This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Technical Discussions
- Network Architecture & Design
- I need people from VLAN2 to access only one server...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
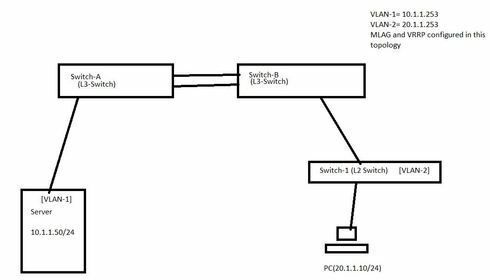
I need people from VLAN2 to access only one server on VLAN1, not all resources.
I need people from VLAN2 to access only one server on VLAN1, not all resources.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-22-2018 06:22 AM
I need people from VLAN2 to access only one server on VLAN1, not all resources, just one single server IP. Basically, I want to keep both networks isolated except for that server that should common to both.
6 REPLIES 6
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-23-2018 03:21 AM
I want to keep both networks (VLAN-1 and VLAN-2) isolated except for that server that should access via clients of VLAN-2 and other devices are not even accessible and pinging. now help to create ACL.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-22-2018 11:04 PM
Not perfect answer.
You could also use the idea of "VLAN Isolation"
https://documentation.extremenetworks.com/exos_16/EXOS_16_2/VLAN/c_vlan-isolation.shtml
Regards
You could also use the idea of "VLAN Isolation"
https://documentation.extremenetworks.com/exos_16/EXOS_16_2/VLAN/c_vlan-isolation.shtml
Regards
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-22-2018 11:48 AM
Hi,
This is an example :
BD-Lab.4 # show policy MS-VLAN-BRIDGE.pol
Policies at Policy Server:
Policy: MS-VLAN-BRIDGE
entry BRIDGE-TO-MS {
if match all {
source-address 10.32.32.0/23 ;
destination-address 10.32.0.0/21 ;
}
then {
permit ;
}
}
entry BRIDGE-to-BRIDGE {
if match all {
source-address 10.32.32.0/23 ;
destination-address 10.32.32.0/23 ;
}
then {
permit ;
}
}
You hav to create a policy first, then add to an ACL :
#
configure access-list MS-VLAN-BRIDGE vlan "Vlan-100" ingress
This is an example :
BD-Lab.4 # show policy MS-VLAN-BRIDGE.pol
Policies at Policy Server:
Policy: MS-VLAN-BRIDGE
entry BRIDGE-TO-MS {
if match all {
source-address 10.32.32.0/23 ;
destination-address 10.32.0.0/21 ;
}
then {
permit ;
}
}
entry BRIDGE-to-BRIDGE {
if match all {
source-address 10.32.32.0/23 ;
destination-address 10.32.32.0/23 ;
}
then {
permit ;
}
}
You hav to create a policy first, then add to an ACL :
#
configure access-list MS-VLAN-BRIDGE vlan "Vlan-100" ingress
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-22-2018 08:19 AM
is that a layer 2 vlan or layer 3? which device has ip adress on that network segment?
you should make a rule on that device, allowing/denying your traffic.
sometimes it is also possible to give that specific server a nic/ip from VLAN 2 - so you don't need to make exception rules.
it is up to you!
you should make a rule on that device, allowing/denying your traffic.
sometimes it is also possible to give that specific server a nic/ip from VLAN 2 - so you don't need to make exception rules.
it is up to you!