- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ Controller
- XCC & Control Captive Portal
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
XCC & Control Captive Portal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-23-2021 04:19 PM
Essentially the endpoint is placed into the correct network and is challenged by the captive portal (to accept T&Cs) but their network access is not restricted as an unregistered user.. they can browse the internet when this should not be allowed until they become registered. My understanding is that the 'unregistered' role is built-in to XCC and it should be preventing access. Any tips on how to stop traffic until the registered phase?
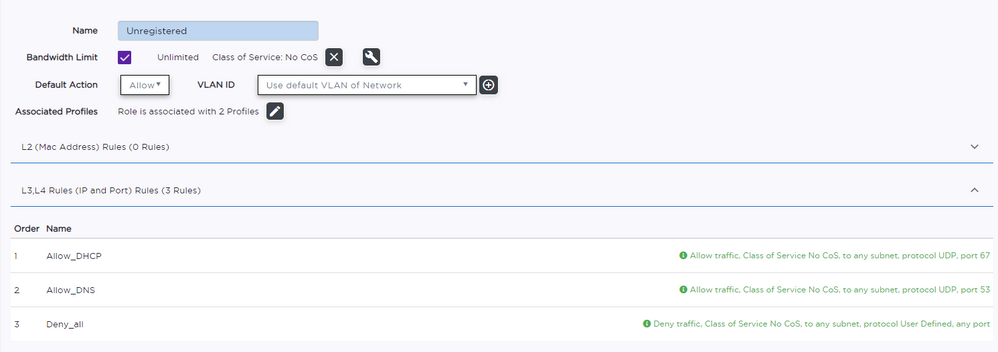
I have tried these rules but they dont seem to have any effect. If I change the default action to deny on the unregistered role they get no access network access at all (i.e. not even captive portal).
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-25-2021 03:23 PM
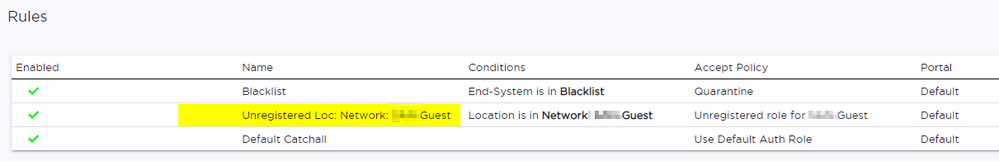
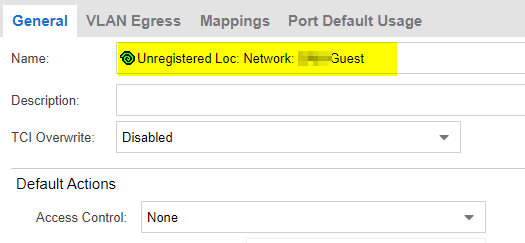
I raised a GTAC ticket and had some assistance. Essentially with XCC 5.36 the role name used for captive portal has changed. When you create a captive portal a "Onboard / Rule" is created and it is the name of this rule that must be returned by control. In my case the default rules were all I needed (didn't need to add services to the role in policy).
XCC Onboard Rule:
Policy Role in Control with matching Name:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-25-2021 03:23 PM
I raised a GTAC ticket and had some assistance. Essentially with XCC 5.36 the role name used for captive portal has changed. When you create a captive portal a "Onboard / Rule" is created and it is the name of this rule that must be returned by control. In my case the default rules were all I needed (didn't need to add services to the role in policy).
XCC Onboard Rule:
Policy Role in Control with matching Name:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-25-2021 05:04 AM
Which role are you returning in the unauthenticated state, it should be Unregistered role for network <network> if you are using the automatically generated role?
If you are using your own unregistered role, have you added some specific "redirect" rules into that role.
If the above doesn't help then it maybe worth opening a case with GTAC.
-Gareth