This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- RE: ISLs in 2-tier MLAG setup with RSTP goto LISTE...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISLs in 2-tier MLAG setup with RSTP goto LISTENING
ISLs in 2-tier MLAG setup with RSTP goto LISTENING
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-24-2018 09:05 PM
Hey,
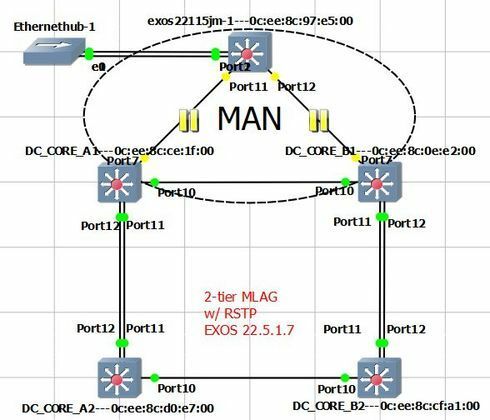
Let's look at the following topology.
In order to accomodate a MAN loop I thought I'd set up a simulation using EXOS 22.5 featuring RSTP support in MLAG scenarios.
What is not clear is how to configure RSTP exactly, thus I have configured it very simply like this:
* DC_CORE_A1.60 # show conf stp
#
# Module stp configuration.
#
configure stpd s0 mode dot1w
configure stpd s0 priority 4096
enable stpd s0 auto-bind vlan vl-NetMgmt
Not even considering the MAN loop (links are disabled), the links between tiers A1-B1 and A2-B2 on A1 and A2 are no longer forwarding.
* DC_CORE_A1.60 # sh s0 port
Port Mode State Cost Flags Priority Port ID Designated Bridge
7 802.1D FORWARDING 200000 eDappw---- 128 8007 10:00:0c??8c:ce:1f:00
10 802.1D LISTENING 200000 eDappw---- 128 800a 10:00:0c??8c:ce:1f:00
11* 802.1D FORWARDING 180000 eDap-w---- 128 800b 10:00:0c??8c:ce:1f:00
* DC_CORE_A2.7 # sh s0 port
Port Mode State Cost Flags Priority Port ID Designated Bridge
10 802.1D LISTENING 200000 eDappw---- 128 800a 80:00:0c??8c:d0:e7:00
11* 802.1D FORWARDING 180000 eRapaw---- 128 800b 10:00:0c??8c:ce:1f:00
MLAG is set up correctly.
Disabling STP on either A1 or B1 solves the issue. But we will need STP to protect from the loop.
Would anyone have an idea what the problem is?
Thx
Bonus question: Why does it show "LISTENING" anyway? cause that's not a 802.1w state (DISCARDING/LEARNING/FORWARDING)
Let's look at the following topology.
In order to accomodate a MAN loop I thought I'd set up a simulation using EXOS 22.5 featuring RSTP support in MLAG scenarios.
What is not clear is how to configure RSTP exactly, thus I have configured it very simply like this:
* DC_CORE_A1.60 # show conf stp
#
# Module stp configuration.
#
configure stpd s0 mode dot1w
configure stpd s0 priority 4096
enable stpd s0 auto-bind vlan vl-NetMgmt
Not even considering the MAN loop (links are disabled), the links between tiers A1-B1 and A2-B2 on A1 and A2 are no longer forwarding.
* DC_CORE_A1.60 # sh s0 port
Port Mode State Cost Flags Priority Port ID Designated Bridge
7 802.1D FORWARDING 200000 eDappw---- 128 8007 10:00:0c??8c:ce:1f:00
10 802.1D LISTENING 200000 eDappw---- 128 800a 10:00:0c??8c:ce:1f:00
11* 802.1D FORWARDING 180000 eDap-w---- 128 800b 10:00:0c??8c:ce:1f:00
* DC_CORE_A2.7 # sh s0 port
Port Mode State Cost Flags Priority Port ID Designated Bridge
10 802.1D LISTENING 200000 eDappw---- 128 800a 80:00:0c??8c:d0:e7:00
11* 802.1D FORWARDING 180000 eRapaw---- 128 800b 10:00:0c??8c:ce:1f:00
MLAG is set up correctly.
Disabling STP on either A1 or B1 solves the issue. But we will need STP to protect from the loop.
Would anyone have an idea what the problem is?
Thx
Bonus question: Why does it show "LISTENING" anyway? cause that's not a 802.1w state (DISCARDING/LEARNING/FORWARDING)
9 REPLIES 9
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-25-2018 07:49 AM
With MLAG you do not need Loop protection between access and the core...
Regards
Zdeněk Pala
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-25-2018 07:47 AM
Well, the actual topology is more like the following and the switches forming the MAN loop are indeed 3rd party.
BTW the remark about EXOS RSTP carrier VLAN is another interesting and unanswered question. Lots of mysteries here 🙂
BTW the remark about EXOS RSTP carrier VLAN is another interesting and unanswered question. Lots of mysteries here 🙂
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-25-2018 07:47 AM
STP supports any topology. 😉
If a provider MAN ring is used it may not be possible to use EAPS over it. EAPS over third party switches has its own problems, including by default not opening the ring port after detecting a failure. CFM might help as well.
Anyway, the above scenario does not seem to require anything but MLAG with LACP.
But EXOS should understand that the MLAG-ISL is not part of the STP topology in an MLAG setup, and provide useful show output to help in verification and troubleshooting in addition to correct operation (the show output does not look as if the feature is working as it should, and I have not tested STP over MLAG ports with EXOS yet, so I do not know if it works or not).
A possible problem in the scenario above might be the EXOS RSTP requirement of an untagged VLAN on an RSTP enable port, but the ISL is supposed to have tagged VLANs only. (I do not use RSTP on EXOS, but only MSTP, because of this limitation.)
Thanks,
Erik
If a provider MAN ring is used it may not be possible to use EAPS over it. EAPS over third party switches has its own problems, including by default not opening the ring port after detecting a failure. CFM might help as well.
Anyway, the above scenario does not seem to require anything but MLAG with LACP.
But EXOS should understand that the MLAG-ISL is not part of the STP topology in an MLAG setup, and provide useful show output to help in verification and troubleshooting in addition to correct operation (the show output does not look as if the feature is working as it should, and I have not tested STP over MLAG ports with EXOS yet, so I do not know if it works or not).
A possible problem in the scenario above might be the EXOS RSTP requirement of an untagged VLAN on an RSTP enable port, but the ISL is supposed to have tagged VLANs only. (I do not use RSTP on EXOS, but only MSTP, because of this limitation.)
Thanks,
Erik
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-25-2018 07:47 AM
I would go with EAPS to handle ring topology at the MAN and I would utilize ELRP to detect loop at the access. Any kind of STP based protocol is wrong at the ring topologies.
Regards
Zdeněk Pala
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-25-2018 07:47 AM
Update: Port 10 on B2 was disabled. This put ports 10 on both A1 and A2 to listening. That somewhat defies the active-active nature of MLAG.
If I disable any other port 10 on A1,A2 or B1 nothing similar happens.
When the problem appears, port 10 on A2 is flapping between LEARNING and LISTENING and the log repeately says " Fail to flush vlan inst 000f424a Switch port 10 error 1"
(Ports 7 on both devices toward the MAN loop are disabled. The picture doesn't show it but they are. For that matter, ignore the MAN loop.)
If I disable any other port 10 on A1,A2 or B1 nothing similar happens.
When the problem appears, port 10 on A2 is flapping between LEARNING and LISTENING and the log repeately says "
(Ports 7 on both devices toward the MAN loop are disabled. The picture doesn't show it but they are. For that matter, ignore the MAN loop.)