- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Analytics Configuration
Analytics Configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-25-2020 05:23 AM
Hi Everyone,
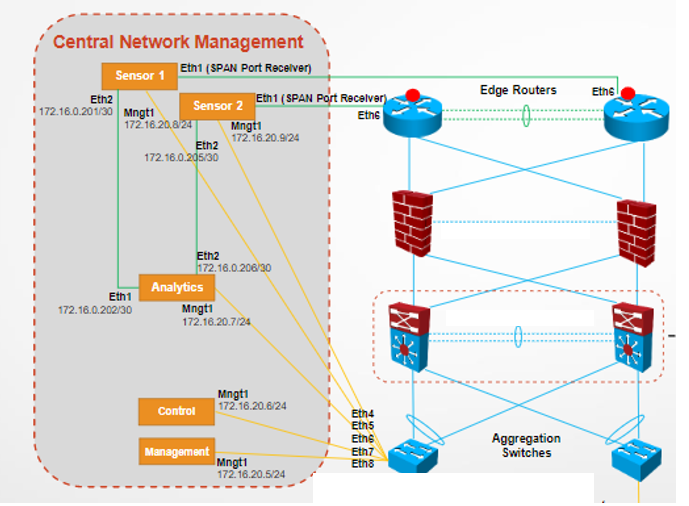
Below diagram is the position of our XMC devices.
Please help on how to configure flow collector sensor SSA link to two mirrored routers.
Please share any sample configuration for physical connectivity base on our XMC design.
Any configuration that helps us to build the Central Management. Thank you
SSA - 2 units
Analytics - 1 unit
XMC - 1 unit
NAC - 1 unit
Regards,
Sazon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-03-2020 08:42 PM
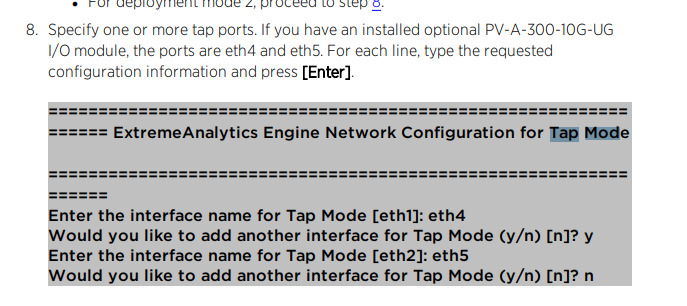
I believe so,
See the following install guide clip:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-01-2020 05:29 AM
Hi Ryan,
PV-A-305
PV-FC-180
Yes you are correct.
My two sensors SSA wil directly mirror traffic from the routers.
Then, the two sensors SSA is also directly connected to our Analytics appliance.
The Analytics Appliance will connect the management port to our internal network to be able to add in our XMC.
I am reading the link you shared. Please see the screenshot below and which deployment set up will I choose.

Is it possible to have two directly connected sensors to the analytics compliance (eth0, eth1) and the management port will be the one to become engine IP address.
Regards,
Sazon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-31-2020 06:58 PM
Hello,
You are trying to configure two PV-FC-180 appliances to tunnel GRE traffic back to the Analytics box correct? Are Sensor 1 and Sensor 2 PV-FC-180s?
The are the sensors directly connected to the analytics box as the diagram suggests?
Typically the sensors are set up to tunnel the traffic into a GRE tunnel back to the analytics:
Check out this article:
The XMC server is pretty good at configuring the PV-FC-180 appliance. Just make sure the SNMP profile assigned has the correct CLI credentials.
If the appliances are directly connected I think you might be able to just mirror the traffic through to the analytics box and configure netflow on the mirror ingress port. Per the deployment guide you should be able to get eth4 and eth5 of the analytics box into “tap mode”
“2. Interface Mirrored - Separate interfaces are configured for management and monitoring traffic. The monitoring interface will put into tap mode for traffic monitoring. Suitable for feeds from XOS/VOSS/SLX switches”
In this case I think you could get away with setting the mirror ports to port 2.
Configure IP address:
configure terminal
!
interface vlan.0.10
ip address 10.X.X.X.X 255.255.255.252 primary
no ip proxy-arp
no ip forwarding
no shutdown
exit
(Note: Do not configure IP on VLAN 1, or if you do remove VLAN 1 from all other ports. If not there’s a change the ARP packets could be dropped due to pvid 0 drop flow configuration, resulting in L3 management loss)
Configure Netflow:
# netflow
set netflow export-interval 1
set netflow export-destination 10X.X.X.X 2055
set netflow export-version 9
set netflow port tg.1.2 enable rx
set netflow template refresh-rate 30 timeout 1
set netflow cache enable
Configure Mirror:
# mirror
set mirror create 1
set mirror 1 mirrorN 15
set mirror ports ge.1.2 1
(Difference being send the mirror N to another physical port and the Tbp.0.1 port per the article to get it into the GRE turnnel.
Apply policy to mirror ingress port:
# policy
set policy profile 1 name EMC_FS_Mirror pvid-status enable pvid 0 mirror-destination 1
set policy rule admin-profile port tg.1.2 mask 16 port-string tg.1.2 admin-pid 1
set policy rule 1 ipproto 47 mask 8 drop prohibit-mirror
Enable jumbo:
# port
set port jumbo enable tg.1.1
set port jumbo enable tg.1.2
set port jumbo enable tg.1.3
set port jumbo enable tg.1.4
The difference between the first configuration is that the policy that is applied to the mirror ingress port will mirror the traffic into tbp.0.1 which is then send into the gre tunnel through the configuration for “interface tun.0.1”
In your case it seems unnecessary to put the mirrored traffic in the tunnel when the appliance is already directly connected.
Someone will probably post an let me know if this isn’t the case.
Thanks
-Ryan
