- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ
- Set up separate public WIFI with separate IP range
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Set up separate public WIFI with separate IP range
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-18-2021 03:13 PM
We are installing APs for Public access. We need to keep these clients off our native network. We also need them to be able to surf internet only. How best to do this?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-19-2021 01:51 PM
I would recommend setting up a Guest VLAN so your guests are in a different IP pool than any internal users. You can either do this on your own network DHCP server outside of ExtremeCloud IQ (XIQ), or you can set up a DHCP server on an AP. This guide reviews how to set up a DHCP server on an AP in XIQ: https://extremeportal.force.com/ExtrArticleDetail?an=000079335&q=DHCP%20XIQ
Once you have the guests on their own VLAN, you’ll want to apply the guest internet access only IP firewall object, which will restrict users on the Guest SSID to external IP addresses only, and blocks all internal addresses. To do this you’ll want to go to Configure> Open the Network Policy in question> Open/Create the Guest SSID> Scroll down to the User Access Settings section within the SSID> Find the Default User Profile line and either create a new user profile or edit the one you’re currently using. Note that if you’re currently using a pre-build default user profile that came with XIQ, you won’t be able to edit that profile and you’ll have to create a new one.
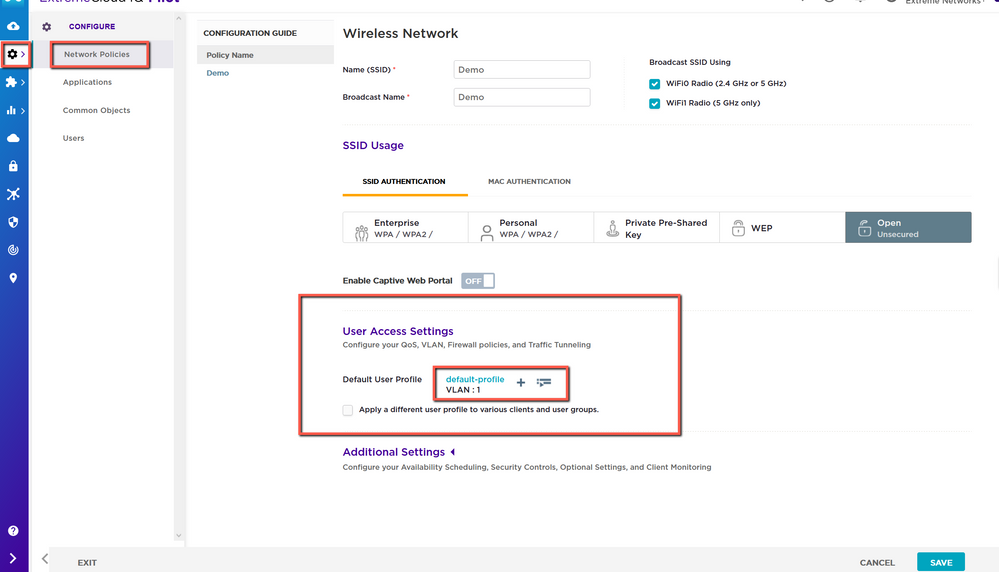
In the User Profile settings, confirm you’ve set it to the Guest VLAN. Then go to the Security tab and toggle Firewall Rules to ON. Click on the list icon to view pre-built IP firewall Policies.
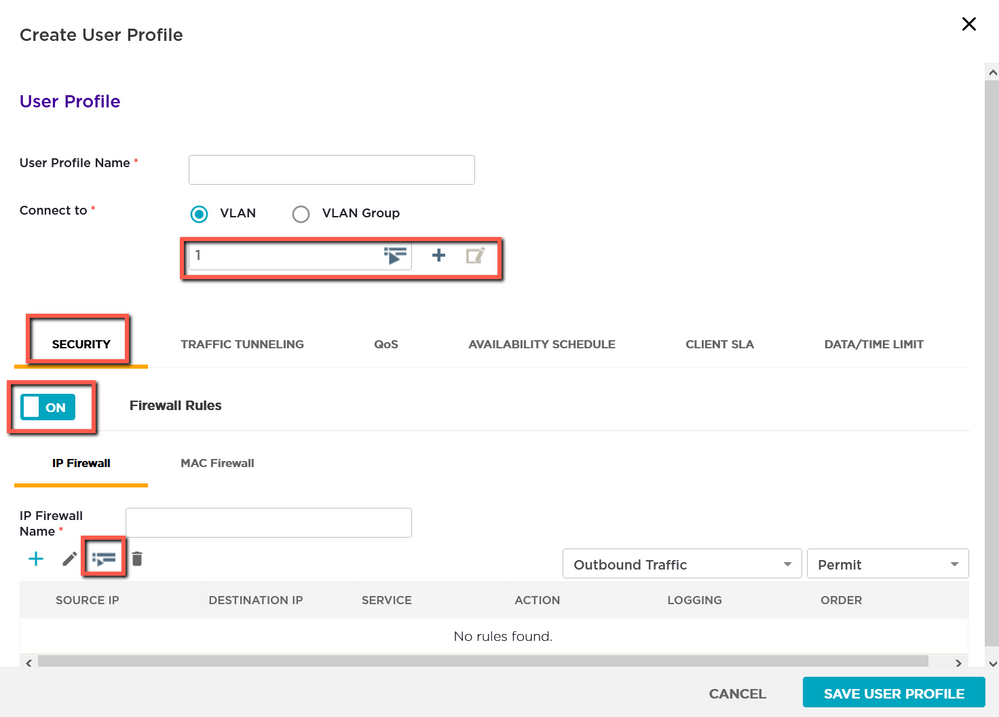
In the list you should see an object called Guest-Internet-Access-Only, check the box next to that item and click Select IP Firewall.
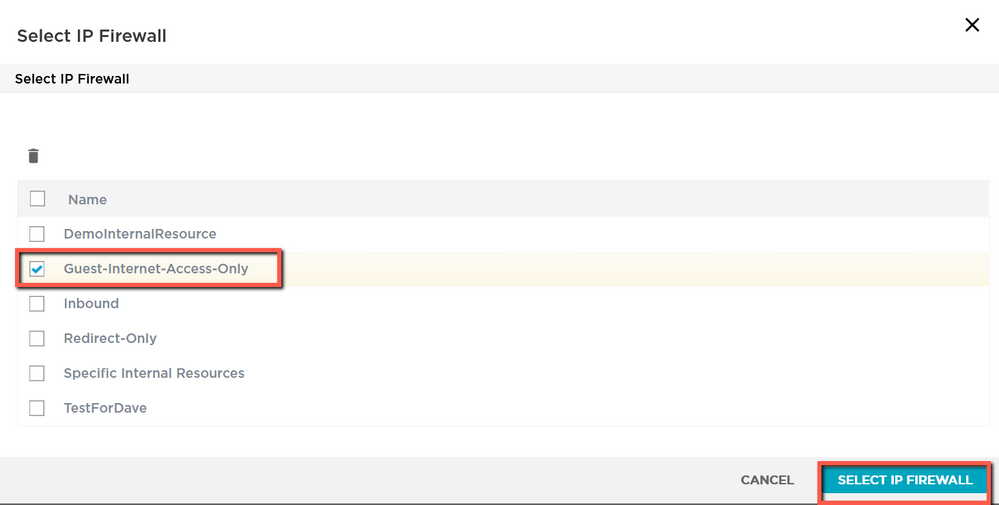
You should see the new rules listed in the Security tab now; these rules allow DHCP and DNS traffic, and blocks all traffic going to any internal address. All other traffic, in this case traffic headed to external IP addresses, is allowed. Save the User Profile, save the SSID, and then when you are ready push a configuration update out to all of your APs. This will require a reboot of the AP, which in turn will cause a brief drop in traffic, just so you are prepared.
Please let me know if I can clarify anything!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-19-2021 01:51 PM
I would recommend setting up a Guest VLAN so your guests are in a different IP pool than any internal users. You can either do this on your own network DHCP server outside of ExtremeCloud IQ (XIQ), or you can set up a DHCP server on an AP. This guide reviews how to set up a DHCP server on an AP in XIQ: https://extremeportal.force.com/ExtrArticleDetail?an=000079335&q=DHCP%20XIQ
Once you have the guests on their own VLAN, you’ll want to apply the guest internet access only IP firewall object, which will restrict users on the Guest SSID to external IP addresses only, and blocks all internal addresses. To do this you’ll want to go to Configure> Open the Network Policy in question> Open/Create the Guest SSID> Scroll down to the User Access Settings section within the SSID> Find the Default User Profile line and either create a new user profile or edit the one you’re currently using. Note that if you’re currently using a pre-build default user profile that came with XIQ, you won’t be able to edit that profile and you’ll have to create a new one.

In the User Profile settings, confirm you’ve set it to the Guest VLAN. Then go to the Security tab and toggle Firewall Rules to ON. Click on the list icon to view pre-built IP firewall Policies.

In the list you should see an object called Guest-Internet-Access-Only, check the box next to that item and click Select IP Firewall.

You should see the new rules listed in the Security tab now; these rules allow DHCP and DNS traffic, and blocks all traffic going to any internal address. All other traffic, in this case traffic headed to external IP addresses, is allowed. Save the User Profile, save the SSID, and then when you are ready push a configuration update out to all of your APs. This will require a reboot of the AP, which in turn will cause a brief drop in traffic, just so you are prepared.
Please let me know if I can clarify anything!
