- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeControl
- Re: Provide VLAN and ISID without policy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Provide VLAN and ISID without policy
Provide VLAN and ISID without policy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-26-2022 05:41 AM
I want dynamic VLAN and ISID assignment without using a policy.
So the switch gets the VLAN AND the ISID dynamically.
At which point I have to configure the ISID?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-08-2025 01:06 AM - edited 10-09-2025 01:54 AM
To provide a VLAN and ISID (Instance ID) without a policy, you can use a command-line interface (CLI) to manually configure the fabric attach (FA) attributes, which maps the VLAN to the ISID. Alternatively, you can write a custom UPM profile with a script to trigger the mapping, though this is a more complex workaround for platforms like Extreme Networks. Seminole County Clerk of Court
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-31-2022 05:10 PM - edited 08-31-2022 05:14 PM
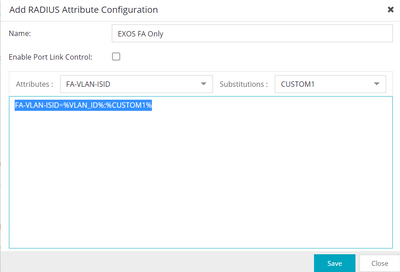
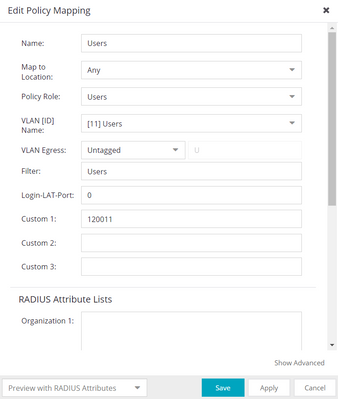
Just use proper radius attribute
Attach new "Radius attributes to send" config to EXOS switch.
Then in NAC Profile add ISID number to Custom1 field:
Of course you can remove ISID from Policy config and still use Policy with conjunction to FA (eg. for traffic filtering)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-28-2025 04:40 AM - edited 07-28-2025 04:41 AM
Hi Apologies for bringing up old post but this is sort of what i'm looking for to answer something in 2025 🙂 but if i was mapping untagged and tagged vlans to a port (such as 3rd party access point with multiple SSID's) how do you achieve multiple dynamic VLAN and I-SID mappings with exos and FA? do you have an example? thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-28-2025 05:52 AM - edited 07-28-2025 06:20 AM
Best option is to use multiple FA-VLAN-ISIDs but you need EXOS 33.2. With that version you can use multiple VLAN:ISID mappings:
FA-VLAN-ISID="10:120010,11:120011,123:120123"
The first VLAN:NSI entry specified is the PVID vlan and the other vlans as egress VLANs
If you don't have EXOS 33.2 then Policy is the only sensible way.
Policy with control "Permit" and VLAN Egress definitions for tagged vlans only.
NAC would respond with Policy name with Filter-ID and FA-VLAN-ISID for untagged traffic.
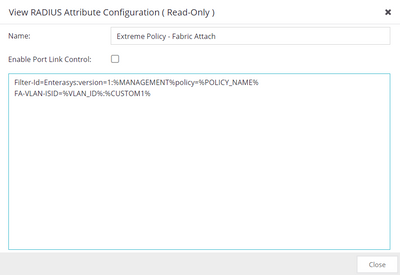
Example:
Filter-Id=Enterasys:version=1:policy=ACCESS-POINT
FA-VLAN-ISID=11:120011
ACCESS-POINT Policy profile includes "Permit" permission and only "tagged" VLANs (in VLAN Egress tab in Policy Manager)
FA-VLAN-ISID would set up untagged vlan 11 and i-sid 120011
There is a drawback - tagged vlans will not be FA-signalled on uplink port. If you want such behavior and you want to have it automated, then you can use i-sid offset option
# configure fabric attach isid-nsi-offset <number>
In such case dynamic VLANs can have i-sid auto assigned by switch itself. Eg when you would configure:
# configure fabric attach isid-nsi-offset 120000
When dynamic VLAN is created based on Radius response then switch would map it to i-sid adding vlan to offset. For example if vlan would be 100 then i-sid would be 120100 (as per example)
You can also create a python script which will be triggered by UPM and would install all needed fa mappings. Unfortunately distribution of the script to all switches could be the different issue. In one word it is complicated so I don't recommend go that way.
One very important thing. When you would use Policy, there is an option to enable "AP Aware" feature on Policy profile. This feature would disable consecutive auth requests on the port when AP Aware Policy is applied. It is hugely important to avoid double auth requests for same user/endpoint. Why double? First one would come from WiFi and then, once the endpoint is permitted by WIFi, second session would come from a switch port. It's because port itself is netlogin-enabled to authenticate access point.