- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Re: ERS 4800 FA ISID/VLAN assignment with NAC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ERS 4800 FA ISID/VLAN assignment with NAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-19-2021 11:37 PM
Hi All,
Wondering if anyone has a template for setting up ERS 4800 with Extreme Control so that ISID/VLAN pairs are auto-created.
Upstream switch is a VSP7400 and I can manually assign a port using cli “i-sid <ISID> vlan <ID>”. This tests successfully if I then add a port member manually.
When trying to automate this with MAC based auth via Extreme NAC I get “RADIUS Authentication timeout”
B09-L02C1S3(config)#% show eapol sessions
-------------------------- Unauthorized Clients ----------------------------
Unit/Port Client MAC Address Type Radius Status
--------- ------------------ -------------- ------------------------------
1/2 00:C0:B7:92:FE:D3 Intruder RADIUS Authentication timeout
Looking at control logs the correct rule is being hit and attributes are being passed:
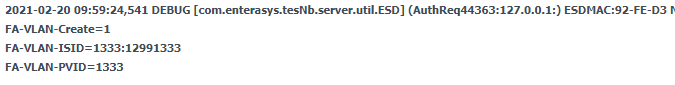
I can see radius responses via a packet capture as well.. so there are responses going back to the switch (in addition management radius logins work).
ERS:
!
! *** VLAN ***
!
vlan create 6 type port 1
vlan ports 1/1-48 tagging unTagPvidOnly
vlan ports 1/50 tagging tagAll
vlan ports 2/1-48 tagging unTagPvidOnly
vlan ports 2/50 tagging tagAll
vlan configcontrol flexible
vlan members 1 NONE
no auto-pvid
!
eapol multihost allow-non-eap-enable
eapol multihost radius-non-eap-enable
eapol multihost auto-non-eap-mhsa-enable
eapol multihost use-radius-assigned-vlan
eapol multihost non-eap-use-radius-assigned-vlan
eapol multihost eap-packet-mode unicast
eapol multihost multivlan enable
eapol multihost non-eap-reauthentication-enable
interface Ethernet ALL
eapol multihost port 1/2 enable eap-mac-max 2 allow-non-eap-enable non-eap-mac-max 2 radius-non-eap-enable use-radius-assigned-vlan
non-eap-use-radius-assigned-vlan eap-packet-mode unicast mac-max 2
exit
no eapol multihost non-eap-pwd-fmt ip-addr
no eapol multihost non-eap-pwd-fmt port-number
interface Ethernet ALL
eapol port 1/2 status auto traffic-control in
exit
fa extended-logging
fa zero-touch-option auto-port-mode-fa-client client-type 6-7
fa zero-touch-option auto-trusted-mode-fa-client client-type 6-7
no fa message-authentication 1/ALL,2/ALL
Eventually I want to auth an avaya handset and a PC.. at the moment just wanting to get a single device authd with PVID set (untagged).
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-20-2021 08:53 AM
Hi Glen,
Here a working setup for me on ERS-4850 with a small difference.
I’m using SPBM on the ERS and not fabric attach but the radius attributes should be ok.
ERS4850:
!
! *** RADIUS ***
radius server host 10.xx.xx.xx acct-enable
radius server host used-by eapol acct-enable
radius server host used-by non-eapol acct-enable timeout 20
radius accounting interim-updates enable
radius reachability mode use-radius username "reachme" password "reachme"
radius reachability timeout 2
!
! *** RADIUS Dynamic Server ***
radius dynamic-server replay-protection
radius dynamic-server client 10.xx.xx.xx
radius dynamic-server client 10.xx.xx.xx port 3799
adius dynamic-server client 10.xx.xx.xx secret ****************
adius dynamic-server client 10.xx.xx.xx enable
radius dynamic-server client 10.xx.xx.xx process-change-of-auth-requests
radius dynamic-server client 10.xx.xx.xx process-disconnect-requests
radius dynamic-server client 10.xx.xx.xx process-reauthentication-requests
!
! *** EAP ***
eapol multihost allow-non-eap-enable
eapol multihost radius-non-eap-enable
eapol multihost non-eap-phone-enable
eapol multihost use-radius-assigned-vlan
eapol multihost non-eap-use-radius-assigned-vlan
eapol multihost eap-packet-mode unicast
eapol multihost multivlan enable
!
interface Ethernet ALL
eapol multihost port 1-50 enable eap-mac-max 3 allow-non-eap-enable non-eap-mac-max 3 radius-non-eap-enable non-eap-phone-enable use-radius-assigned-vlan non-eap-use-radius-assigned-vlan eap-packet-mode unicast mac-max 3
exit
no eapol multihost non-eap-pwd-fmt ip-addr
no eapol multihost non-eap-pwd-fmt port-number
interface Ethernet ALL
! EAPOL ENABLED PORTS
eapol port 1-48 status auto re-authentication-period 60 quiet-interval 30 max-request 10
! UPLINKS
eapol port 47-50 re-authentication-period 60 quiet-interval 30 max-request 10
interface Ethernet ALL
eapol port ALL radius-dynamic-server enable
exit
!
! *** EAP Voip VLAN ***
! eapol enable
!
! *** Fabric Attach ***
fa auto-provision server
fa zero-touch-option auto-trusted-mode-fa-client client-type 6
fa zero-touch-option auto-pvid-mode-fa-client client-type 6
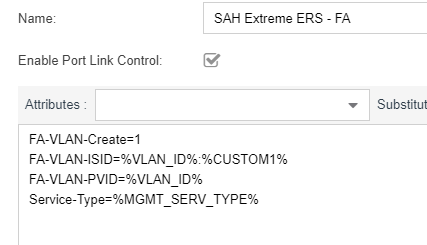
Here the NAC Radius attributes template:
FA-VLAN-Create=1
FA-VLAN-ISID=%VLAN_ID%:%CUSTOM1%
Egress-VLANID=0x%CUSTOM2%
FA-Service-Request=BPDU
FA-Service-Request=SLPPGUARD
FA-Service-Request=DHCPSNOOP:%VLAN_ID%
Service-Type=%MGMT_SERV_TYPE%
%CUSTOM3%
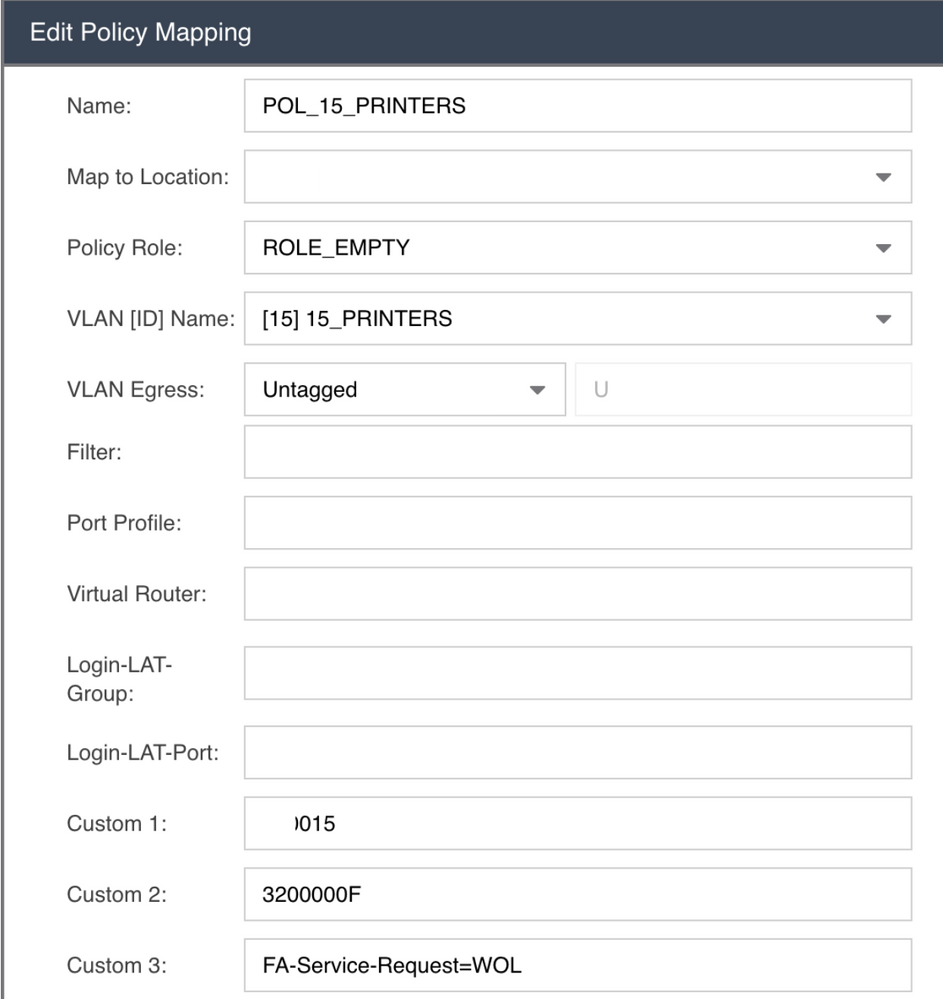
Here the policy mapping for a printer (untagged) (32000xxx where 32=untagged and xxx=VLANID in hex):
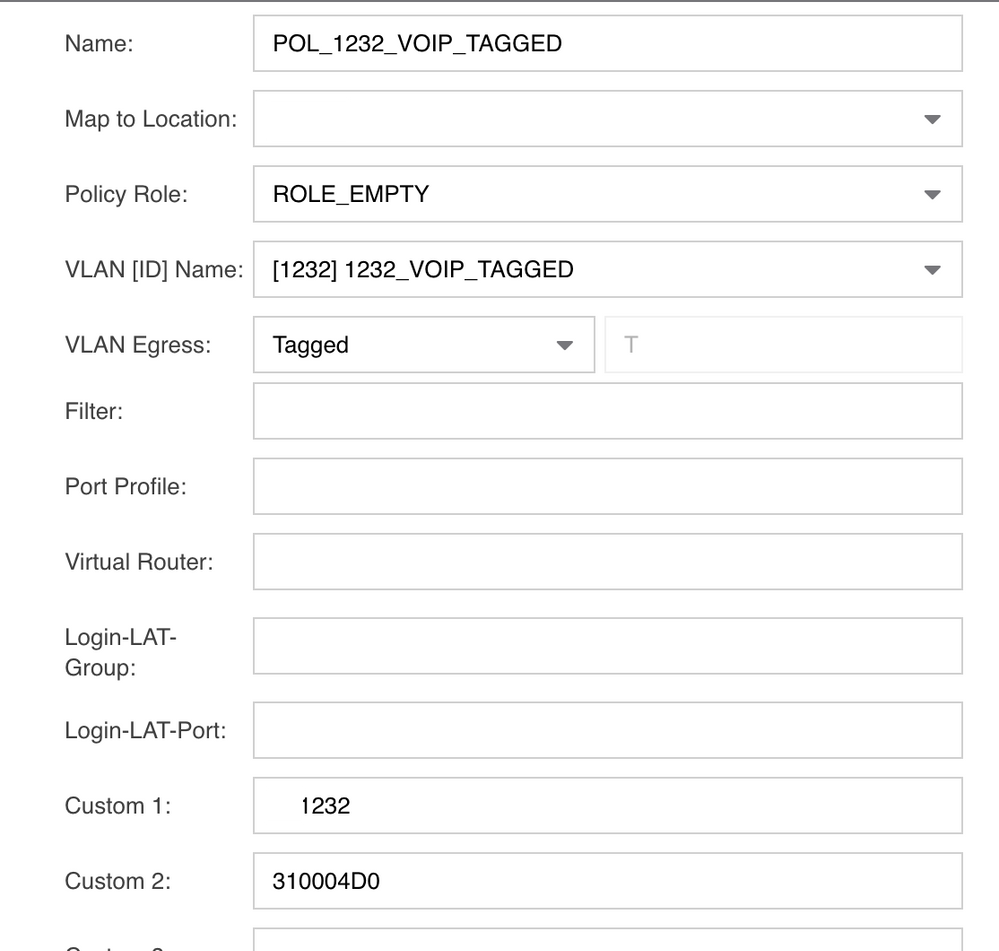
Here for an IPPhone (a client can be attached behind the phone also doing MAC/802.1X auth)(31000xxx where 31=tagged and xxx=VLANID in hex)::
Give it a try and let me know
Mig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-21-2021 07:23 AM
Glad to see it ok.
With this kind of setup and Access Control flexibility you have access to a huge potential for network automation.
Have a look at those threads:
Please, don’t forget to close this topic
Regards,
Mig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-21-2021 07:04 AM
Hah thanks so much Mig. That works a treat!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-20-2021 08:53 AM
Hi Glen,
Here a working setup for me on ERS-4850 with a small difference.
I’m using SPBM on the ERS and not fabric attach but the radius attributes should be ok.
ERS4850:
!
! *** RADIUS ***
radius server host 10.xx.xx.xx acct-enable
radius server host used-by eapol acct-enable
radius server host used-by non-eapol acct-enable timeout 20
radius accounting interim-updates enable
radius reachability mode use-radius username "reachme" password "reachme"
radius reachability timeout 2
!
! *** RADIUS Dynamic Server ***
radius dynamic-server replay-protection
radius dynamic-server client 10.xx.xx.xx
radius dynamic-server client 10.xx.xx.xx port 3799
adius dynamic-server client 10.xx.xx.xx secret ****************
adius dynamic-server client 10.xx.xx.xx enable
radius dynamic-server client 10.xx.xx.xx process-change-of-auth-requests
radius dynamic-server client 10.xx.xx.xx process-disconnect-requests
radius dynamic-server client 10.xx.xx.xx process-reauthentication-requests
!
! *** EAP ***
eapol multihost allow-non-eap-enable
eapol multihost radius-non-eap-enable
eapol multihost non-eap-phone-enable
eapol multihost use-radius-assigned-vlan
eapol multihost non-eap-use-radius-assigned-vlan
eapol multihost eap-packet-mode unicast
eapol multihost multivlan enable
!
interface Ethernet ALL
eapol multihost port 1-50 enable eap-mac-max 3 allow-non-eap-enable non-eap-mac-max 3 radius-non-eap-enable non-eap-phone-enable use-radius-assigned-vlan non-eap-use-radius-assigned-vlan eap-packet-mode unicast mac-max 3
exit
no eapol multihost non-eap-pwd-fmt ip-addr
no eapol multihost non-eap-pwd-fmt port-number
interface Ethernet ALL
! EAPOL ENABLED PORTS
eapol port 1-48 status auto re-authentication-period 60 quiet-interval 30 max-request 10
! UPLINKS
eapol port 47-50 re-authentication-period 60 quiet-interval 30 max-request 10
interface Ethernet ALL
eapol port ALL radius-dynamic-server enable
exit
!
! *** EAP Voip VLAN ***
! eapol enable
!
! *** Fabric Attach ***
fa auto-provision server
fa zero-touch-option auto-trusted-mode-fa-client client-type 6
fa zero-touch-option auto-pvid-mode-fa-client client-type 6
Here the NAC Radius attributes template:
FA-VLAN-Create=1
FA-VLAN-ISID=%VLAN_ID%:%CUSTOM1%
Egress-VLANID=0x%CUSTOM2%
FA-Service-Request=BPDU
FA-Service-Request=SLPPGUARD
FA-Service-Request=DHCPSNOOP:%VLAN_ID%
Service-Type=%MGMT_SERV_TYPE%
%CUSTOM3%
Here the policy mapping for a printer (untagged) (32000xxx where 32=untagged and xxx=VLANID in hex):

Here for an IPPhone (a client can be attached behind the phone also doing MAC/802.1X auth)(31000xxx where 31=tagged and xxx=VLANID in hex)::

Give it a try and let me know
Mig
