This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (General)
- Creation of a single SSID with ExtremeControl
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Creation of a single SSID with ExtremeControl
Creation of a single SSID with ExtremeControl
Anonymous
Not applicable
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-28-2018 10:41 AM
Hi,
I would like to create a single SSID for all my wireless requirements, and protect that with a pre-shared key so that other wireless users in the building can't, say, make use of the Guest internet.
At the moment I have the following SSIDs:
1) "Guest" - this is providing a captive portal via Extreme Control via MAC authentication
2) "Internal" - this is doing 802.1x authentication via Extreme Control
3) "MobileIron" - this is doing MAC authentication via Extreme Control
Any corporate device I think I can push the SSID and pre-shared key out via Windows policy. Guest and MobileIron users can simply enter the pre-shared key when they connect.
So handling this through Extreme Control I believe I can do, but not sure what to do about the authentication and redirection methods for combining the SSID's on the wireless controller.
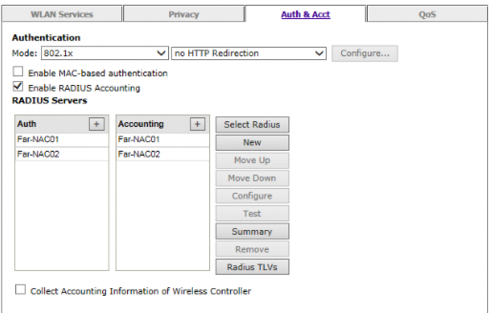
For example: Guest and MobileIron use MAC Auth and Internal uses 802.1x in the 'Auth & Act' section of the WLAN config, see image below first for internal 802.1x
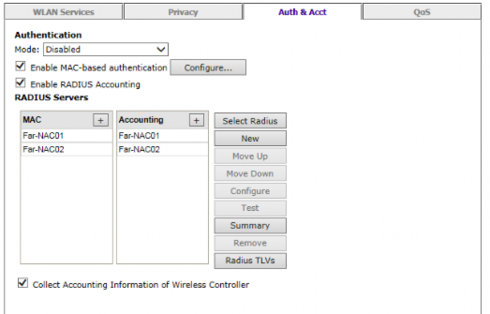
and the following for Guest and Mobileiron:
So is the answer that I simply create the a single SSID, set the mode to 802.1x but also tick the box for 'Enable MAC-Based authentication' - but I don't believe that's going to work for all situations?
Would web redirection at the controller still work for Guest users to Extreme Control captive portal - or does SSID always need to be separate?
The reason I want to combine Guest with a single SSID is that on the wired network if anyone connects to the network that fails authentication it is automatically dropped to the Guest network where they are redirected to a captive portal page and then only get internet access, and want to do the same for wireless as dynamically as it does for wired.
With wired I can set the authentication methods to first use 802.1x then MAC, but not sure I can do that same for wireless - which I think is the sum of the problem?
If you have any experience let me know, many thanks in advance.
I would like to create a single SSID for all my wireless requirements, and protect that with a pre-shared key so that other wireless users in the building can't, say, make use of the Guest internet.
At the moment I have the following SSIDs:
1) "Guest" - this is providing a captive portal via Extreme Control via MAC authentication
2) "Internal" - this is doing 802.1x authentication via Extreme Control
3) "MobileIron" - this is doing MAC authentication via Extreme Control
Any corporate device I think I can push the SSID and pre-shared key out via Windows policy. Guest and MobileIron users can simply enter the pre-shared key when they connect.
So handling this through Extreme Control I believe I can do, but not sure what to do about the authentication and redirection methods for combining the SSID's on the wireless controller.
For example: Guest and MobileIron use MAC Auth and Internal uses 802.1x in the 'Auth & Act' section of the WLAN config, see image below first for internal 802.1x
and the following for Guest and Mobileiron:
So is the answer that I simply create the a single SSID, set the mode to 802.1x but also tick the box for 'Enable MAC-Based authentication' - but I don't believe that's going to work for all situations?
Would web redirection at the controller still work for Guest users to Extreme Control captive portal - or does SSID always need to be separate?
The reason I want to combine Guest with a single SSID is that on the wired network if anyone connects to the network that fails authentication it is automatically dropped to the Guest network where they are redirected to a captive portal page and then only get internet access, and want to do the same for wireless as dynamically as it does for wired.
With wired I can set the authentication methods to first use 802.1x then MAC, but not sure I can do that same for wireless - which I think is the sum of the problem?
If you have any experience let me know, many thanks in advance.
9 REPLIES 9
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-04-2018 12:42 AM
Hey Martin,
The problem that we see is as soon as you enable 802.1x on the SSID when they attempt to associate to the SSID mobile devices will prompt the user for username/password rather then pushing them straight to the captive portal. I always recommend a separate SSID for 802.1x just to improve user experience if captive portal is going to be used.
Thanks
-Ryan
The problem that we see is as soon as you enable 802.1x on the SSID when they attempt to associate to the SSID mobile devices will prompt the user for username/password rather then pushing them straight to the captive portal. I always recommend a separate SSID for 802.1x just to improve user experience if captive portal is going to be used.
Thanks
-Ryan
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-19-2019 05:42 PM
What do you do to prevent devices in an End-System Group from joining guest and jumping directly to their spot in the NAC policy? My concern is a corporate device is connected to the guest wireless and now traffic is not encrypted and the device now has access to more network resources than intended on guest wifi. Can you have two policies in the NAC. One for enterprise (WPA/MAC Auth and 802.1x Auth) and one for Guest? Or am I missing something all together?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-19-2019 07:37 PM
Martin,
depending on on how you set this h, you can create rules to deny access if those devices connect on the guest SSID. Also you can set to deny devices that are in AD to connect to the guest ssid.
depending on on how you set this h, you can create rules to deny access if those devices connect on the guest SSID. Also you can set to deny devices that are in AD to connect to the guest ssid.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-19-2019 07:38 PM
Can you give me more details? I can't find where the NAC knows what SSID they connected from.