This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EOS)
- S Series VXLAN LAB setup
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
S Series VXLAN LAB setup
S Series VXLAN LAB setup
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-28-2016 12:53 PM
Hi
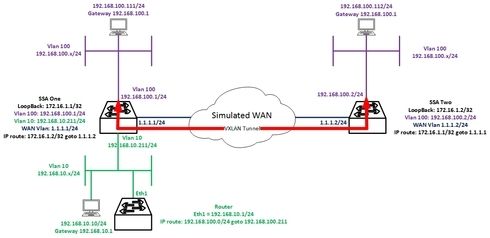
I am busy playing with VXLAN between two S series switches in my LAB and have some problems.
The two S series switches connect to each other across a L3 routed network.
I have configured the VXLAN tunnel and that seems to be working fine.
VXLAN Setup for "SSA One":
interface tun.0.1 tunnel mode vxlan l2 tbp.0.1
tunnel source 172.16.1.1
no shutdown
exit
set tunnel logical-switch create name Switch1
set tunnel map logical-switch Switch1 keyword 111 vlan 100
set tunnel remote-vtep logical-switch Switch1 ip-address 172.16.1.2
set vlan egress 100 tbp.0.1 tagged
set vlan egress 100 ge.2.48 untagged (User Port)
VXLAN Setup for "SSA Two"
interface tun.0.1 tunnel mode vxlan l2 tbp.0.1
tunnel source 172.16.1.2
no shutdown
exit
set tunnel logical-switch create name Switch1
set tunnel map logical-switch Switch1 keyword 111 vlan 100
set tunnel remote-vtep logical-switch Switch1 ip-address 172.16.1.1
set vlan egress 100 tbp.0.1 tagged
set vlan egress 100 tg.1.24 untagged (User Port)
With the above configuration, devices connected to both S series switches in vlan 100 can ping each other.
-----------------------------------------------------------------------------------------
For the next part of my lab I would like to test routing from the remote site (SSA Two) to a network that is connected to "SSA one"
For this I added another vlan on "SSA one" and created a routed interface.
For users in vlan 100 (the VXLAN vlan) I have specified 192.168.100.1 (Vlan 100 interface on "SSA One") as the default gateway.
Clients connected the "SSA one" in vlan 100 can ping any device in vlan 10 and any device in vlan 10 can ping any device connected to "SSA one" in vlan 100.
The problem I have is with the remote clients.
The Remote clients connected to "SSA Two" in vlan 100 can ping any other device in vlan 100 (Both SSA one and SSA Two). These clients can also ping the Vlan 10 interface of "SSA One" (192.168.10.211), but they can not ping any other device in vlan 10.
The Vlan 10 devices can not ping any of the remote vlan 100 (SSA two) clients.
Why is this?
If I extend vlan 100 from "SSA One" to an external router that routes traffic for both Vlan 100 and Vlan 10 then every client can reach every other client.
Only when I use one of the terminating VXLAN SSA's for routing can the remote client not route out.
Hope this makes sense....
Regards
I am busy playing with VXLAN between two S series switches in my LAB and have some problems.
The two S series switches connect to each other across a L3 routed network.
I have configured the VXLAN tunnel and that seems to be working fine.
VXLAN Setup for "SSA One":
interface tun.0.1 tunnel mode vxlan l2 tbp.0.1
tunnel source 172.16.1.1
no shutdown
exit
set tunnel logical-switch create name Switch1
set tunnel map logical-switch Switch1 keyword 111 vlan 100
set tunnel remote-vtep logical-switch Switch1 ip-address 172.16.1.2
set vlan egress 100 tbp.0.1 tagged
set vlan egress 100 ge.2.48 untagged (User Port)
VXLAN Setup for "SSA Two"
interface tun.0.1 tunnel mode vxlan l2 tbp.0.1
tunnel source 172.16.1.2
no shutdown
exit
set tunnel logical-switch create name Switch1
set tunnel map logical-switch Switch1 keyword 111 vlan 100
set tunnel remote-vtep logical-switch Switch1 ip-address 172.16.1.1
set vlan egress 100 tbp.0.1 tagged
set vlan egress 100 tg.1.24 untagged (User Port)
With the above configuration, devices connected to both S series switches in vlan 100 can ping each other.
-----------------------------------------------------------------------------------------
For the next part of my lab I would like to test routing from the remote site (SSA Two) to a network that is connected to "SSA one"
For this I added another vlan on "SSA one" and created a routed interface.
For users in vlan 100 (the VXLAN vlan) I have specified 192.168.100.1 (Vlan 100 interface on "SSA One") as the default gateway.
Clients connected the "SSA one" in vlan 100 can ping any device in vlan 10 and any device in vlan 10 can ping any device connected to "SSA one" in vlan 100.
The problem I have is with the remote clients.
The Remote clients connected to "SSA Two" in vlan 100 can ping any other device in vlan 100 (Both SSA one and SSA Two). These clients can also ping the Vlan 10 interface of "SSA One" (192.168.10.211), but they can not ping any other device in vlan 10.
The Vlan 10 devices can not ping any of the remote vlan 100 (SSA two) clients.
Why is this?
If I extend vlan 100 from "SSA One" to an external router that routes traffic for both Vlan 100 and Vlan 10 then every client can reach every other client.
Only when I use one of the terminating VXLAN SSA's for routing can the remote client not route out.
Hope this makes sense....
Regards
15 REPLIES 15
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-06-2017 05:24 AM
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-29-2016 10:26 AM
I have thx.... wanted to use the new stuff 😉
Lets wait and see what we get from the extreme guys on this....
Lets wait and see what we get from the extreme guys on this....
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-29-2016 10:26 AM
Hi Andre,
Since this is suspected to be a bug, would you please open a case with GTAC so it can be properly reviewed?
It will also be helpful to include a link to this thread in the case details.
Since this is suspected to be a bug, would you please open a case with GTAC so it can be properly reviewed?
It will also be helpful to include a link to this thread in the case details.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-29-2016 10:19 AM
Hi Andre,
have you considered using GRE L2 tunneling instead? As I see it, VXLAN can be used for DCI, but other methods exist as well and might be better tested.
Br,
Erik
have you considered using GRE L2 tunneling instead? As I see it, VXLAN can be used for DCI, but other methods exist as well and might be better tested.
Br,
Erik