encryption-type none
authentication-type mac
use aaa-policy RADIUS
use captive-portal RADIUS
captive-portal-enforcement fall-back
Then connecting to SSID I see in logs that system first tries to authenticate client against AAA / RADIUS and then failover to Captive Portal
Then successful authentication via Captive Portal pages against same RADIUS server
So in theory this will work fine as you see first attempt goes to RADIUS.
You might noticed a problem though - AAA policy asks to authenticate user 38-F2-3E-18-5B-04
This is result of having authentication method MAC.
So here we go with a fork:
- either you have to create a user database based on clients' MAC addresses instead of username and password
- or you will use Captive portal guest registration based on your VX-9000
Regards,
Ondrej
EDIT: Just checked RADIUS group policy for timeout options and I have some bad news - it is also limited to 86400 seconds
However RFC2865 does specify its maximum as 32-bit integer, we have limitation for a day in WiNG
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-20-2017 10:01 AM
Hi Ondrej, Did you have a chance to test this?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-20-2017 10:01 AM
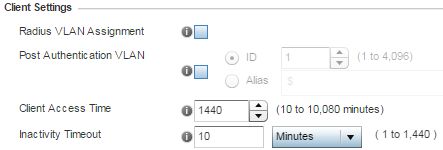
It is the inactivity timeout the value in question that is limited to 1 Day (1440minutes). The above numbers are both the same in 5.8.4. (inactivity timeout & Client Access time)
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-20-2017 10:01 AM
Theoretically speaking it shall pass automatically with first CP authentication - then it relies on RADIUS authentication timeout.
Let me test it to get it confirmed.
EDIT: In WiNG 5.8.5 I see the access time is extended to max 10080 minutes / 7 days.
Let me test it to get it confirmed.
EDIT: In WiNG 5.8.5 I see the access time is extended to max 10080 minutes / 7 days.