This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (General)
- Radius logs show success but controller shows erro...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Radius logs show success but controller shows error
Radius logs show success but controller shows error
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-21-2016 12:31 PM
We just installed two new C5210 controllers for a client. They also currently have two C4110-1 controllers in production. One of the new controllers that was installed is not authenticating via Radius with a Windows 2012 NPS server. The logs on the NPS server show a successfull authentication, however the wireless controller shows an error. When I test the radius server from the WLAN auth section I receive the following error: RADIUS_SHAREDSECRETKEY_DECODE_FAILED
The authentication request does show in the NPS logs with an incorrect user account/password error. So the controller is sending radius requests to the server successfully. If I test the radius server from the Login Maintenance screen using authorized credentials the test returns a "System error" message, while the NPS server shows an authentication success message.
I have removed the WLAN controller as a radius client and then added it back. I have also deleted the radius server from the controller and added it back. The shared secret is entered correctly and it is sending the authentication requests to the radius server correctly, it just doesn't seem that it is receiving a proper response back.
The other new controller is authentication properly as well as the two existing controllers. It is only one controller that is experiencing this issue.
Thank You.
The authentication request does show in the NPS logs with an incorrect user account/password error. So the controller is sending radius requests to the server successfully. If I test the radius server from the Login Maintenance screen using authorized credentials the test returns a "System error" message, while the NPS server shows an authentication success message.
I have removed the WLAN controller as a radius client and then added it back. I have also deleted the radius server from the controller and added it back. The shared secret is entered correctly and it is sending the authentication requests to the radius server correctly, it just doesn't seem that it is receiving a proper response back.
The other new controller is authentication properly as well as the two existing controllers. It is only one controller that is experiencing this issue.
Thank You.
10 REPLIES 10
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-21-2016 02:27 PM
You've wrote...
"The logs on the NPS server show a successfull authentication"
"The authentication request does show in the NPS logs with an incorrect user account/password error. "
So it's not an success - right.
I'd check whether the request hits the right connection request / network policy.
Look in the event log and compare the request from the good v10 controller with the bad one.
"The logs on the NPS server show a successfull authentication"
"The authentication request does show in the NPS logs with an incorrect user account/password error. "
So it's not an success - right.
I'd check whether the request hits the right connection request / network policy.
Look in the event log and compare the request from the good v10 controller with the bad one.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-21-2016 02:18 PM
NAC is not involved in this. This is directly between the wireless controller and Windows NPS server.
Both new controllers are running 10.01.05.0008. They are in an availability pair. The primary controller fails radius authentication, while the backup controller is successful with radiusu authentication. Both have identical configurations for the radius server and are all using the same shared key.
I do have an open GTAC case, but haven't heard anything back yet. I just thought I would throw it out on the hub to see if anyone else has encountered a similar issue.
Both new controllers are running 10.01.05.0008. They are in an availability pair. The primary controller fails radius authentication, while the backup controller is successful with radiusu authentication. Both have identical configurations for the radius server and are all using the same shared key.
I do have an open GTAC case, but haven't heard anything back yet. I just thought I would throw it out on the hub to see if anyone else has encountered a similar issue.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-21-2016 02:18 PM
Thanks Ty. We'll have someone in contact with you soon.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-21-2016 02:09 PM
Hello Ty,
That is odd.
The only time I've seen that error message is if there is a discrepancy in the shared secret configured on either side, unless we have had a bug.
What version are you running? There was a bug that we fixed in 9.21.02 and later that involved a re-configured the shared secret. (in that case, a radius server configured from scratch was fine)
Is NAC involved at all?
There are a few knowledge articles that match, but any issues seen are fixed in current firmware.
https://gtacknowledge.extremenetworks.com/articles/Solution/Changing-the-radius-shared-secret-on-the...
https://gtacknowledge.extremenetworks.com/articles/Solution/RADIUS-SHAREDSECRETKEY-DECODE-FAILED-err...
https://gtacknowledge.extremenetworks.com/articles/Solution/Dynamic-Reauth-is-failing-with-a-shared-...
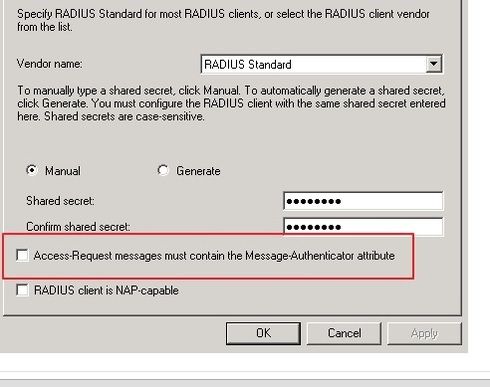
I would also double check that this Access-Request message box is not checked:
If nothing above helps and it's still not working, I would suggest opening a case with GTAC and we can investigate further.
Thanks,
Jason
That is odd.
The only time I've seen that error message is if there is a discrepancy in the shared secret configured on either side, unless we have had a bug.
What version are you running? There was a bug that we fixed in 9.21.02 and later that involved a re-configured the shared secret. (in that case, a radius server configured from scratch was fine)
Is NAC involved at all?
There are a few knowledge articles that match, but any issues seen are fixed in current firmware.
https://gtacknowledge.extremenetworks.com/articles/Solution/Changing-the-radius-shared-secret-on-the...
https://gtacknowledge.extremenetworks.com/articles/Solution/RADIUS-SHAREDSECRETKEY-DECODE-FAILED-err...
https://gtacknowledge.extremenetworks.com/articles/Solution/Dynamic-Reauth-is-failing-with-a-shared-...
I would also double check that this Access-Request message box is not checked:
If nothing above helps and it's still not working, I would suggest opening a case with GTAC and we can investigate further.
Thanks,
Jason
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-21-2016 02:01 PM
I did review that article already. There is a NAC server in this environment, however the radius authentication in this situation is between the controller and a Windows Server 2012 NPS server.
I did confirm that there is not a radius override enabled in the NAC appliance.
I did confirm that there is not a radius override enabled in the NAC appliance.