- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (VSP/Fabric Engine)
- Same IP on each side of VOSS cluster for mirrored ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Same IP on each side of VOSS cluster for mirrored P2P's to Firewall
Same IP on each side of VOSS cluster for mirrored P2P's to Firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-04-2021 01:21 PM
Hi,
Currently trying to convert an EXOS configuration into VOSS with a topology I’m not sure how best to translate.
Here is a simple diagram of the topology. The two VOSS switches are a clustered pair.
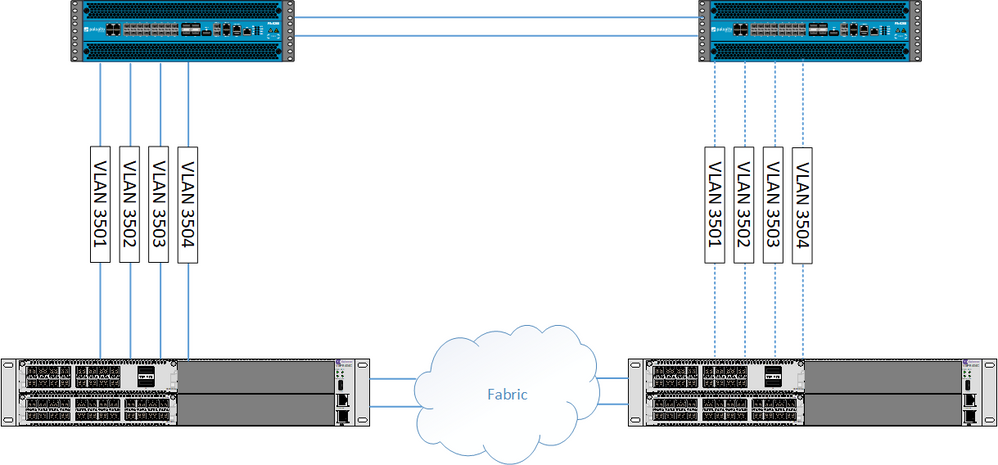
Here their are two firewalls configured as active / passive, the active is top left, passive top right.
The links actually criss-cross but for simplicity I’ve drawn them as above. In essence there are four VLAN’s 3501 to 3504 that are each P2P /30 subnets and are configured as OSPF / BFD link adjacencies.
On the active firewall the ports are all up and active, the passive firewall the ports are all down.
The way it works and the way its configured in EXOS is that the same VLAN’s and P2P IP’s are configured on both cores, but because the side of the right is down, the VLAN interfaces are down, and therefor there is no conflict in the fact the same IP configuration is configured on both sides.
Should the active firewall fail, then the same P2P interfaces come up on the other core / firewall and everything is learned through their instead. This is configured that way as the firewalls have identical configuration, so when flipping across the configuration is still the same, hence the link configuration needs to be the same.
Not sure how to mirror this in VOSS i.e. have the same IP both sides. This is required additionally if one VOSS core fails the other VOSS core needs to own the IP addresses, much like the EXOS config would have.
Maybe I can use RSMLT or DVR in this capacity to create a common IP between the clustered VOSS switches?
Maybe I could do something with Flex-UNI to put the same VLANs each side into different I-SID’s. That would essentially be the same VLAN ID on port, but each port will have a different I-SID, meaning I could possibly use the same IP (P2P Subnet)?
The only other option I can think of is having one side own two of the VLAN’s IP addresses (P2P Subnets), and have the other side own the other two. I could then just use the fabric to get each of the VLANs to the correct place. Issue with that is if one of the cores fail, I effectively only have two OSPF adjacencies instead of four?
Many thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-04-2021 07:03 PM
This makes sense now 🙂 There are multiple ways to do it. I actually prefer a L3 solution over an L2 solution where the FW bridges two VLANs.
Roger
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-04-2021 05:12 PM
Sorry guys, I should have added more detail to the query. My head is in the problem so I’ve made assumptions on the detail you needed to know about without realising it.
Hopefully this diagram will help better, it also shows what I meant by criss-crossing links that I wasn’t clear on.
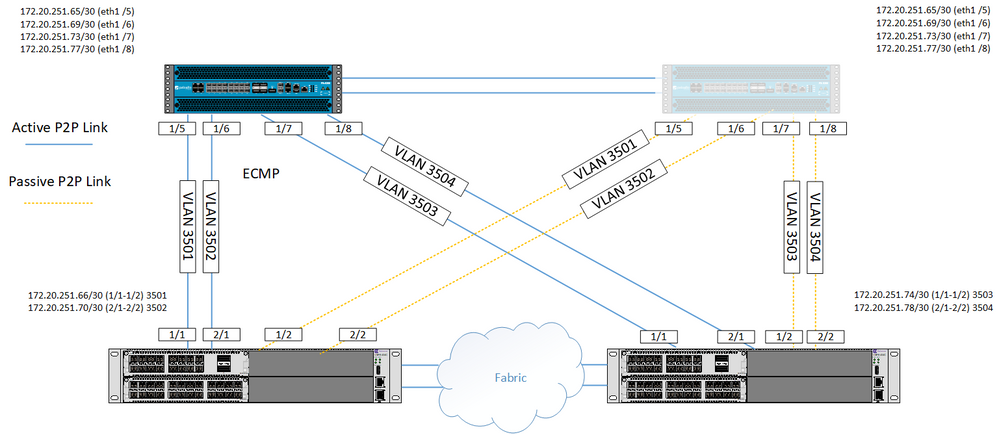
So each of the connections are L3 PTP connections, running OSPF and using ECMP.
Drawing it out like this actually makes it clearer to myself (and jogs my memory), in that the third option I gave would actually do the trick i.e. I don’t actually need to configured each of the 4 PTP IP addresses on both sides - its just how the config is written in EXOS but it doesn’t actually serve any advantage or used in that way (some old config was lingering around).
If the firewall to left goes down the second firewall goes active and all the links come up. That means each of the four PTP links come before but just pointing to the other firewall, but the bit to pay attention too is the fact the same VLAN ID’s are used on the same switches.
The reason for that is when I come across this issue:
Basically I originally had all the VLANs and IP addressing configured on each core (hence thinking I need to mirror it in VOSS) i.e. if you just focus on core 1 (bottom left), I had it configured for VLANs 3501 (Active), 3502 (Active), 3503 (Passive) an 3504 (Passive). When the firewall flipped it went 3501 (Passive), 3502 (Passive), 3503 (Active) and 3504 (Active).
This created an issue where the PTP links stopped working. This turned out to be that the firewall would see the same MAC address from the switch when the VLANs changed from 3501 & 3502 to 3503 & 3504. This caused an issue because when the firewall goes from passive to active it is expecting to see the same MAC coming from the same VLAN’s, but it didn’t and so stopped working.
The answer was to make sure the VLANs stayed the same on the cores when the firewalls flipped across from passive to active, and this was done by pluming it in as above.
The thread was really useful though as its presented answers to other scenario’s, maybe this isn’t the best way of doing it and a different way of doing it VOSS.
Hopefully the information will be helpful to someone else 🙂
Apologies for the confusing and miss-leading the conversation.
Thanks,
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-04-2021 02:27 PM
Could you complete the topology diagram with the missing links?
Are the 4 VLANs on 4 different ports?
Are the uplinks between VSPs in SMLT config?
Mig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-04-2021 01:53 PM
yes, but don’t forget he is talking about a single VLAN (actually 4 vlans) being on both vIST switches bridged by the cross-links from/to the FW, which he has not drawn.
Roger
