- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (VSP/Fabric Engine)
- Same IP on each side of VOSS cluster for mirrored ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Same IP on each side of VOSS cluster for mirrored P2P's to Firewall
Same IP on each side of VOSS cluster for mirrored P2P's to Firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-04-2021 01:21 PM
Hi,
Currently trying to convert an EXOS configuration into VOSS with a topology I’m not sure how best to translate.
Here is a simple diagram of the topology. The two VOSS switches are a clustered pair.
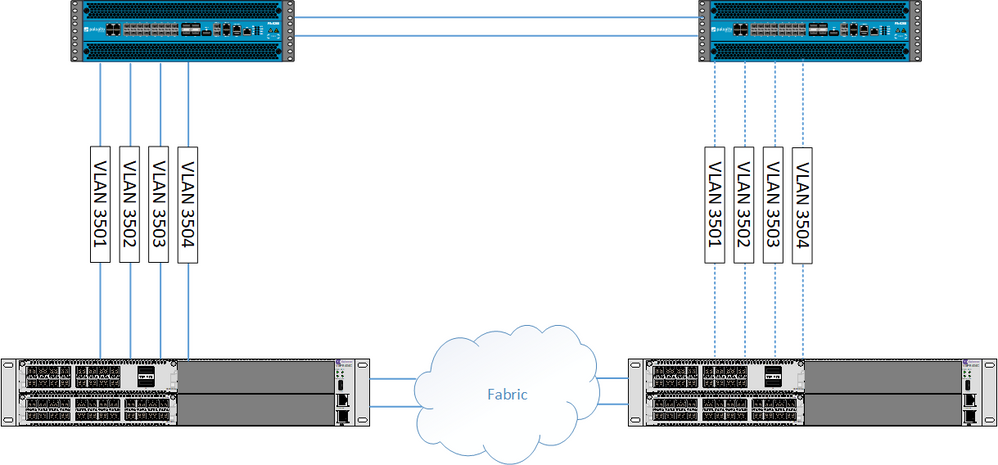
Here their are two firewalls configured as active / passive, the active is top left, passive top right.
The links actually criss-cross but for simplicity I’ve drawn them as above. In essence there are four VLAN’s 3501 to 3504 that are each P2P /30 subnets and are configured as OSPF / BFD link adjacencies.
On the active firewall the ports are all up and active, the passive firewall the ports are all down.
The way it works and the way its configured in EXOS is that the same VLAN’s and P2P IP’s are configured on both cores, but because the side of the right is down, the VLAN interfaces are down, and therefor there is no conflict in the fact the same IP configuration is configured on both sides.
Should the active firewall fail, then the same P2P interfaces come up on the other core / firewall and everything is learned through their instead. This is configured that way as the firewalls have identical configuration, so when flipping across the configuration is still the same, hence the link configuration needs to be the same.
Not sure how to mirror this in VOSS i.e. have the same IP both sides. This is required additionally if one VOSS core fails the other VOSS core needs to own the IP addresses, much like the EXOS config would have.
Maybe I can use RSMLT or DVR in this capacity to create a common IP between the clustered VOSS switches?
Maybe I could do something with Flex-UNI to put the same VLANs each side into different I-SID’s. That would essentially be the same VLAN ID on port, but each port will have a different I-SID, meaning I could possibly use the same IP (P2P Subnet)?
The only other option I can think of is having one side own two of the VLAN’s IP addresses (P2P Subnets), and have the other side own the other two. I could then just use the fabric to get each of the VLANs to the correct place. Issue with that is if one of the cores fail, I effectively only have two OSPF adjacencies instead of four?
Many thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-04-2021 01:51 PM
Hi Roger,
If I understand well the description, we have an active/passive firewall cluster.
I have seen such setup in production (checkpoint) and the passive member is not forwarding any client traffic to the VSP. The MAC entries on both VSP clusters are different on the uplink ports towards the firewall.
Martin is also mentioning OSPF between the firewalls and the VSP. In such case, a /30 subnet is not enough to activate RSMLT
Mig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-04-2021 01:39 PM
Believe me, if the traffic is bridged through the firewalls, then you will see a MAC complaint and VSP will move the peer MAC to the vIST if you don’t turn off the “sys control virtual-ist mac-move-protection”.
Roger
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-04-2021 01:37 PM
Hi Martin,
As it is a VOSS cluster, all VLANs have to be present on both VOSS switches ad have an i-sid.
You can perfectly mirror the vlan config on the ports and to ensure high-availability on the L3 side of the VOSS cluster you can use RSMLT (using 2 IP addresses) or VRRP (using 3 IP addresses). This will clean the “same IP issue”.
If the firewall is putting down the port, the fdb should be cleaned. I don’t see any MAC issue.
Mig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-04-2021 01:33 PM
Martin
what you need to know is that if you are running the VSPs in a vIST cluster, then the two switches exchange MAC addresses through the IST protocol (you need to configure a VLAN always on both sides incl. ISIDs). However what the switches in that case by default check for, is whether they learn the peer MAC through edge ports between the peer vIST switches, like in your setup as the firewalls are L2 only. In this case to avoid the peer MAC checking, you need to turn this feature off: “no sys control virtual-ist mac-move-protection”.
Now what I don’t understand is the following: You are talking about pt-t-pt links, but then you are talking about a cross-connection. In that case, you don’t have point-to-points anymore, but there are multiple ports that are used for the same VLAN - one to FW 1 and one to FW 2, correct? Are you saying the firewall takes care of taking the ports up/down and thus in an active setup, only one port is up for a given VLAN per switch?
Roger
