This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- ISLs in 2-tier MLAG setup with RSTP goto LISTENING
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISLs in 2-tier MLAG setup with RSTP goto LISTENING
ISLs in 2-tier MLAG setup with RSTP goto LISTENING
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-24-2018 09:05 PM
Hey,
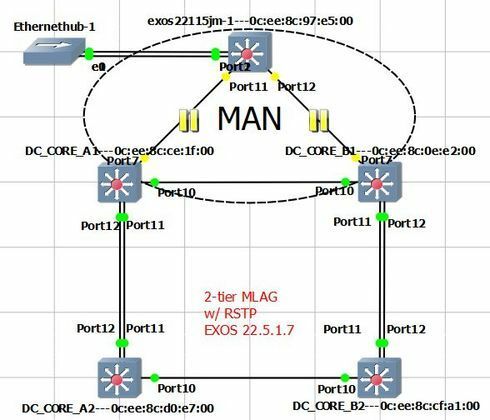
Let's look at the following topology.
In order to accomodate a MAN loop I thought I'd set up a simulation using EXOS 22.5 featuring RSTP support in MLAG scenarios.
What is not clear is how to configure RSTP exactly, thus I have configured it very simply like this:
* DC_CORE_A1.60 # show conf stp
#
# Module stp configuration.
#
configure stpd s0 mode dot1w
configure stpd s0 priority 4096
enable stpd s0 auto-bind vlan vl-NetMgmt
Not even considering the MAN loop (links are disabled), the links between tiers A1-B1 and A2-B2 on A1 and A2 are no longer forwarding.
* DC_CORE_A1.60 # sh s0 port
Port Mode State Cost Flags Priority Port ID Designated Bridge
7 802.1D FORWARDING 200000 eDappw---- 128 8007 10:00:0c??8c:ce:1f:00
10 802.1D LISTENING 200000 eDappw---- 128 800a 10:00:0c??8c:ce:1f:00
11* 802.1D FORWARDING 180000 eDap-w---- 128 800b 10:00:0c??8c:ce:1f:00
* DC_CORE_A2.7 # sh s0 port
Port Mode State Cost Flags Priority Port ID Designated Bridge
10 802.1D LISTENING 200000 eDappw---- 128 800a 80:00:0c??8c:d0:e7:00
11* 802.1D FORWARDING 180000 eRapaw---- 128 800b 10:00:0c??8c:ce:1f:00
MLAG is set up correctly.
Disabling STP on either A1 or B1 solves the issue. But we will need STP to protect from the loop.
Would anyone have an idea what the problem is?
Thx
Bonus question: Why does it show "LISTENING" anyway? cause that's not a 802.1w state (DISCARDING/LEARNING/FORWARDING)
Let's look at the following topology.
In order to accomodate a MAN loop I thought I'd set up a simulation using EXOS 22.5 featuring RSTP support in MLAG scenarios.
What is not clear is how to configure RSTP exactly, thus I have configured it very simply like this:
* DC_CORE_A1.60 # show conf stp
#
# Module stp configuration.
#
configure stpd s0 mode dot1w
configure stpd s0 priority 4096
enable stpd s0 auto-bind vlan vl-NetMgmt
Not even considering the MAN loop (links are disabled), the links between tiers A1-B1 and A2-B2 on A1 and A2 are no longer forwarding.
* DC_CORE_A1.60 # sh s0 port
Port Mode State Cost Flags Priority Port ID Designated Bridge
7 802.1D FORWARDING 200000 eDappw---- 128 8007 10:00:0c??8c:ce:1f:00
10 802.1D LISTENING 200000 eDappw---- 128 800a 10:00:0c??8c:ce:1f:00
11* 802.1D FORWARDING 180000 eDap-w---- 128 800b 10:00:0c??8c:ce:1f:00
* DC_CORE_A2.7 # sh s0 port
Port Mode State Cost Flags Priority Port ID Designated Bridge
10 802.1D LISTENING 200000 eDappw---- 128 800a 80:00:0c??8c:d0:e7:00
11* 802.1D FORWARDING 180000 eRapaw---- 128 800b 10:00:0c??8c:ce:1f:00
MLAG is set up correctly.
Disabling STP on either A1 or B1 solves the issue. But we will need STP to protect from the loop.
Would anyone have an idea what the problem is?
Thx
Bonus question: Why does it show "LISTENING" anyway? cause that's not a 802.1w state (DISCARDING/LEARNING/FORWARDING)
9 REPLIES 9
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-07-2018 10:28 PM
The topology got lost 😞 I'm attaching it again.
Two things:
1) I believe the problem was due to intricacies with GNS3. When you disable the port on one switch (here B2 at the bottom right), unlike in the real world, the port on the other side of the link (A2) does not go down. So in this case the other side was still physically up but not receiving any BPDUs. Since ports 10 on A1,A2 and B1,B2 respectively form an MLAG, it somehow makes sense that both ports 10 on A1 and A2 went to LISTENING.
To simulate a physical link down you have to manually disable the ports on both ends of the link, in this case B2 and A2. In that case everything continues to work.
2) Concerning Erik's statement: "STP over MLAG ports is required to e.g. detect loops between two access switches"
Wouldn't it be enough to run STP locally on each of the concerned switches and put all ports (except uplinks) into edge-safeguard mode with bpdu-protection. In case of loops (no matter if local to the switch or from another access switch) they would be disabled. You would not actually need STP to traverse the MLAGs.
Two things:
1) I believe the problem was due to intricacies with GNS3. When you disable the port on one switch (here B2 at the bottom right), unlike in the real world, the port on the other side of the link (A2) does not go down. So in this case the other side was still physically up but not receiving any BPDUs. Since ports 10 on A1,A2 and B1,B2 respectively form an MLAG, it somehow makes sense that both ports 10 on A1 and A2 went to LISTENING.
To simulate a physical link down you have to manually disable the ports on both ends of the link, in this case B2 and A2. In that case everything continues to work.
2) Concerning Erik's statement: "STP over MLAG ports is required to e.g. detect loops between two access switches"
Wouldn't it be enough to run STP locally on each of the concerned switches and put all ports (except uplinks) into edge-safeguard mode with bpdu-protection. In case of loops (no matter if local to the switch or from another access switch) they would be disabled. You would not actually need STP to traverse the MLAGs.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-26-2018 11:58 AM
In general, STP over MLAG ports is required to e.g. detect loops between two access switches that are connected to the distribution (or core) via MLAG. That is, the loop is from one access port of one switch to another access port of the other switch (similar use case as for ELRP disabling the egress port).
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-25-2018 09:34 AM
Just like Zdenek, I don't see the need to run STP above MLAG. STP should only be used to avoid loops at the access (or ELRP instead of STP).
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-25-2018 08:39 AM
What is the newly introduced RSTP and MSTP support concerning MLAG in 22.5 and 22.6 good for?