This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (ERS)
- Re: MHSA/MHMA automation
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
MHSA/MHMA automation
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-04-2022 06:07 AM
Hi,
We're deploying NAC in an existing network of mainly ERS49XX and ERS48XX switches.
On these ERS switches, one needs to specify if a port needs to be in MHSA or MHMA mode.
For example:
Thanks!
We're deploying NAC in an existing network of mainly ERS49XX and ERS48XX switches.
On these ERS switches, one needs to specify if a port needs to be in MHSA or MHMA mode.
For example:
- our access points need MHSA (AP authenticates, connected clients do not since they're authenticated elsewhere)
- IP phones need MHMA: both the phone and the connected PC need to authenticate
Thanks!
Solved! Go to Solution.
1 ACCEPTED SOLUTION
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-05-2022 04:46 AM
Fijs,
On ERS 4900 as from 7.9.1:
 Here for the ZTC for ERS:
Here for the ZTC for ERS:
 I suggest you to read the doc ConfigFabConERS49005900_7.8.1_CG.pdf
I suggest you to read the doc ConfigFabConERS49005900_7.8.1_CG.pdf
Mig
On ERS 4900 as from 7.9.1:
 Here for the ZTC for ERS:
Here for the ZTC for ERS: I suggest you to read the doc ConfigFabConERS49005900_7.8.1_CG.pdf
I suggest you to read the doc ConfigFabConERS49005900_7.8.1_CG.pdfMig
6 REPLIES 6
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-11-2022 12:26 PM
Ah, yes, good point. Both approaches work with Extreme APs (Fabric Attach enabled) but if you have non-Extreme WLAN APs then you need the RADIUS MHSA attribute... or you do manual config...or even better you use Extreme WLAN !
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-11-2022 10:42 AM
Unfortunately the AP's in this case are not Extreme AP's.
So for the 49XX, an upgrade will do the trick.
For the 48XX, we'll have to manually change to MHSA for AP ports.
So for the 49XX, an upgrade will do the trick.
For the 48XX, we'll have to manually change to MHSA for AP ports.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-11-2022 06:43 AM
Got this unicast question: is this implemented also on the latest firmware for the ERS48xx series?
Replying on thread for everyone's benefit.
So the fa zero-touch-option auto-port-mode-fa-client client-type 6 is also available on ERS4800.
Whereas the new MHSA RADIUS attribute support is only on ERS5900/4900 & 3600:
Replying on thread for everyone's benefit.
So the fa zero-touch-option auto-port-mode-fa-client client-type 6 is also available on ERS4800.
Whereas the new MHSA RADIUS attribute support is only on ERS5900/4900 & 3600:
ERS5900
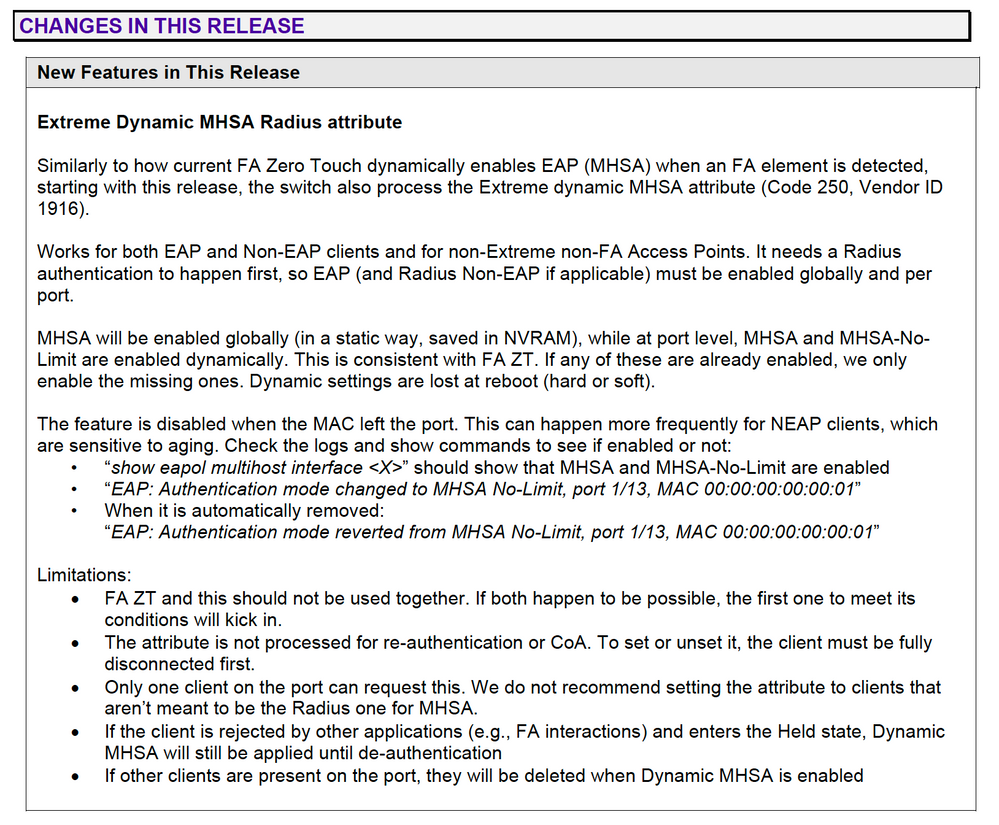
7.9.1 SW Extreme Dynamic MHSA RADIUS vendor specific attribute (VSA) Extreme-Dynamic-MHSA (vendor ID 1916 value 250)
ERS4900
7.9.1 SW Extreme Dynamic MHSA RADIUS vendor specific attribute (VSA) Extreme-Dynamic-MHSA (vendor ID 1916 value 250)
ERS3600
6.5.3 SW Extreme Dynamic MHSA RADIUS vendor specific attribute (VSA) Extreme-Dynamic-MHSA (vendor ID 1916 value 250)
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-06-2022 09:28 AM
So the answer above from Miguel is correct; as of 7.9.1 release you can now enable MHSA on the port via a RADIUS attribute (the same that VOSS uses).
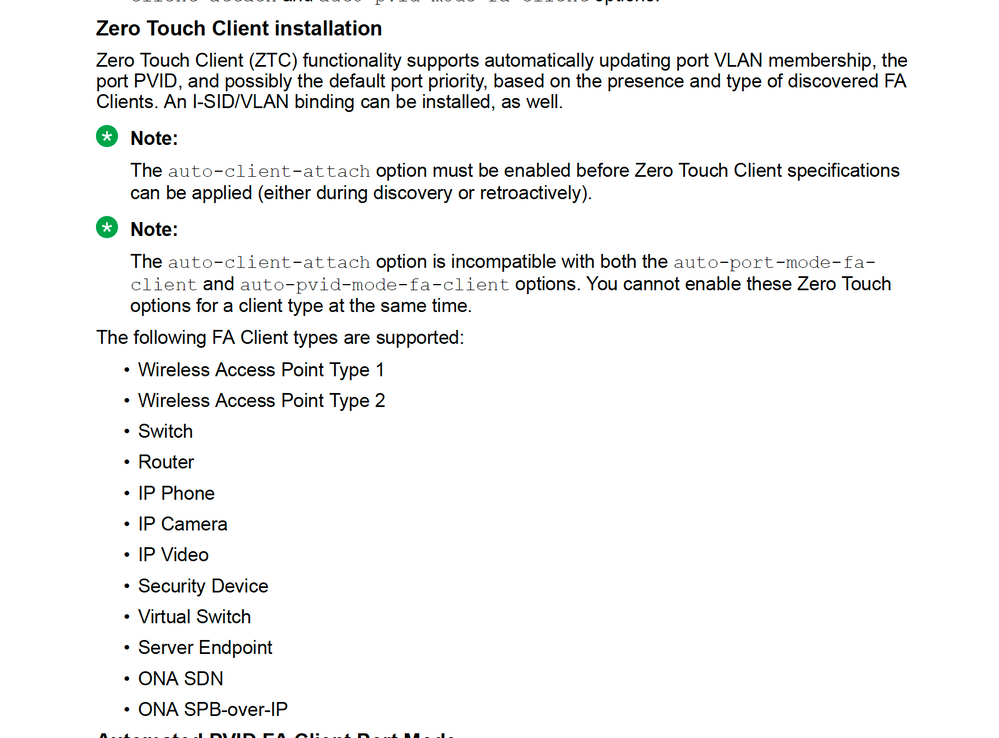
However, for completeness, there is also the "old" ERS approach which is still possible, which is based around FA zero-touch-options.
If you enable this command for FA Client type 6 = (WAP-type1):
fa zero-touch-option auto-port-mode-fa-client client-type 6
However, for completeness, there is also the "old" ERS approach which is still possible, which is based around FA zero-touch-options.
If you enable this command for FA Client type 6 = (WAP-type1):
fa zero-touch-option auto-port-mode-fa-client client-type 6
- auto-port-mode-fa-client: When this option is activated for certain FA Client types, whenever an FA client of that type is discovered on an access port, the access port is automatically pre-configured for EAP/NEAP in mode Multiple-Hosts-Single-Authentication (MHSA). The FA Client will thus need to authenticate against a RADIUS server using either EAPoL or RADIUS MAC-based authentication (NEAP).
