- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- RE: Floating Default Route vs Flow Redirect
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Floating Default Route vs Flow Redirect
Floating Default Route vs Flow Redirect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-23-2017 08:31 AM
Hi,
Currently working on integrating a legacy Cisco network with Extreme, where the default route for the interim is to send all traffic into the legacy Cisco network.
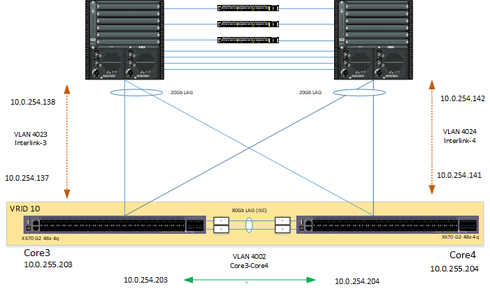
This is to be configured via static routing, due to problems in the legacy network enabling a common routing protocol. Below is an example of what the network interconnections will look like:
The two Extreme Switches are using MLAG, common VRRP between them for each of the VLANs with Fabric routing mode enabled, and OSPF also enable across the two.
So in the scenario I would like both cores to route all traffic to the first Cisco core, should that fail all traffic to be routed to the other core.
Have been looking at both these articles:
https://extremeportal.force.com/ExtrArticleDetail?an=000083175
https://extremeportal.force.com/ExtrArticleDetail?an=000083436
The new network is all on 10.x.x.x/8, everything else is to go to the legacy network.
Was exploring implementing something like the following:
create flow-redirect core3-redirect
configure flow-redirect core3-redirect add nexthop 10.0.254.204 priority 100
configure flow-redirect core3-redirect add nexthop 10.0.254.138 priority 200
edit policy ACL_redirect
Entry redirect {
If match all {
source-address 10.0.0.0/8;
} then {
permit;
redirect-name core3-redirect;
}
}
configure access-list ACL_redirect ports x ingress
---------------
create flow-redirect core4-redirect
configure flow-redirect core4-redirect add nexthop 10.0.254.142 priority 100
configure flow-redirect core4-redirect add nexthop 10.0.254.203 priority 200
edit policy ACL_redirect
Entry redirect {
If match all {
source-address 10.0.0.0/8;
} then {
permit;
redirect-name core4-redirect;
}
}
configure access-list ACL_redirect ports x ingress
--------------
Not sure if this is the best way to do it, perhaps using the following instead?:
configure iproute priority static [11-65534]
Also, should I use flow-redirect I would probably have to apply the ACL to all ports bar the ISC link and interlinks to legacy network?
Will have to give the same consideration on the legacy side to stop any asymmetric routing, so if you also have any ideas around that?
Many thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-23-2017 09:55 AM
Hi,
Sure, and I know what your saying and makes perfect sense. Unfortunately I'm in the situation where I need to minimalise what I do on the Cisco's as much as possible - using OSPF is how I would typically do it.
To handle the routes I was wondering if I could use it on conjunction with the following to manage the route:
https://extremeportal.force.com/ExtrArticleDetail?an=000091306
configure iproute add 10.1.1.0/24 10.2.1.1 protection ping
Not sure if it would work with a default route?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-23-2017 09:55 AM
Again how does "software redundancy will take care of activating or re-activating the redundant links" ?
Only when the port is disable or when 1 of cisco switches is down. But when that happens, your default route will still be in the routing table. You have no floating static default .route.
You can run all under OSPF with Cisco. All Layer 3. But again, that is what you want to avoid in the first place because of "legacy" cisco.
I can assure you, legacy Cisco is also a reputable product. You can accommodate mHSRP for sure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-23-2017 09:55 AM
So had another idea (to try and keep it simple), but not sure if anyone can collaborate it - but basically to use software port redundancy instead:
https://extremeportal.force.com/ExtrArticleDetail?an=000081265
Take the following:
So here I have removed the LAG / Port-Channels between the Extreme and Cisco's. Each Extreme core has a default route configured to their respective Cisco core, and the software redundancy will take care of activating or re-activating the redundant links. Routes shared via OSPF between the Extreme cores would then handle where to direct traffic dependant on whether to links to legacy core 1 or legacy core 2 go down?
What do you think?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-23-2017 09:00 AM
configure flow-redirect flow_redirect_name health-check [ping | arp | neighbordiscovery]
If any of the legacy Cisco switch goes down, your static route will always be in the routing table. So you have a black-hole route.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-23-2017 09:00 AM
Thanks for comment. I'll take a look at that section and post back if I work it out. Re the other comment about the health check, this link states the following:
https://extremeportal.force.com/ExtrArticleDetail?an=000083175
"If more than one next hope address is used, EXOS will automatically send ping health-checks to make sure the next hop is available. If the connectivity is loss then it will refer to the next highest priority next hop in the configuration."
So I'm assuming in my example with two next hope addresses it is doing this automatically?
Thanks.