This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- RE: Login failed through SNMPv3 - wrong digest
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Login failed through SNMPv3 - wrong digest
Login failed through SNMPv3 - wrong digest
Anonymous
Not applicable
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-21-2018 08:53 AM
Hi
Have an issue where each of the core switches in the network are continually reporting this error in the logs:
Login failed through SNMPv3 - wrong digest (10.23.23.12)
Login failed through SNMPv3 - wrong digest (10.23.23.142)
Those IP addresses listed (10.23.23.12 & 142) are NAC appliances. None of the core switches are configured in NAC switches configuration.
The SNMP configuration on the core switch looks like the following:
configure snmpv3 delete user "admin" engine-id 80:00:07:7c:03:00:04:96:9a:6a:54
configure snmpv3 delete user "initial" engine-id 80:00:07:7c:03:00:04:96:9a:6a:54
configure snmpv3 delete user "initialmd5" engine-id 80:00:07:7c:03:00:04:96:9a:6a:54
configure snmpv3 delete user "initialsha" engine-id 80:00:07:7c:03:00:04:96:9a:6a:54
configure snmpv3 delete user "initialmd5Priv" engine-id 80:00:07:7c:03:00:04:96:9a:6a:54
configure snmpv3 delete user "initialshaPriv" engine-id 80:00:07:7c:03:00:04:96:9a:6a:54
configure snmpv3 delete group "v1v2c_ro" user "v1v2c_ro" sec-model snmpv1
configure snmpv3 delete group "v1v2c_rw" user "v1v2c_rw" sec-model snmpv1
configure snmpv3 delete group "v1v2c_ro" user "v1v2c_ro" sec-model snmpv2c
configure snmpv3 delete group "v1v2c_rw" user "v1v2c_rw" sec-model snmpv2c
configure snmpv3 delete group "admin" user "admin" sec-model usm
configure snmpv3 delete group "initial" user "initial" sec-model usm
configure snmpv3 delete group "initial" user "initialmd5" sec-model usm
configure snmpv3 delete group "initial" user "initialsha" sec-model usm
configure snmpv3 delete group "initial" user "initialmd5Priv" sec-model usm
configure snmpv3 delete group "initial" user "initialshaPriv" sec-model usm
configure snmpv3 delete access "admin" sec-model usm sec-level priv
configure snmpv3 delete access "initial" sec-model usm sec-level noauth
configure snmpv3 delete access "initial" sec-model usm sec-level authnopriv
configure snmpv3 delete access "v1v2c_ro" sec-model snmpv1 sec-level noauth
configure snmpv3 delete access "v1v2c_ro" sec-model snmpv2c sec-level noauth
configure snmpv3 delete access "v1v2c_rw" sec-model snmpv1 sec-level noauth
configure snmpv3 delete access "v1v2c_rw" sec-model snmpv2c sec-level noauth
configure snmpv3 delete access "v1v2cNotifyGroup" sec-model snmpv1 sec-level noauth
configure snmpv3 delete access "v1v2cNotifyGroup" sec-model snmpv2c sec-level noauth
configure snmpv3 delete mib-view "defaultUserView" subtree 1.0
configure snmpv3 delete mib-view "defaultUserView" subtree 1.3.6.1.6.3.16
configure snmpv3 delete mib-view "defaultUserView" subtree 1.3.6.1.6.3.18
configure snmpv3 delete mib-view "defaultUserView" subtree 1.3.6.1.6.3.15.1.2.2.1.4
configure snmpv3 delete mib-view "defaultUserView" subtree 1.3.6.1.6.3.15.1.2.2.1.6
configure snmpv3 delete mib-view "defaultUserView" subtree 1.3.6.1.6.3.15.1.2.2.1.9
configure snmpv3 delete mib-view "defaultNotifyView" subtree 1.0
configure snmpv3 delete community "private"
configure snmpv3 delete community "public"
configure snmpv3 add user "NetSight" engine-id 80:00:07:7c:03:00:04:96:9a:6a:54 authentication sha auth-encrypted localized-key 23??23:b8:23?4c:23:f3:66:35:23:05:30:23:09:60:55:79:23:92:23:ea:44:4d:35:23?23:82 privacy aes 128 privacy-encrypted localized-key 23:cb:58:23:9e:51:23:b0:45:23:d9:6c:23:c1:23??23:86:23:f3:23:eb:23:b3:23:d2:6d
configure snmpv3 add user "NetSight" engine-id 80:00:1f:88:80:2f:51:09:53:4c:29:33:57 authentication sha auth-encrypted localized-key 23:aa:23:1a:23:a6:23:a6:65:23:ae:53:23:c5:47:23:c3:23:b6:33:38:46:30:23:b8:25:34:23:1f:23:d1 privacy aes 128 privacy-encrypted localized-key 23:0e:23:1d:23:f6:23:a5:48:23:ed:23:bf:23:de:23:f5:23:11:5f:23:09:23:8d:27:23:90:23:ea
configure snmpv3 add group "NetAdmin" user "NetSight" sec-model usm
configure snmpv3 add access "NetAdmin" sec-model usm sec-level priv read-view "defaultAdminView" write-view "defaultAdminView" notify-view "defaultAdminView"
configure snmpv3 add target-addr "TV1NetSight" param "TV1NetSight" ipaddress 10.23.23.20 transport-port 162 from 10.255.0.3 vr "VR-Default" tag-list "TVTrapTag"
configure snmpv3 add target-params "TV1NetSight" user "NetSight" mp-model snmpv3 sec-model usm sec-level priv
configure snmpv3 add notify "TVInformTag" tag "TVInformTag" type inform
configure snmpv3 add notify "TVTrapTag" tag "TVTrapTag"
disable snmp access snmp-v1v2c
disable snmpv3 default-group
disable snmpv3 default-user
disable snmp access vr "VR-Mgmt"
Little overkill, but generally just using SNMPv3 which works fine just for traps to be sent to 10.23.23.20, which is Extreme Management.
When I take a packet trace from the NAC appliance (10.23.23.12) I get the following:
Frame 6: 294 bytes on wire (2352 bits), 294 bytes captured (2352 bits)
Ethernet II, Src: ExtremeN_9a:6a:17 (00:04:96:9a:6a:17), Dst: Vmware_3a:43:d0 (00:0c:29:3a:43:d0)
Internet Protocol Version 4, Src: 10.255.0.2, Dst: 10.23.23.20
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
Total Length: 280
Identification: 0x0000 (0)
Flags: 0x02 (Don't Fragment)
Fragment offset: 0
Time to live: 64
Protocol: UDP (17)
Header checksum: 0x0daa [validation disabled]
Source: 10.255.0.2
Destination: 10.23.23.20
[Source GeoIP: Unknown]
[Destination GeoIP: Unknown]
User Datagram Protocol, Src Port: 56970 (56970), Dst Port: 162 (162)
Source Port: 56970
Destination Port: 162
Length: 260
Checksum: 0xdf2c [validation disabled]
[Stream index: 0]
Simple Network Management Protocol
msgVersion: snmpv3 (3)
msgGlobalData
msgID: 508
msgMaxSize: 8192
msgFlags: 03
.... .0.. = Reportable: Not set
.... ..1. = Encrypted: Set
.... ...1 = Authenticated: Set
msgSecurityModel: USM (3)
msgAuthoritativeEngineID: 8000077c030004969a6a17
1... .... = Engine ID Conformance: RFC3411 (SNMPv3)
Engine Enterprise ID: Extreme Networks (1916)
Engine ID Format: MAC address (3)
Engine ID Data: MAC address: ExtremeN_9a:6a:17 (00:04:96:9a:6a:17)
msgAuthoritativeEngineBoots: 42
msgAuthoritativeEngineTime: 602683
msgUserName: NetSight
msgAuthenticationParameters: bc5ee08e1e5cc1d2b2d1a5c9
[Authentication: OK]
[Expert Info (Chat/Checksum): SNMP Authentication OK]
msgPrivacyParameters: 00000000000098e6
msgData: encryptedPDU (1)
encryptedPDU: 8412a3dd665bcdaf76713921a83bafac03569062096d8789...
Decrypted ScopedPDU: 3081a5040b8000077c030004969a6a170400a78193020201...
contextEngineID: 8000077c030004969a6a17
1... .... = Engine ID Conformance: RFC3411 (SNMPv3)
Engine Enterprise ID: Extreme Networks (1916)
Engine ID Format: MAC address (3)
Engine ID Data: MAC address: ExtremeN_9a:6a:17 (00:04:96:9a:6a:17)
contextName:
data: snmpV2-trap (7)
snmpV2-trap
request-id: 424
error-status: noError (0)
error-index: 0
variable-bindings: 6 items
1.3.6.1.2.1.1.3.0: 60283163
Object Name: 1.3.6.1.2.1.1.3.0 (iso.3.6.1.2.1.1.3.0)
Value (Timeticks): 60283163
1.3.6.1.6.3.1.1.4.1.0: 1.3.6.1.6.3.1.1.5.5 (iso.3.6.1.6.3.1.1.5.5)
Object Name: 1.3.6.1.6.3.1.1.4.1.0 (iso.3.6.1.6.3.1.1.4.1.0)
Value (OID): 1.3.6.1.6.3.1.1.5.5 (iso.3.6.1.6.3.1.1.5.5)
1.3.6.1.4.1.1916.1.1.1.30.0: 10.23.23.12
Object Name: 1.3.6.1.4.1.1916.1.1.1.30.0 (iso.3.6.1.4.1.1916.1.1.1.30.0)
Value (IpAddress): 10.23.23.12
1.3.6.1.4.1.1916.1.1.1.50.0:
Object Name: 1.3.6.1.4.1.1916.1.1.1.50.0 (iso.3.6.1.4.1.1916.1.1.1.50.0)
Value (Integer32): 1
1.3.6.1.4.1.1916.1.1.1.51.0: 0a17170c
Object Name: 1.3.6.1.4.1.1916.1.1.1.51.0 (iso.3.6.1.4.1.1916.1.1.1.51.0)
Value (OctetString): 0a17170c
1.3.6.1.4.1.1916.1.1.1.52.0: 56522d44656661756c74
Object Name: 1.3.6.1.4.1.1916.1.1.1.52.0 (iso.3.6.1.4.1.1916.1.1.1.52.0)
Value (OctetString): 56522d44656661756c74
So the packet is from the core switch itself on IP 10.255.0.2 to NetSight on 10.23.23.20 as you expect.
What I don't understand are the OIDs showing authentication failures to the NAC IP of 10.23.23.12 using SNMPv2-trap?
I'm not sure why that's being sent by the switch?
This is the packet capture I was running on the NAC device 10.23.23.12:
tcpdump -vvv -i eth0 port 162 -w snmp.pcap
The only packets it collects are similar to the one shown above.
Any ideas?
Many thanks in advance
Have an issue where each of the core switches in the network are continually reporting this error in the logs:
Those IP addresses listed (10.23.23.12 & 142) are NAC appliances. None of the core switches are configured in NAC switches configuration.
The SNMP configuration on the core switch looks like the following:
configure snmpv3 delete user "admin" engine-id 80:00:07:7c:03:00:04:96:9a:6a:54
configure snmpv3 delete user "initial" engine-id 80:00:07:7c:03:00:04:96:9a:6a:54
configure snmpv3 delete user "initialmd5" engine-id 80:00:07:7c:03:00:04:96:9a:6a:54
configure snmpv3 delete user "initialsha" engine-id 80:00:07:7c:03:00:04:96:9a:6a:54
configure snmpv3 delete user "initialmd5Priv" engine-id 80:00:07:7c:03:00:04:96:9a:6a:54
configure snmpv3 delete user "initialshaPriv" engine-id 80:00:07:7c:03:00:04:96:9a:6a:54
configure snmpv3 delete group "v1v2c_ro" user "v1v2c_ro" sec-model snmpv1
configure snmpv3 delete group "v1v2c_rw" user "v1v2c_rw" sec-model snmpv1
configure snmpv3 delete group "v1v2c_ro" user "v1v2c_ro" sec-model snmpv2c
configure snmpv3 delete group "v1v2c_rw" user "v1v2c_rw" sec-model snmpv2c
configure snmpv3 delete group "admin" user "admin" sec-model usm
configure snmpv3 delete group "initial" user "initial" sec-model usm
configure snmpv3 delete group "initial" user "initialmd5" sec-model usm
configure snmpv3 delete group "initial" user "initialsha" sec-model usm
configure snmpv3 delete group "initial" user "initialmd5Priv" sec-model usm
configure snmpv3 delete group "initial" user "initialshaPriv" sec-model usm
configure snmpv3 delete access "admin" sec-model usm sec-level priv
configure snmpv3 delete access "initial" sec-model usm sec-level noauth
configure snmpv3 delete access "initial" sec-model usm sec-level authnopriv
configure snmpv3 delete access "v1v2c_ro" sec-model snmpv1 sec-level noauth
configure snmpv3 delete access "v1v2c_ro" sec-model snmpv2c sec-level noauth
configure snmpv3 delete access "v1v2c_rw" sec-model snmpv1 sec-level noauth
configure snmpv3 delete access "v1v2c_rw" sec-model snmpv2c sec-level noauth
configure snmpv3 delete access "v1v2cNotifyGroup" sec-model snmpv1 sec-level noauth
configure snmpv3 delete access "v1v2cNotifyGroup" sec-model snmpv2c sec-level noauth
configure snmpv3 delete mib-view "defaultUserView" subtree 1.0
configure snmpv3 delete mib-view "defaultUserView" subtree 1.3.6.1.6.3.16
configure snmpv3 delete mib-view "defaultUserView" subtree 1.3.6.1.6.3.18
configure snmpv3 delete mib-view "defaultUserView" subtree 1.3.6.1.6.3.15.1.2.2.1.4
configure snmpv3 delete mib-view "defaultUserView" subtree 1.3.6.1.6.3.15.1.2.2.1.6
configure snmpv3 delete mib-view "defaultUserView" subtree 1.3.6.1.6.3.15.1.2.2.1.9
configure snmpv3 delete mib-view "defaultNotifyView" subtree 1.0
configure snmpv3 delete community "private"
configure snmpv3 delete community "public"
configure snmpv3 add user "NetSight" engine-id 80:00:07:7c:03:00:04:96:9a:6a:54 authentication sha auth-encrypted localized-key 23??23:b8:23?4c:23:f3:66:35:23:05:30:23:09:60:55:79:23:92:23:ea:44:4d:35:23?23:82 privacy aes 128 privacy-encrypted localized-key 23:cb:58:23:9e:51:23:b0:45:23:d9:6c:23:c1:23??23:86:23:f3:23:eb:23:b3:23:d2:6d
configure snmpv3 add user "NetSight" engine-id 80:00:1f:88:80:2f:51:09:53:4c:29:33:57 authentication sha auth-encrypted localized-key 23:aa:23:1a:23:a6:23:a6:65:23:ae:53:23:c5:47:23:c3:23:b6:33:38:46:30:23:b8:25:34:23:1f:23:d1 privacy aes 128 privacy-encrypted localized-key 23:0e:23:1d:23:f6:23:a5:48:23:ed:23:bf:23:de:23:f5:23:11:5f:23:09:23:8d:27:23:90:23:ea
configure snmpv3 add group "NetAdmin" user "NetSight" sec-model usm
configure snmpv3 add access "NetAdmin" sec-model usm sec-level priv read-view "defaultAdminView" write-view "defaultAdminView" notify-view "defaultAdminView"
configure snmpv3 add target-addr "TV1NetSight" param "TV1NetSight" ipaddress 10.23.23.20 transport-port 162 from 10.255.0.3 vr "VR-Default" tag-list "TVTrapTag"
configure snmpv3 add target-params "TV1NetSight" user "NetSight" mp-model snmpv3 sec-model usm sec-level priv
configure snmpv3 add notify "TVInformTag" tag "TVInformTag" type inform
configure snmpv3 add notify "TVTrapTag" tag "TVTrapTag"
disable snmp access snmp-v1v2c
disable snmpv3 default-group
disable snmpv3 default-user
disable snmp access vr "VR-Mgmt"
Little overkill, but generally just using SNMPv3 which works fine just for traps to be sent to 10.23.23.20, which is Extreme Management.
When I take a packet trace from the NAC appliance (10.23.23.12) I get the following:
Frame 6: 294 bytes on wire (2352 bits), 294 bytes captured (2352 bits)
Ethernet II, Src: ExtremeN_9a:6a:17 (00:04:96:9a:6a:17), Dst: Vmware_3a:43:d0 (00:0c:29:3a:43:d0)
Internet Protocol Version 4, Src: 10.255.0.2, Dst: 10.23.23.20
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
Total Length: 280
Identification: 0x0000 (0)
Flags: 0x02 (Don't Fragment)
Fragment offset: 0
Time to live: 64
Protocol: UDP (17)
Header checksum: 0x0daa [validation disabled]
Source: 10.255.0.2
Destination: 10.23.23.20
[Source GeoIP: Unknown]
[Destination GeoIP: Unknown]
User Datagram Protocol, Src Port: 56970 (56970), Dst Port: 162 (162)
Source Port: 56970
Destination Port: 162
Length: 260
Checksum: 0xdf2c [validation disabled]
[Stream index: 0]
Simple Network Management Protocol
msgVersion: snmpv3 (3)
msgGlobalData
msgID: 508
msgMaxSize: 8192
msgFlags: 03
.... .0.. = Reportable: Not set
.... ..1. = Encrypted: Set
.... ...1 = Authenticated: Set
msgSecurityModel: USM (3)
msgAuthoritativeEngineID: 8000077c030004969a6a17
1... .... = Engine ID Conformance: RFC3411 (SNMPv3)
Engine Enterprise ID: Extreme Networks (1916)
Engine ID Format: MAC address (3)
Engine ID Data: MAC address: ExtremeN_9a:6a:17 (00:04:96:9a:6a:17)
msgAuthoritativeEngineBoots: 42
msgAuthoritativeEngineTime: 602683
msgUserName: NetSight
msgAuthenticationParameters: bc5ee08e1e5cc1d2b2d1a5c9
[Authentication: OK]
[Expert Info (Chat/Checksum): SNMP Authentication OK]
msgPrivacyParameters: 00000000000098e6
msgData: encryptedPDU (1)
encryptedPDU: 8412a3dd665bcdaf76713921a83bafac03569062096d8789...
Decrypted ScopedPDU: 3081a5040b8000077c030004969a6a170400a78193020201...
contextEngineID: 8000077c030004969a6a17
1... .... = Engine ID Conformance: RFC3411 (SNMPv3)
Engine Enterprise ID: Extreme Networks (1916)
Engine ID Format: MAC address (3)
Engine ID Data: MAC address: ExtremeN_9a:6a:17 (00:04:96:9a:6a:17)
contextName:
data: snmpV2-trap (7)
snmpV2-trap
request-id: 424
error-status: noError (0)
error-index: 0
variable-bindings: 6 items
1.3.6.1.2.1.1.3.0: 60283163
Object Name: 1.3.6.1.2.1.1.3.0 (iso.3.6.1.2.1.1.3.0)
Value (Timeticks): 60283163
1.3.6.1.6.3.1.1.4.1.0: 1.3.6.1.6.3.1.1.5.5 (iso.3.6.1.6.3.1.1.5.5)
Object Name: 1.3.6.1.6.3.1.1.4.1.0 (iso.3.6.1.6.3.1.1.4.1.0)
Value (OID): 1.3.6.1.6.3.1.1.5.5 (iso.3.6.1.6.3.1.1.5.5)
1.3.6.1.4.1.1916.1.1.1.30.0: 10.23.23.12
Object Name: 1.3.6.1.4.1.1916.1.1.1.30.0 (iso.3.6.1.4.1.1916.1.1.1.30.0)
Value (IpAddress): 10.23.23.12
1.3.6.1.4.1.1916.1.1.1.50.0:
Object Name: 1.3.6.1.4.1.1916.1.1.1.50.0 (iso.3.6.1.4.1.1916.1.1.1.50.0)
Value (Integer32): 1
1.3.6.1.4.1.1916.1.1.1.51.0: 0a17170c
Object Name: 1.3.6.1.4.1.1916.1.1.1.51.0 (iso.3.6.1.4.1.1916.1.1.1.51.0)
Value (OctetString): 0a17170c
1.3.6.1.4.1.1916.1.1.1.52.0: 56522d44656661756c74
Object Name: 1.3.6.1.4.1.1916.1.1.1.52.0 (iso.3.6.1.4.1.1916.1.1.1.52.0)
Value (OctetString): 56522d44656661756c74
So the packet is from the core switch itself on IP 10.255.0.2 to NetSight on 10.23.23.20 as you expect.
What I don't understand are the OIDs showing authentication failures to the NAC IP of 10.23.23.12 using SNMPv2-trap?
I'm not sure why that's being sent by the switch?
This is the packet capture I was running on the NAC device 10.23.23.12:
tcpdump -vvv -i eth0 port 162 -w snmp.pcap
The only packets it collects are similar to the one shown above.
Any ideas?
Many thanks in advance
3 REPLIES 3
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-21-2018 10:37 AM
you welcome , i have been wondering similarly earlier 🙂
glad i was able to help.
glad i was able to help.
Anonymous
Not applicable
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-21-2018 10:21 AM
Hi Ahmed,
Thanks for posting.... think you might be spot on there!
Should have captured on 161 and I might have seen and understood the request from NAC 🙂
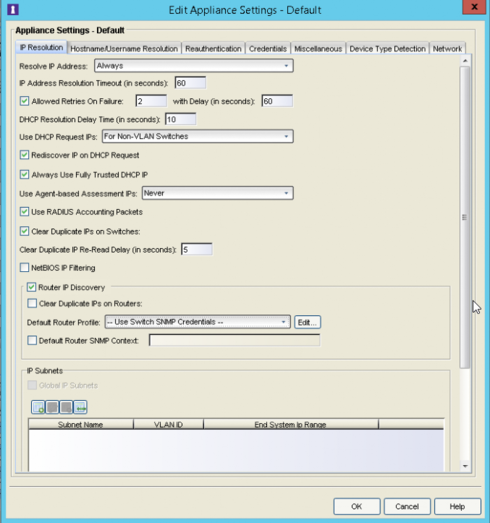
Checked the setting and was set too --Use Switch SNMP Credentials--, so changed it to match the actual credentials I use for the switches, and as of yet not see this message popup in the logs.
Nice one, thanks for the help 🙂
Thanks for posting.... think you might be spot on there!
Should have captured on 161 and I might have seen and understood the request from NAC 🙂
Checked the setting and was set too --Use Switch SNMP Credentials--, so changed it to match the actual credentials I use for the switches, and as of yet not see this message popup in the logs.
Nice one, thanks for the help 🙂
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-21-2018 10:04 AM
I think this is related to IP Router Discovery part of NAC IP resolution.
NAC will connect to the default gateway to try to resolve the IP of the end system, and i think it will use port 161 not 162 , 162 is the port used for SNMP trap.
NAC will connect to the default gateway to try to resolve the IP of the end system, and i think it will use port 161 not 162 , 162 is the port used for SNMP trap.