This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- RE: How to create a single SSID with multiple vlan...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to create a single SSID with multiple vlans ?
How to create a single SSID with multiple vlans ?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-13-2017 12:51 PM
Hi all,
I have deployed a Netsight server, a Extreme NAC server and a c5210 wireless controller.
On the Wireless controller side:
I created a WLAN service with authentication mode 802.1x which is using a single radius server (Extreme NAC IA-A-20) for auth & acct.
I also created a role with default action:
Access Control: containment VLAN
VLAN: vlan212
Clicked Advanced >> Added vlan212, vlan300, vlan211 to be used. I have not defined any policy rules.
Then I defined a VNS to bind this WLAN service to this Role when user is authenticated.
On the NAC side:
I added the EWC to access control engine as "Extreme identiFi Wireless".
I created two policy roles. One of them is configured to contain to vlan211 and the other is configured to contain to vlan300.
Note: when I try to enforce domain data to wireless controller, "cannot remove active Role -XXXX- from EWC ..." error occurs.
Then I have tested with two wireless clients. I can see that both clients are assigned to these different NAC profiles successfully. But they are assigned to same vlan212.
Is it possible to assign clients with different NAC profiles to different Vlans on the same SSID ?
Thanks.
I have deployed a Netsight server, a Extreme NAC server and a c5210 wireless controller.
On the Wireless controller side:
I created a WLAN service with authentication mode 802.1x which is using a single radius server (Extreme NAC IA-A-20) for auth & acct.
I also created a role with default action:
Access Control: containment VLAN
VLAN: vlan212
Clicked Advanced >> Added vlan212, vlan300, vlan211 to be used. I have not defined any policy rules.
Then I defined a VNS to bind this WLAN service to this Role when user is authenticated.
On the NAC side:
I added the EWC to access control engine as "Extreme identiFi Wireless".
I created two policy roles. One of them is configured to contain to vlan211 and the other is configured to contain to vlan300.
Note: when I try to enforce domain data to wireless controller, "cannot remove active Role -XXXX- from EWC ..." error occurs.
Then I have tested with two wireless clients. I can see that both clients are assigned to these different NAC profiles successfully. But they are assigned to same vlan212.
Is it possible to assign clients with different NAC profiles to different Vlans on the same SSID ?
Thanks.
13 REPLIES 13
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-13-2017 01:30 PM
Hi Yury,
Firstly, I have to confess that I could not understand how to configure the first method on the wireless controller. Because as I know, a VNS can only bind a WLAN service to only two different Roles (non-authenticated / authenticated).
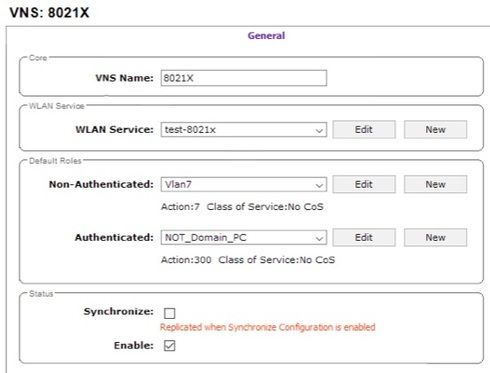
Anyway, I tried my best and deleted all custom made CoS and Roles on the EWC, then enforced domain policies from Netsight successfully. Then I configured the VNS as below:
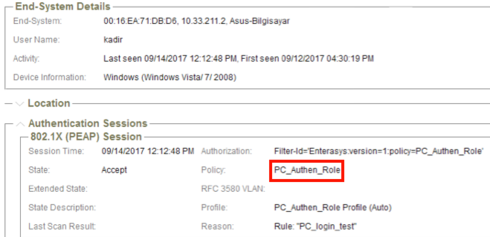
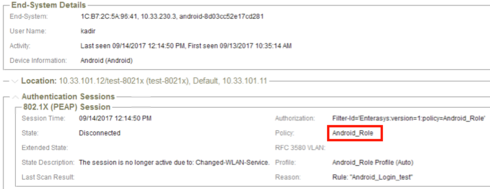
Then, I tested this configuration by connecting two different clients to the same SSID (test-8021x) simultaneously: one of the clients assigned to "Vlan211" and the other assigned to "Vlan311" which are not related to "NOT_Domain_PC" role. They are just assigned to Vlans that NAC sends as radius attributes :
Test client-1 Authentication session:
Test client-2 Authentication session:
I understand from this test that no matter what is chosen in the "Default Roles >> Authenticated" field, clients are assigned according to radius attribute that NAC sends.
Is it right ?
Thanks
Firstly, I have to confess that I could not understand how to configure the first method on the wireless controller. Because as I know, a VNS can only bind a WLAN service to only two different Roles (non-authenticated / authenticated).
Anyway, I tried my best and deleted all custom made CoS and Roles on the EWC, then enforced domain policies from Netsight successfully. Then I configured the VNS as below:
Then, I tested this configuration by connecting two different clients to the same SSID (test-8021x) simultaneously: one of the clients assigned to "Vlan211" and the other assigned to "Vlan311" which are not related to "NOT_Domain_PC" role. They are just assigned to Vlans that NAC sends as radius attributes :
Test client-1 Authentication session:
Test client-2 Authentication session:
I understand from this test that no matter what is chosen in the "Default Roles >> Authenticated" field, clients are assigned according to radius attribute that NAC sends.
Is it right ?
Thanks
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-13-2017 01:30 PM
I will try it tomorrow. Thanks again.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-13-2017 01:30 PM
No , not WLAN service by topology . I meant Role (sometimes refered as Policy). NAC sending back the Filter-ID which is exactly matching the Role name configured on the controller. This role can be bounded to particular Topology (which is the VLAN for you).
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-13-2017 01:14 PM
Hi Yakup ,
You can assing different VLANs in one of this two methods :
- Sending different Policy which bounded to specific topology on the Wireless Controller (e.g. Policy1 on controller configured to "Contain to VLAN100" , Policy2 on controller configured to "Contain to VLAN200" . ) So based on some criteria , ExtremeNAC will send different Policy , then controller will assign different Topology (therefore VLAN) to the user
- Second method is using the same policy , but sending Tunneled Attributes . For doing that , change the "Extreme identiFi Wireless" (when you were adding switch to the NAC) to "RFC3580- VLANID & Extreme IdentiFi Wireless" , in this case together with FilterID (Policy name) the tunneled attributes will come to controller .
You can assing different VLANs in one of this two methods :
- Sending different Policy which bounded to specific topology on the Wireless Controller (e.g. Policy1 on controller configured to "Contain to VLAN100" , Policy2 on controller configured to "Contain to VLAN200" . ) So based on some criteria , ExtremeNAC will send different Policy , then controller will assign different Topology (therefore VLAN) to the user
- Second method is using the same policy , but sending Tunneled Attributes . For doing that , change the "Extreme identiFi Wireless" (when you were adding switch to the NAC) to "RFC3580- VLANID & Extreme IdentiFi Wireless" , in this case together with FilterID (Policy name) the tunneled attributes will come to controller .