- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (VSP/Fabric Engine)
- Creative uses for the I-SID!
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Creative uses for the I-SID!
Creative uses for the I-SID!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-21-2020 10:20 AM
Hi,
The reason I am opening this thread on the topic is to help me break my traditional approach to networking and help me understand and develop ideas that creatively use the fabric.
I’m trying to grasp ideas of how I can use the function of the fabric to do things or solves problems that are currently not in my periphery.
As an example, on this post
Mig mentions how the use of Flex UNI was used to keep a phone on the same VLAN but provision it in a DMZ then back into the LAN by alternating the I-SID.
When reading the various manuals you observe from a high level things that are sometimes hard to put into a real world context, like being able to join different VLAN ID’s on a single I-SID, but what sort of problems would that solve?
I understand the hyper virtualisation aspect of the fabric, but what about pulling it together, using the i-SID as service and the addition of L3VSN’s. How complicated or practical or widespread would it be to use lots of IS-IS accept polices to allow access to services or is the use of a Firewall more prevalent for intra service communication or generally this is just for special cases?
Also not sure about the idea where Fabric is extensively being used for the VLAN /IP to follow the client anywhere in the network as the norm i.e. if you have a network with lots of edge cabinets through ExtremeControl I’ve kept say logical /24 subnets for Data, Voice etc contained to location - kept traditional best practices. If a client moves it simply gets a different IP in the new location based on the switch it connects too. I am seeing that the fabric is removing those boundaries but is that a good idea? I get it for specific cases but not adopted as the norm. What about prospect of VLAN loops with the VLAN potentially anywhere in the network?
Appreciate this is a very open ended topic, but even just a few ideas would really help me understand and hopefully develop my own ideas.
Many thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-22-2020 11:00 AM
Ah, that’s a shame, those attributes seemed like a revelation then. Fingers crossed they will come along soon!
In relation to how you have configured the locations I’ve done a similar thing but using VLAN islands instead. I don’t have access to a system at moment to post screenshots, but when I do I will post.
What the VLAN islands do in policy does pretty much the same thing but in a different way. In summary you can configure a VLAN island for say printers, and then program the VLAN / I-SID information for each switch. Then for the policy of ‘Printers’ you just select the VLAN island container for Printers and it will automatically associate the corresponding VLAN / I-SID for that switch. Basically all it does is use the VLAN island details as a database reference and then just writes the Printer policy to each switch with the corresponding VLAN / I-SID it correlates to.
Anyway, might be useful for someone to know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-21-2020 07:56 PM
Not yet as many attributes as for the BOSS:

It will maybe come in futur releases if we ask it enough
Mig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-21-2020 07:37 PM
Roger and Mig, this is really useful. Very much appreciate the detail and the time taken to answer the post.
Have a question about the RADIUS attributes. I had not realised you could enable some of those features and wondered how they got configured on the port when the VLAN was dynamically being assigned!
My question is, do you know if those same attributes work with EXOS? or what attributes are available in EXOS I could use. Guess I am most interested in the FA attribute options?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-21-2020 06:05 PM
Hi Martin,
Another use case of same VLAN/multiple i-sid I use is to standardize the vlan config on different remote sites at customer premises.
All the sites are using the same vlan ids while the i-sid are different on all sites. A I use this within different VRFs.
This is keeping the infrastructure understanding quite easy for the customer.
I manage this through aggregated rules in the NAC where the site is the discriminator for the i-sid.
See here some screenshots for the printers with MAC Auth but it applies to all VLANs and with 802.1X Auth:
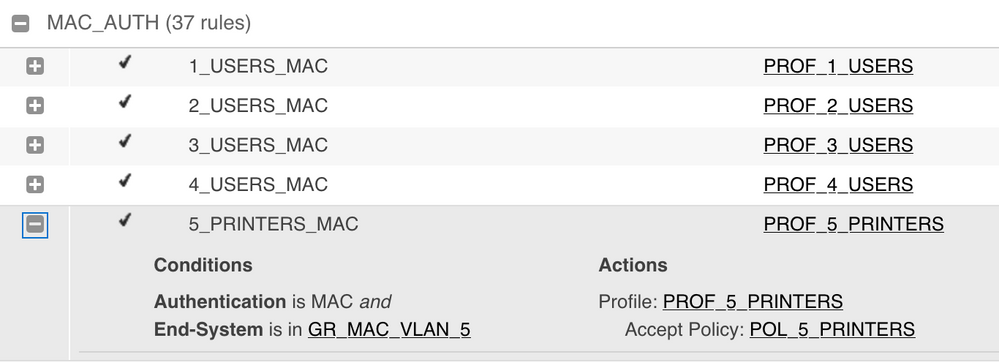
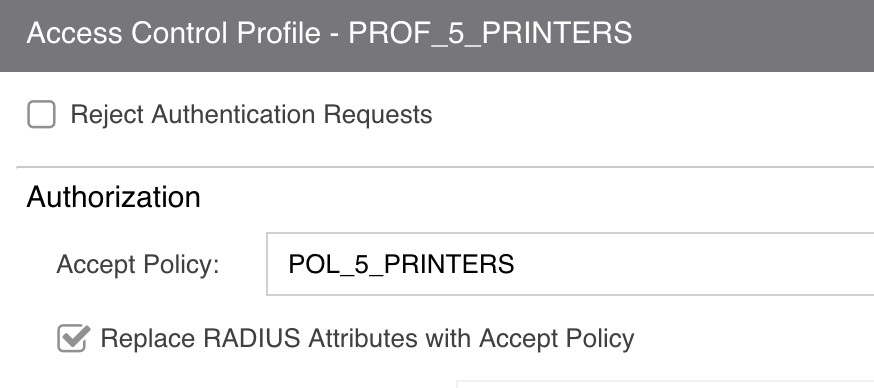
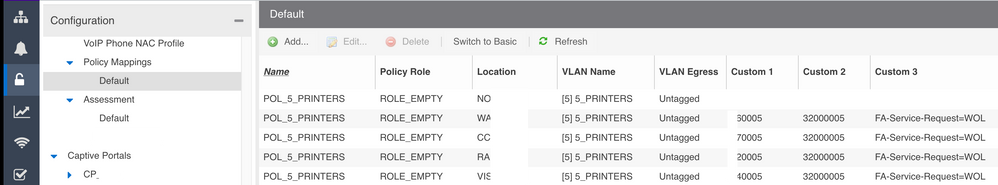
As you see, one rule fits all the sites (30+).
This is my radius attribute profile for BOSS switches:
FA-VLAN-Create=1
FA-VLAN-ISID=%VLAN_ID%:%CUSTOM1%
Egress-VLANID=0x%CUSTOM2%
FA-Service-Request=BPDU
FA-Service-Request=SLPPGUARD
FA-Service-Request=DHCPSNOOP:%VLAN_ID%
Service-Type=%MGMT_SERV_TYPE%
%CUSTOM3%
You can see that we are able to enable BPDU-Filtering, SLPP-Guard, DHCP-Snooping and WOL on a port where we provision a VLAN.
For what concerns inter VRF traffic, my golden rule is “a switch is not a firewall and a firewall is not a switch”. If you need ACL type of filtering, do that in a firewall and you will be happy.
Regards,
Mig

