This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Technical Discussions
- Scripting
- Cisco - Extreme NAC integration -multiauthenticati...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco - Extreme NAC integration -multiauthentication, vlan, dot1x, mac
Cisco - Extreme NAC integration -multiauthentication, vlan, dot1x, mac
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-20-2015 10:40 AM
How to integrate cisco switches with Extreme NAC. You can pass vlan, acl's per user, authenticate mac or user even download acl's from NAC and even more - multiauthenticate up to 8 users on one cisco port...
7 REPLIES 7
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-20-2015 11:25 AM
Great job Tomasz,
I would alter the interface confic a little bit.
Your Config:
authentication order mab dot1x
authentication priority mab dot1x
My Config:
authentication order mab dot1x
authentication priority dot1x mab
Reason: If the dot1x authentication grants higher priveleges, I think they will not be enforced in your config.
Best Regards
Michael
I would alter the interface confic a little bit.
Your Config:
authentication order mab dot1x
authentication priority mab dot1x
My Config:
authentication order mab dot1x
authentication priority dot1x mab
Reason: If the dot1x authentication grants higher priveleges, I think they will not be enforced in your config.
Best Regards
Michael
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-20-2015 11:25 AM
It seems that extreme cut off my previous post... and that was not request for help but howto, anyway thanks Christoph 🙂
Below is full content of my post.
I'll try to show you how to integrate cisco switches with Extreme NAC. You can pass vlan, acl's per user, authenticate mac or user... even download acl's from NAC and even more - multiauthenticate up to 8 users on one cisco port...rate limit
! The first thing is to configure snmp access, you should see nice green circle in NMS after that.
snmp-server group V3Group v3 auth write myView
snmp-server group snmpgroup v3 auth read V3Read write V3Write
snmp-server group snmpgroup v3 priv
snmp-server view V3Read iso included
snmp-server view V3Write iso included
snmp-server community rw RW
snmp-server location DemoLab-1floor
snmp-server contact Your contact info
! dont forget create snmp user in your group with auth and priv credentials and proper security
! related to NMS profile:)
! snmp user ....
!Then we need to configure aaa radius server(s). Don't forget to check if you didn't cut your own !branch 🙂 Enable enable password and ssh access and ntp 🙂
enable password 7 13061E010803
service password-encryption
username cisco privilege 15 password YOur-VerY-Secret-pASword-unencrypted-Here
ip domain-name your-domain-name
crypto key generate rsa
1024
!
ntp server IP_of_ntp_server_here
!duble check if clock is ok [yeah cisco uses clock not date, time or something linuxish :)]
!
ip ssh version 2
line vty 0 4
transport input ssh
line vty 5 15
transport input ssh
!and finally aaa
!The first thing is to check IOS capabilities. From 15.02 you should be able to multiauth users on !single port [as far as i know the 2960 combo switches has those futures limited]
!I have tested on 2960G
!
aaa new-model
!
!
aaa group server radius radiusNAC
server name your_radius_server_name
!
aaa authentication login default line enable
aaa authentication enable default enable none
aaa authentication dot1x default group radiusNAC
aaa authorization network default group radiusNAC
aaa accounting update periodic 5
aaa accounting dot1x default start-stop group radiusNAC
aaa accounting network default start-stop group radiusNAC
!
aaa server radius dynamic-author
! above line is important to reauthenticate
! below lines includes keys for radius servers [in this cace nacs agteways] keep in mind that
! you should put this keys in unencrypted form 🙂
client NAC_1_IP server-key 7 0223306834322E06737D2138373236343F210919011C
client NAC_2_IP server-key 7 0223306834322E06737D2138373236343F210919011C
auth-type all
ignore session-key
ignore server-key
ignore retransmission
!
aaa session-id common
system mtu routing 1500
authentication mac-move permit
authentication critical recovery delay 1000
!
radius-server attribute nas-port format c
radius-server dead-criteria time 30 tries 3
radius-server vsa send accounting
radius-server vsa send authentication
!
radius server your_radius_server_name
address ipv4 Radius_IP auth-port 1812 acct-port 1813
key 7 132023213438250D1417001207073738252622647C6C
!
!
dot1x system-auth-control
dot1x critical eapol
!
! And interfaces, 1-for multiauth, 3-for dynamic, downloadable acls,
! 4-for multidomain [ipphone and computer on one port]
!
interface GigabitEthernet0/1
switchport access vlan 33
switchport mode access
ip access-group 110 in
authentication control-direction in
authentication event fail action next-method
authentication event server dead action authorize vlan 23
authentication event server alive action reinitialize
authentication host-mode multi-auth
authentication open
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication violation replace
dot1x pae authenticator
!
interface GigabitEthernet0/2
switchport mode trunk
!
interface GigabitEthernet0/3
switchport access vlan 33
switchport mode access
ip access-group 110 in
authentication control-direction in
authentication event fail action next-method
authentication event server dead action authorize vlan 23
authentication event no-response action authorize vlan 400
authentication event server alive action reinitialize
authentication open
authentication order mab dot1x
authentication priority mab dot1x
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication violation replace
mab
dot1x pae authenticator
dot1x timeout tx-period 1
dot1x max-reauth-req 1
spanning-tree portfast
!
interface GigabitEthernet0/4
switchport mode access
switchport voice vlan 2
ip access-group default_acl in
authentication control-direction in
authentication event fail action authorize vlan 400
authentication event server dead action authorize vlan 23
authentication event no-response action authorize vlan 400
authentication event server alive action reinitialize
authentication host-mode multi-domain
authentication open
authentication order mab
authentication priority mab dot1x
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication violation replace
mab
dot1x pae authenticator
dot1x timeout tx-period 1
dot1x max-reauth-req 1
spanning-tree portfast
!
ip access-list extended Unregistered
permit ip any host 192.168.30.20
permit ip any host 192.168.30.21
deny udp any any eq domain
permit ip any any
ip access-list extended default_acl
permit ip any any
access-list 100 permit ip any any
access-list 110 permit ip any any
ip access-list extended EnterpriseUser
permit ip any any
! Thats all from cisco , then NAC
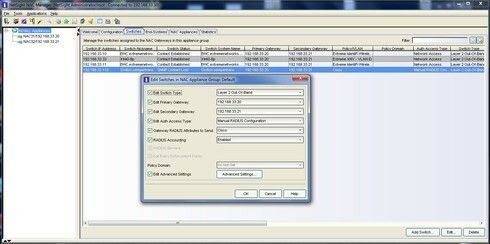
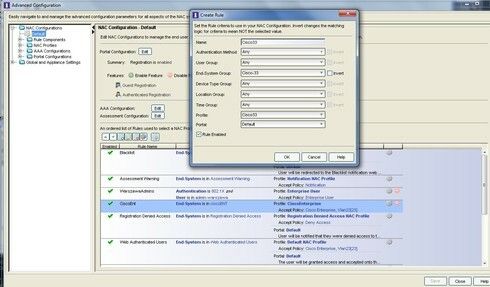
We need to make policy, end devices/users group, nac profile, group and conf for switch parameters.
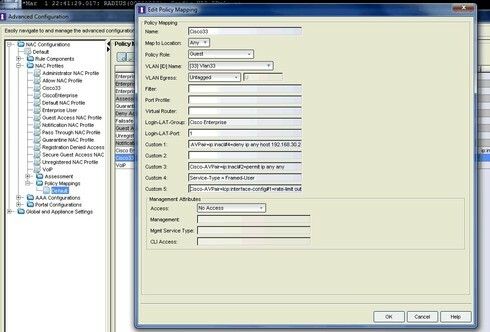
Below screens shows how to pass vlan and named acl to cisco switch.
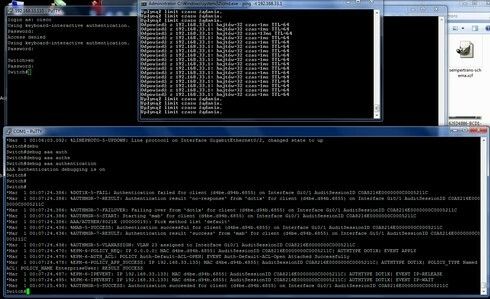
You should enable debug on cisco to check if our work works 🙂
debug authentication...
debug radius ...
If you want to pass ACL's from NAC to cisco then you should use another option fields and reconfigure switch parameters. Look at avpair atributes !
Thats all, wish you many success playing with cisco 🙂 Pls let me know if you got any success.
Below is full content of my post.
I'll try to show you how to integrate cisco switches with Extreme NAC. You can pass vlan, acl's per user, authenticate mac or user... even download acl's from NAC and even more - multiauthenticate up to 8 users on one cisco port...rate limit
! The first thing is to configure snmp access, you should see nice green circle in NMS after that.
snmp-server group V3Group v3 auth write myView
snmp-server group snmpgroup v3 auth read V3Read write V3Write
snmp-server group snmpgroup v3 priv
snmp-server view V3Read iso included
snmp-server view V3Write iso included
snmp-server community rw RW
snmp-server location DemoLab-1floor
snmp-server contact Your contact info
! dont forget create snmp user in your group with auth and priv credentials and proper security
! related to NMS profile:)
! snmp user ....
!Then we need to configure aaa radius server(s). Don't forget to check if you didn't cut your own !branch 🙂 Enable enable password and ssh access and ntp 🙂
enable password 7 13061E010803
service password-encryption
username cisco privilege 15 password YOur-VerY-Secret-pASword-unencrypted-Here
ip domain-name your-domain-name
crypto key generate rsa
1024
!
ntp server IP_of_ntp_server_here
!duble check if clock is ok [yeah cisco uses clock not date, time or something linuxish :)]
!
ip ssh version 2
line vty 0 4
transport input ssh
line vty 5 15
transport input ssh
!and finally aaa
!The first thing is to check IOS capabilities. From 15.02 you should be able to multiauth users on !single port [as far as i know the 2960 combo switches has those futures limited]
!I have tested on 2960G
!
aaa new-model
!
!
aaa group server radius radiusNAC
server name your_radius_server_name
!
aaa authentication login default line enable
aaa authentication enable default enable none
aaa authentication dot1x default group radiusNAC
aaa authorization network default group radiusNAC
aaa accounting update periodic 5
aaa accounting dot1x default start-stop group radiusNAC
aaa accounting network default start-stop group radiusNAC
!
aaa server radius dynamic-author
! above line is important to reauthenticate
! below lines includes keys for radius servers [in this cace nacs agteways] keep in mind that
! you should put this keys in unencrypted form 🙂
client NAC_1_IP server-key 7 0223306834322E06737D2138373236343F210919011C
client NAC_2_IP server-key 7 0223306834322E06737D2138373236343F210919011C
auth-type all
ignore session-key
ignore server-key
ignore retransmission
!
aaa session-id common
system mtu routing 1500
authentication mac-move permit
authentication critical recovery delay 1000
!
radius-server attribute nas-port format c
radius-server dead-criteria time 30 tries 3
radius-server vsa send accounting
radius-server vsa send authentication
!
radius server your_radius_server_name
address ipv4 Radius_IP auth-port 1812 acct-port 1813
key 7 132023213438250D1417001207073738252622647C6C
!
!
dot1x system-auth-control
dot1x critical eapol
!
! And interfaces, 1-for multiauth, 3-for dynamic, downloadable acls,
! 4-for multidomain [ipphone and computer on one port]
!
interface GigabitEthernet0/1
switchport access vlan 33
switchport mode access
ip access-group 110 in
authentication control-direction in
authentication event fail action next-method
authentication event server dead action authorize vlan 23
authentication event server alive action reinitialize
authentication host-mode multi-auth
authentication open
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication violation replace
dot1x pae authenticator
!
interface GigabitEthernet0/2
switchport mode trunk
!
interface GigabitEthernet0/3
switchport access vlan 33
switchport mode access
ip access-group 110 in
authentication control-direction in
authentication event fail action next-method
authentication event server dead action authorize vlan 23
authentication event no-response action authorize vlan 400
authentication event server alive action reinitialize
authentication open
authentication order mab dot1x
authentication priority mab dot1x
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication violation replace
mab
dot1x pae authenticator
dot1x timeout tx-period 1
dot1x max-reauth-req 1
spanning-tree portfast
!
interface GigabitEthernet0/4
switchport mode access
switchport voice vlan 2
ip access-group default_acl in
authentication control-direction in
authentication event fail action authorize vlan 400
authentication event server dead action authorize vlan 23
authentication event no-response action authorize vlan 400
authentication event server alive action reinitialize
authentication host-mode multi-domain
authentication open
authentication order mab
authentication priority mab dot1x
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication violation replace
mab
dot1x pae authenticator
dot1x timeout tx-period 1
dot1x max-reauth-req 1
spanning-tree portfast
!
ip access-list extended Unregistered
permit ip any host 192.168.30.20
permit ip any host 192.168.30.21
deny udp any any eq domain
permit ip any any
ip access-list extended default_acl
permit ip any any
access-list 100 permit ip any any
access-list 110 permit ip any any
ip access-list extended EnterpriseUser
permit ip any any
! Thats all from cisco , then NAC
We need to make policy, end devices/users group, nac profile, group and conf for switch parameters.
Below screens shows how to pass vlan and named acl to cisco switch.
You should enable debug on cisco to check if our work works 🙂
debug authentication...
debug radius ...
If you want to pass ACL's from NAC to cisco then you should use another option fields and reconfigure switch parameters. Look at avpair atributes !
Thats all, wish you many success playing with cisco 🙂 Pls let me know if you got any success.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-20-2015 10:55 AM
Hello
You can find a few answers here: https://community.extremenetworks.com/extreme/topics/integration-cisco-switches-into-enterasys-nac
And I already had seen an integration guide for Cisco switch from Enterasys. But I can't find it anymore on Extremes website.
Regards
You can find a few answers here: https://community.extremenetworks.com/extreme/topics/integration-cisco-switches-into-enterasys-nac
And I already had seen an integration guide for Cisco switch from Enterasys. But I can't find it anymore on Extremes website.
Regards