- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeControl
- Re: Several sites, with every site the same rules,...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Several sites, with every site the same rules, but different vlans send back. How to set this up.
Several sites, with every site the same rules, but different vlans send back. How to set this up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-19-2022 08:26 AM
Hi,
I have to configure NAC for a company which has several sites. We did this before with Identity Engine (Ignition Server).
The company has several sites, where we want every computer to authenticate wireless (ap's controlled by VE6120) through Extreme control.
Most of the sites have the same rules, but with different vlans send back, because of other vlans used in another site.
My question is, how do I have to configure NAC to become this?
- How does NAC know which rule must be hitted from which site? making groups of serial numbers of the AP's belonging to that site? hope not...;-)
- Do I have to create every rule for every site?
Thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-09-2022 12:04 PM
Hello,
There are many different ways to accomplish this goal depending on how many sites and how complex you would like the rules/configuration to be.
If you have a large number of sites in which you need to send different AVPs back for RADIUS I would recommend that you use the location based policy mappings combined with called-station-ID injection on the VE6120.
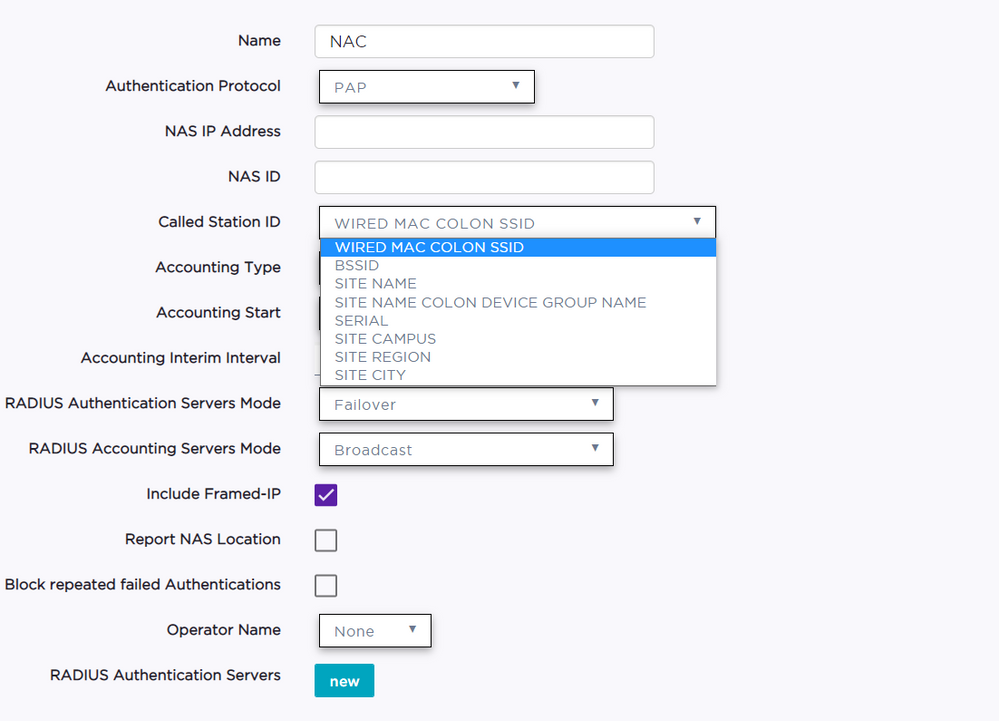
Called-Station-ID injection: In the AAA policy configured on the WLAN in the VE6120 there is a "Called Station ID" field with the following options:
What this feature will do for you is replace the called-station-id RADIUS AVP with a location identifier you can use in Control to identify that a different accept AVP needs to be returned.
If you have split up your Sites within XCC you can send a different site name in each of those locations. You can get as granular as "Site Name: Device Group" so potentially Control can even identify a different location based on the names of the device groups within each site.
Control reads the replaced called station ID and extracts the value and treats it as "AP_ZONE", which is used as part of the "AP ID" section of the location groups. It then replaces the called-station-ID with the SIemen's BSSID MAC which is sent in a 3rd party AVP sent by default by the VE6120 so no information is lost by using the called-station-ID injection.
Location Based Policy Mappings:
By utilizing the called-station-ID injection above Control can identify locations without having to create lists of IPs/AP Names/Serial Numbers. There are a few different ways that you can now utilize this location criteria to send change which Accept AVP is used.
You could build a new rule per location to send the new VLAN AVP, but if you have a large number of locations there may be a better way.
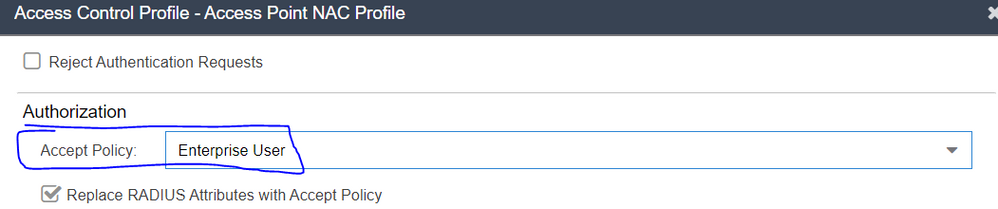
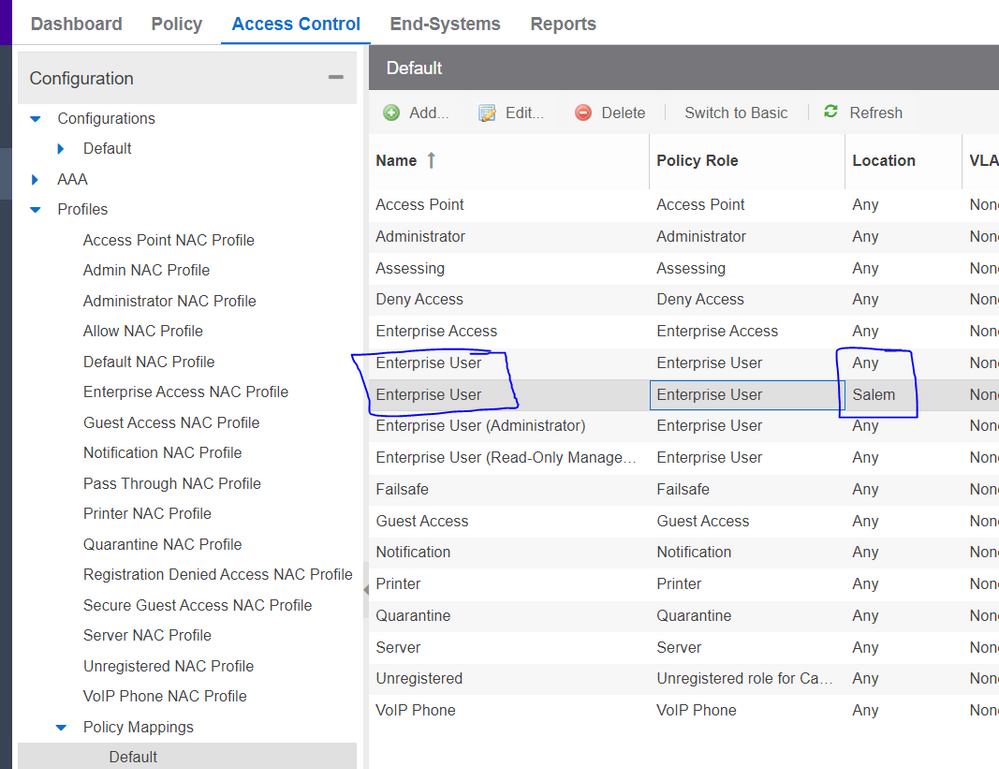
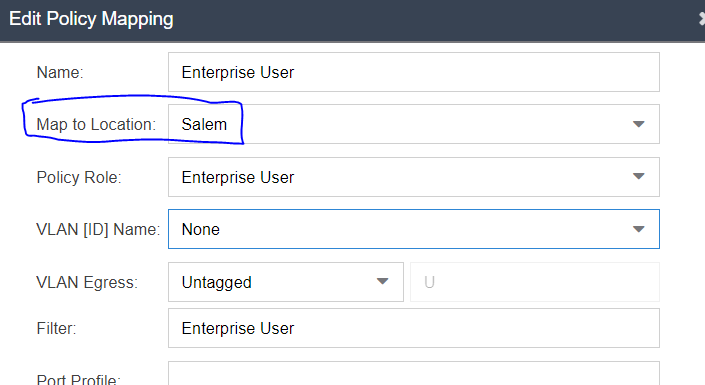
In Control within each rule there is a profile, and each profile has a policy mapping. What you can do is define multiple policy mappings with the same name, but change the "Map to Location" field to use the new location based groups you created based on the above CSI injection.
The profile specifics a specific policy mapping:
You create multiple mappings with the same name, but a different location group:
And then can customize AVPs per location within the new mapping:
You would create a new policy mapping with the same name, a unique location, and the rest of the mapping can be completely customized to suit your needs.
The end systems would all hit a single rule, be assigned a single profile that could have many different policy mappings based on location needs.
This is a very common component of larger systems that have been segmented and is a very robust solution. The APs themselves will not need to be managed as the VE6120 will automatically inject CSI based on device group/site identification so no lists of APs to continually be managed.
Hybrid Mode:
There is also another variation on the above that you could utilize called Hybrid mode which is supported on the VE6120. In the above part of the deployment if you were using filter-id to send a policy name is you would need to create a unique policy role in XCC to "Contain to VLAN" and send that unique policy role in the filter-ID. If there are a large amount of policy rules, or very large amount of segmented areas the number of policy roles could get very large.
EG. 10 rules per site and 10 sites requiring unique VLANs would results in 100 unique policy roles.
Hybrid mode allows you to define a policy and a VLAN separately for each authentication.
You could use the same global level policy role with generic rules and utilize the location based CSI injection and location based policy to send a custom RFC 3580 VLAN authorization along with a Filter-ID role to have a single role used network wide, and change VLAN only.
The disadvantage of this configuration is that the single role now controls which services devices get network wide. Use of granular rules for a specific issue or requirement for one site will now be applied every where. So if you don't use policy rules to control traffic but do it through an ACL or firewall this might be a good solution.
Control is very flexible and there are many ways to accomplish what you're trying to setup, the hard part would be determining which of the available solutions would be best fit for your environment.
Thanks
-Ryan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-08-2022 06:00 AM