EAP-TLS: TLS Alert read:fatal:unknown CA
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-24-2022 02:23 PM
I'm testing EAP-TLS wireless cert-authentication this time. The radius debug log shows the following errors.
I have both private CA certs added to the RADIUS certificate section (Configuration -->System Config-->SSL Certs---Radius)
The certificate order is Root-CA first, Issuer/Intermediate CA second..screenshot below. The android phone also includes both CA certificates. My connection profile is set for the SecureSSID with a EAP-TLS source. The EAP-TLS source has no conditional matches and acts as a catch-all.
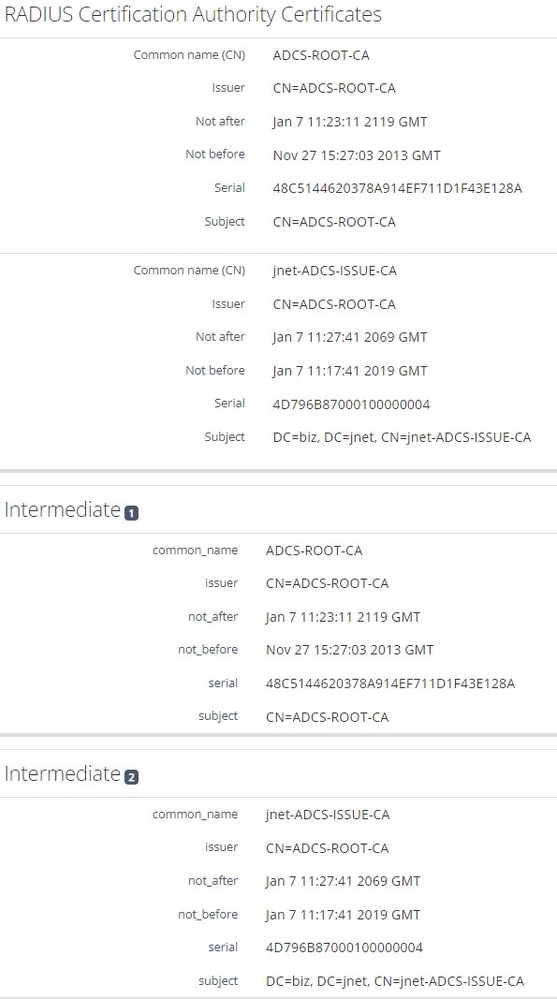
I have both private CA certs added to the RADIUS certificate section (Configuration -->System Config-->SSL Certs---Radius)
The certificate order is Root-CA first, Issuer/Intermediate CA second..screenshot below. The android phone also includes both CA certificates. My connection profile is set for the SecureSSID with a EAP-TLS source. The EAP-TLS source has no conditional matches and acts as a catch-all.
Debug: eap: Peer sent packet with method EAP TLS (13)
Debug: eap: Calling submodule eap_tls to process data
Debug: eap_tls: Continuing EAP-TLS
Debug: eap_tls: [eaptls verify] = ok
Debug: eap_tls: Done initial handshake
ERROR: eap_tls: TLS Alert read:fatal:unknown CA
ERROR: eap_tls: TLS_accept: Failed in error
ERROR: eap_tls: Failed in __FUNCTION__ (SSL_read)
ERROR: eap_tls: error:14094418:SSL routines:ssl3_read_bytes:tlsv1 alert unknown ca
ERROR: eap_tls: error:140940E5:SSL routines:ssl3_read_bytes:ssl handshake failure
ERROR: eap_tls: System call (I/O) error (-1)
ERROR: eap_tls: TLS receive handshake failed during operation
ERROR: eap_tls: [eaptls process] = fail
ERROR: eap: Failed continuing EAP TLS (13) session. EAP sub-module failed
Debug: eap: Sending EAP Failure (code 4) ID 212 length 4
Debug: eap: Failed in EAP select

1 REPLY 1
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-25-2022 10:15 AM
Is this a private CA with no intermediate CAs? Did the root CA sign both the RADIUS server certificate used by A3 and the client certificates used by clients? Or was the RADIUS SERVER cert signed by the root but the ISSUE-CA cert signed clients?
The general order:
The Certificate field will contain the CERT of the RADIUS SERVER certificate.
The Certificate Authority certificate(s) field will contain, in order, the ROOT certificate that *signed* the RADIUS SERVER certificate followed by any other client certificate signing authorities in any order.
The Intermediates will only be populated if there are intermediates in the chain for the RADIUS SERVER (i.e. Root -> Intermediate 1 -> Intermediate 2 -> Server -> Client). So if jnet-ADCS-ISSUE-CA signed the RADIUS SERVER cert it will be listed here. If the RADIUS SERVER cert was signed by a different CA it would be listed here. If the RADIUS SERVER cert was signed by the root, then it would be listed here.
See https://extremeportal.force.com/ExtrArticleDetail?an=000098912 for some more information.
The general order:
The Certificate field will contain the CERT of the RADIUS SERVER certificate.
The Certificate Authority certificate(s) field will contain, in order, the ROOT certificate that *signed* the RADIUS SERVER certificate followed by any other client certificate signing authorities in any order.
The Intermediates will only be populated if there are intermediates in the chain for the RADIUS SERVER (i.e. Root -> Intermediate 1 -> Intermediate 2 -> Server -> Client). So if jnet-ADCS-ISSUE-CA signed the RADIUS SERVER cert it will be listed here. If the RADIUS SERVER cert was signed by a different CA it would be listed here. If the RADIUS SERVER cert was signed by the root, then it would be listed here.
See https://extremeportal.force.com/ExtrArticleDetail?an=000098912 for some more information.
