- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeControl
- checking ldap user and radius attribute on NAC Aut...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
checking ldap user and radius attribute on NAC Authentication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-11-2021 02:34 PM
Hi,
I’m currently on a migration process from Microsoft NPS to Extreme Control.
We have a Cisco ASA as VPN-Gateway.
I will authenticate VPN-Users and Mgmt-Logins.
In the past we separate this with different “called-station-id” values.
Can I realize this with NAC? AFAIK I can’t check/match LDAP-Criteria (LDAP-User-Group) and Radius-Attribute (Radius-User-Group) at the same time.
Or Is there a way to realize this?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-12-2021 02:47 PM
Hi Mig, Peter,
just thinking loud, I suspect it would be possible to use User Group with LDAP/RADIUS lookups and End-System Group with LDAP lookups configured in a way that still a user is looked up…?
Hope that helps,
Tomasz
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-11-2021 03:28 PM
Hi Mig,
thanks for your answer.
I will have both 1 and 2 (not at the same time).
On the current NPS I check:
- NAS-IP (in both cases the same)
- the ldap-user-group (different groups, but a user can be member of both groups
- called-station-id (in case of VPN - value is WAN-IP; in case of mgmt its LAN-IP)
But in general, can I check/match/validate LDAP and Radius Information from Radius-Request at the same time?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-11-2021 03:22 PM
Hi Peter,
Something is still unclear.
You want to
- Authenticate VPN users with authentication requests coming from the ASA
- Authenticate admin users loging into ASA?
If 2 is correct, the authentication request will be different in terms of inbound radius attributes and should be treated as such by Control.
Here an abstract of the event log of Control for a login on the switches:
This is an administrative request because Calling-Station-Id is not present
What attributes and values are you checking on your existing system?
Mig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-11-2021 03:12 PM
Hi Mig,
thanks for your answer, but this does not really helps.
Mgmt-Login for XOS Switches is no problem.
I will authenticate users for vpn-login und mgmt-login from Cisco ASA.
So, the source-IP is the same. So I need something to select. In the ASA we have different values which are send in Radius Request as called-station-id to the NAC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-11-2021 02:40 PM
PeterK,
Here a screenshot on how I manage Mgmt logins on Control for ERS/VSP switches.
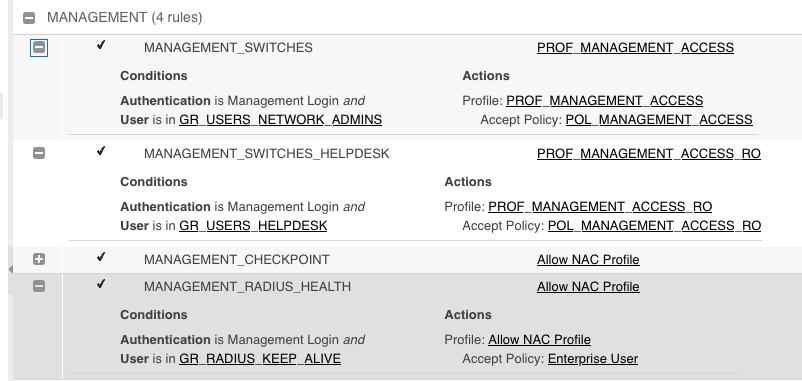
For the VPN users, you can validate them on the location (originated on the VPN concentrator and User-Groups).
Regards
Mig
