- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ Controller
- XCC Dynamic VLAN Assignment
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
XCC Dynamic VLAN Assignment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-13-2021 11:56 AM
Hi Guys,
I'm working on a customer deployment and got some issues using ExtremeControl and XCC (5.36.03).
If I send RFC3580 Vlan Attributes to XCC from the Control, the 802.1x session from the client can't authenticate, even with the VLAN created under Policy > Vlans and the same vlan associated to the Device Group's Profile.
Taking the "Guest Access" role as example, it is configured on the XCC to use the "Default Network VLAN" (as it is in sync with the policy domain, applied to the wired infrastructure too). I've created the VLAN 40 and marked as Bridge@AP Tagged and associated it with the Device Group's Profile (https://extremeportal.force.com/ExtrArticleDetail?an=000094691),
If I send only the FilterID 'policy=Guest Access' the client, the client get's authenticated, but still on the default WLAN VLAN (120). If I send the VTA attributes as follows, the same client can't authenticate:
Filter-Id=Enterasys:version=1:%MANAGEMENT%policy=%POLICY_NAME%
Login-LAT-Port=%LOGIN_LAT_PORT%
Service-Type=%MGMT_SERV_TYPE%
Tunnel-Private-Group-Id=%VLAN_ID%:%VLAN_TUNNEL_TAG%
Tunnel-Type=13:%VLAN_TUNNEL_TAG%
Tunnel-Medium-Type=6:%VLAN_TUNNEL_TAG%
The policy mapping is done on the Control for the dynamic vlan I want to apply.
Any ideas?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-17-2021 01:32 PM
Hi PeterK,
I've just posted the config where I got issues… In summary: B@AC works perfectly, B@AP don't work. Below follows more info...
As far as I discovered, the Dynamic VLAN assignment works without a "Role-to-VLAN pair" static creation on XCC, using RADIUS VLAN attributes, on B@AC topologies, but is not working o B@AP or FabricAttach topologies, even with the association of the VLANs to the Device Group's profile.
Creating the "Role-to-VLAN pairs" is not an option, as the customer is using a single Policy Domain for Wired and Wireless, and this solutions "would not fit" on the environment. Using B@AC solution is not an option as well.
Best regards,
-Leo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-14-2021 11:19 AM
Hi Ovais,
I'll try this approach and let you know if it works!
Thank you so much for the detailed explanation. I appreciate that!
Best regards,
-Leo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-14-2021 12:24 AM
I see, its a bit more clear now. If you have not tried the following already, give it a go. I think this configuration can help you.
I have recently implemented the exact same scenario with XCC version 5.26 for few different deployments. I assign same role to users but flip VLAN based on the user’s location, location could be a building or a floor etc. Assuming you are something similar. To achieve this, I used RFC3576 with the attributes I mentioned in my previous post. This use case is addressed a bit differently in XCC, unlike identifi HYBRID mode where we could use RFC3580 and pass role and VLAN as two separate attributes, XCC needs a bit more config. I am not sure what your deployments looks like and how granular the VLAN assignment is. This config example is based on one VLAN per building, therefore “location” is used as a key differentiator. Likewise, you can have one VLAN per floor/device group/AP etc.
You can use “Location” tab in Site configuration to configure location/zone information, you will use this as a match condition for VLAN assignment, you can either use the name of the SITE itself or one of the following location parameters:
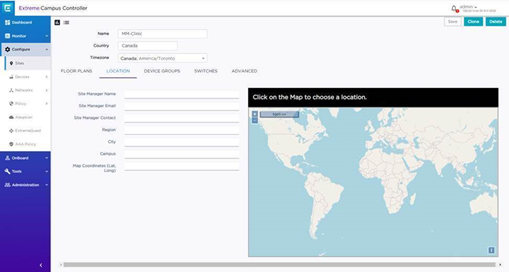
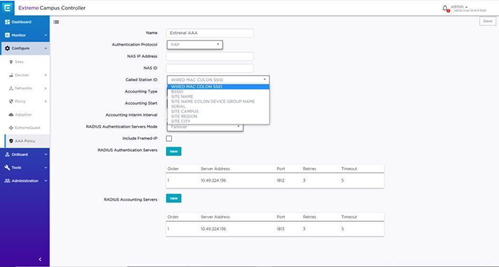
Then, make change to AAA policy in XCC and configure either site name/city/region/ as Called station ID to the NAC (based on how granular the VLAN assignment is). XCC will replace original Called station ID with the one you specify here while sending the authentication request to the NAC.
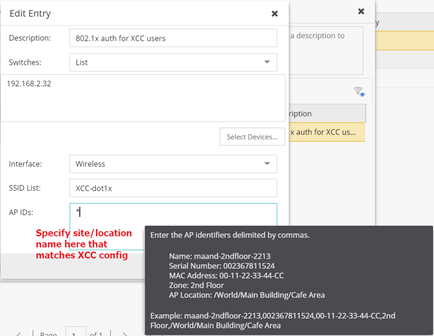
On the NAC, create “location groups” and specify the “Site Name” or whatever parameter you used as Called Station ID. NAC will match this with the incoming Called Station ID.
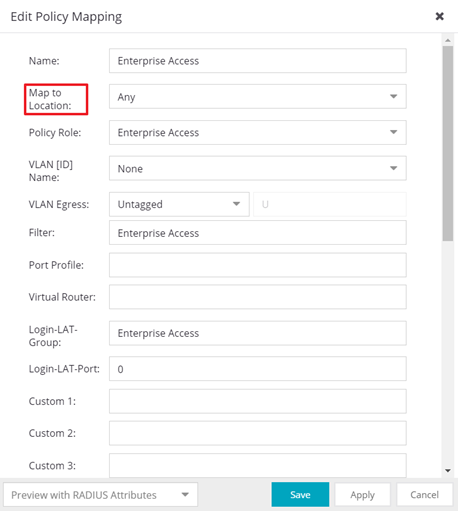
As for the Policy Mapping, you can create Policy Mappings with the same Role name and specify different “Map to location” value for each of them. This will allow NAC to determine which VLAN to return based on location while still using the same Policy Role.
Regards,
Ovais
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-13-2021 08:24 PM
Hi Ovais,
- The XCC didn’t receive the correct filter-id for the role, therefore it puts the client on default WLAN VLAN.
The XCC should be receiving the correct attributes (as I state on item B below), and I ran an TCPDUMP on NAC, and the RADIUS packets seems to be OK.
- It received the filter-id but the AP profile does not have this roles assigned/mapped on it.
The AP receives the same Filter-ID, but when I choose to send the other Radius Attributes, the client is unable to authenticate. Simply changing the NAC's response attributes back, without VLAN related attributes, it works, so the Roles ate already at XCC.
- You are using the attributes to pass VLAN ID, may be you don’t have VLAN configured in policy mapping settings.
I've configured them at the Policy Mapping (and tested on the wired side, with EXOS, and it works es expected).
- I was wondering why do you need to use RFC3580 and pass the VLAN ID as an attribute, not saying it doesn’t work that way, it does, I have done it many time with RFC3576 and passing VLAN as an attribute like following when the requirement is to assign same user Role but different VLANs based on location for instance.
Maybe I wasn't clear, sorry, but I've just configured something like the screenshot provided, and already used it on EXOS and IdentiFi several times, but never with XCC. The goal is really to use the same Role, but assign different VLANs based on the NAC rules, keeping the policy domain consistent across wired/wireless. Passing just the policy in the Filter-ID is not enough, because we don't want to have "Contain to VLAN" Roles, because we use different VLANS, depending on the environment (wired/wireless), departments, AD user groups, etc… But the VLAN attributes seems to be not working… I've ran a test on an old IdentiFi controller, and it works…
- In case, you just need to use diff. Roles each with diff. VLAN, passing the Role as a filter-id to XCC should do the trick since XCC already has the VLAN defined within the Role. If that’s not happening, I will delete the VLAN configuration on the XCC and re-create it.
Unfortunately it's not the case (and I've tested this scenario and selecting the VLAN on the Role make it work perfectly, as soon as I don't pass any VLAN attributes. If I set the VLAN on the Role and send the VLAN attributes, it doesn't work as well). The customer, as stated before, want to use the same Roles, but applying different VLANs depending on the NAC Rules they defined…
It seems an issue with XCC…
Best regards,
-Leo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-13-2021 07:02 PM
So, looks like there is something wrong with the policy assignment:
If I send only the FilterID 'policy=Guest Access' the client, the client get's authenticated, but still on the default WLAN VLAN (120). If I send the VTA attributes as follows, the same client can't authenticate:
Filter-Id=Enterasys:version=1:%MANAGEMENT%policy=%POLICY_NAME%
Login-LAT-Port=%LOGIN_LAT_PORT%
Service-Type=%MGMT_SERV_TYPE%
Tunnel-Private-Group-Id=%VLAN_ID%:%VLAN_TUNNEL_TAG%
Tunnel-Type=13:%VLAN_TUNNEL_TAG%
Tunnel-Medium-Type=6:%VLAN_TUNNEL_TAG%
When the guest authenticates, do you see it getting “Guest Access” role in XCC “Clients” tab? the only reason it should fall back to the default WLAN VLAN is when one of the following is true:
- The XCC didn’t receive the correct filter-id for the role, therefore it puts the client on default WLAN VLAN.
- It received the filter-id but the AP profile does not have this roles assigned/mapped on it.
- You are using the attributes to pass VLAN ID, may be you don’t have VLAN configured in policy mapping settings.
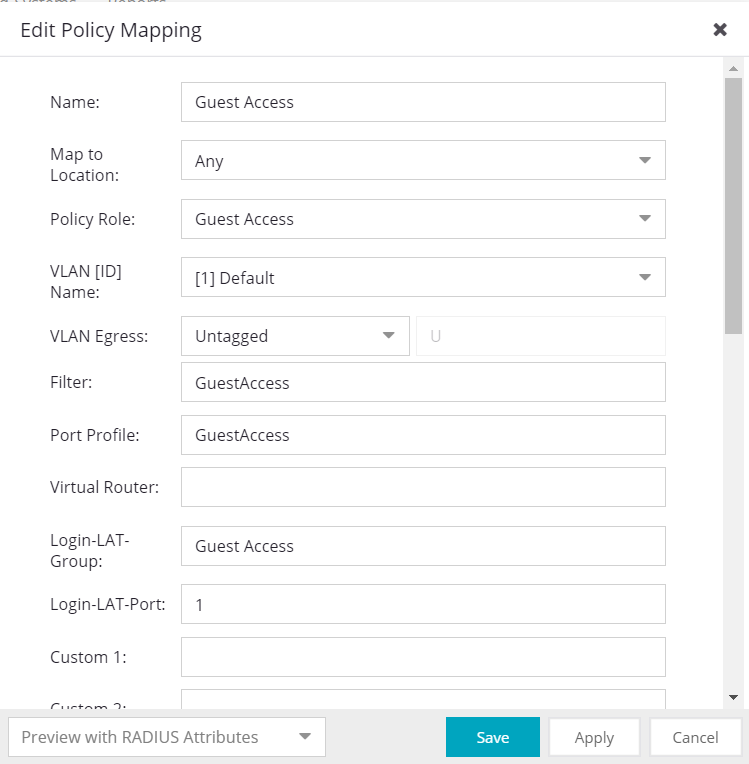
I was wondering why do you need to use RFC3580 and pass the VLAN ID as an attribute, not saying it doesn’t work that way, it does, I have done it many time with RFC3576 and passing VLAN as an attribute like following when the requirement is to assign same user Role but different VLANs based on location for instance.
Filter-Id=Enterasys:%POLICY_NAME%
Login-LAT-Port=%LOGIN_LAT_PORT%
Tunnel-Private-Group-Id=%VLAN_ID%:%VLAN_TUNNEL_TAG%
Tunnel-Type=13:%VLAN_TUNNEL_TAG%
Tunnel-Medium-Type=6:%VLAN_TUNNEL_TAG%
In case, you just need to use diff. Roles each with diff. VLAN, passing the Role as a filter-id to XCC should do the trick since XCC already has the VLAN defined within the Role. If that’s not happening, I will delete the VLAN configuration on the XCC and re-create it.
Regards,
Ovais
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-13-2021 04:21 PM
Hi Ovais,
I'm using direct integration with NAC using Configuration > AAA Policy.
Time is in sync, and it works flawlessly (using the default WLAN VLAN) if I send only the FilterID.
Now if I use the RFC3580 RADIUS Attributes to assign a different VLAN (note that this other VLAN is already created and associated to the Device Group on XCC), the client (802.1x) simply can't connect (even showing successfully authenticated and authorized on NAC).
I've already double-checked the Deployment Guide, bot I couldn't find anything wrong.
Best regards,
-Leo
