This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Technical Discussions
- Network Architecture & Design
- A-Series Switch VLAN Configuration
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
A-Series Switch VLAN Configuration
A-Series Switch VLAN Configuration
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-20-2015 12:53 AM
Hi,
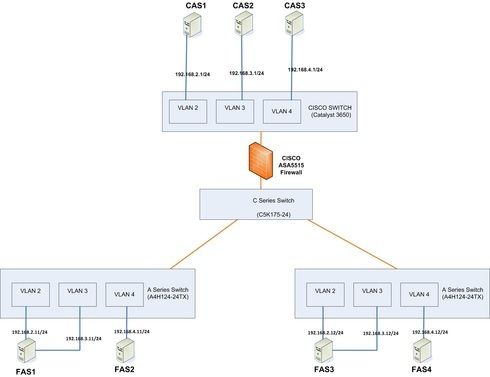
I have some queries on configuring VLAN on our network having the combination of Enterasys A series & C5 series switches which is connected to CISCO 3650 via CISCO ASA Firewall
(Refer the below schematic network diagram)
We need to create VLAN2,3,4 for Enterasys A- Series Switch which connects the computer FAS1,FAS2 & FAS3 with IP range 192.168.2.11/24,192.168.3.11/24&192.168.4.11/24 respectively.
VLAN2 connected computers on A- Series switch need to connect the servers on VLAN2 of CISCO 3650 switch .
Similarly VLAN3 on A - Series switch will able to connect servers on VLAN3 of CISCO 3650
VLAN4 on A - Series switch will able to connect servers on VLAN4 of CISCO 3650
What are all the configuration need to be done on A, C5 series switches & CISCO 3650 , firewalls to meet the requirements.
I have some queries on configuring VLAN on our network having the combination of Enterasys A series & C5 series switches which is connected to CISCO 3650 via CISCO ASA Firewall
(Refer the below schematic network diagram)
We need to create VLAN2,3,4 for Enterasys A- Series Switch which connects the computer FAS1,FAS2 & FAS3 with IP range 192.168.2.11/24,192.168.3.11/24&192.168.4.11/24 respectively.
VLAN2 connected computers on A- Series switch need to connect the servers on VLAN2 of CISCO 3650 switch .
Similarly VLAN3 on A - Series switch will able to connect servers on VLAN3 of CISCO 3650
VLAN4 on A - Series switch will able to connect servers on VLAN4 of CISCO 3650
What are all the configuration need to be done on A, C5 series switches & CISCO 3650 , firewalls to meet the requirements.
3 REPLIES 3
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-20-2015 03:22 PM
Per the Pluggable Transceivers datasheet, the C5-Series is compatible with the MGBIC-02, which is a 1-gigabit-only RJ45 SFP transceiver with a reach of 100 meters.
So yes, in theory one could use a copper SFP transceiver on a C5 switch to connect to one of the ASA 5515-X's gigabit ethernet ports.
On the other hand, on the C5G124-24/48(P2) and C5K125-24/48(P2) it would be simpler and more economical to use one of its native front-panel 10/100/1000 RJ45 ports instead of installing a MGBIC-02. In considering this I haven't yet hit upon a scenario in which it would make good sense to use other than a native port for a copper connection.
So yes, in theory one could use a copper SFP transceiver on a C5 switch to connect to one of the ASA 5515-X's gigabit ethernet ports.
On the other hand, on the C5G124-24/48(P2) and C5K125-24/48(P2) it would be simpler and more economical to use one of its native front-panel 10/100/1000 RJ45 ports instead of installing a MGBIC-02. In considering this I haven't yet hit upon a scenario in which it would make good sense to use other than a native port for a copper connection.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-20-2015 03:50 AM
Hi Jeremy Gibbs,
Thanks for you quick reply.. Now we got idea how to proceed with VLAN configuration to meet the requirements.
I have one more question on connecting C5 series switch to CISCO ASA 5515-X Firewall.
We bought ASA 5515-X Firewall (6GE - Data + 1GE - Mgmt configuration).
How we can connect C5 series to Firewall ?
Can we use copper SFP transceivers on C5 switch and then connect to firewall?
Thanks for you quick reply.. Now we got idea how to proceed with VLAN configuration to meet the requirements.
I have one more question on connecting C5 series switch to CISCO ASA 5515-X Firewall.
We bought ASA 5515-X Firewall (6GE - Data + 1GE - Mgmt configuration).
How we can connect C5 series to Firewall ?
Can we use copper SFP transceivers on C5 switch and then connect to firewall?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-20-2015 01:52 AM
First
Create your vlans on the C series. Assign the IP addresses and subnet masks to the L3 interface
Next, the uplink port to the A4 from the C5
set vlan egress 2,3,4 ge.1.1 tagged
From the A4 to the C5
(first run (set vlan create 2,3,4))
set vlan egress 2,3,4 fe.1.1 tagged
Do the same for other uplink port to the other A4 and so on. You are tagging the port all the way through. Cisco would call this a trunk.
I am assuming you are doing passtrough firewalling on the ASA. So the uplink port to the ASA from the C5
set vlan egress 2,3,4 ge.1.2 tagged
On the cisco firewall you might need to create subinterfaces for each of the VLANS and turn on intra-interface and inter-interface routing:
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
Then tag each of the subinterfaces and put them in the same sercuity group.
Then on the other side (Cisco)
int gig 0/1
switchport mode trunk
For the access ports
int gig 0/4
switchport access vlan 4
etc...
Create your vlans on the C series. Assign the IP addresses and subnet masks to the L3 interface
Next, the uplink port to the A4 from the C5
set vlan egress 2,3,4 ge.1.1 tagged
From the A4 to the C5
(first run (set vlan create 2,3,4))
set vlan egress 2,3,4 fe.1.1 tagged
Do the same for other uplink port to the other A4 and so on. You are tagging the port all the way through. Cisco would call this a trunk.
I am assuming you are doing passtrough firewalling on the ASA. So the uplink port to the ASA from the C5
set vlan egress 2,3,4 ge.1.2 tagged
On the cisco firewall you might need to create subinterfaces for each of the VLANS and turn on intra-interface and inter-interface routing:
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
Then tag each of the subinterfaces and put them in the same sercuity group.
Then on the other side (Cisco)
int gig 0/1
switchport mode trunk
For the access ports
int gig 0/4
switchport access vlan 4
etc...