This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (Identifi)
- RE: Extreme Wireless Controller Redirect to Extern...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Extreme Wireless Controller Redirect to External Captive Portal
Extreme Wireless Controller Redirect to External Captive Portal
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-08-2015 03:21 PM
Hi Extreme experts,
I have a question regarding (Firewall friendly) External Captive Portal Redirection.
First my goal:
I need to integrate the Extreme Wireless Controller into an external Captive Portal System.
- The Portal System first needs a MAC Authentication Request via RADIUS (like Extreme NAC) - which is accepted.
- The Portal expects a URL-Request: "https://:8443/ahsfasdzfgfaszdfd&mac=00-11-22-33-44-55" where 00-11-22-33-44-55 is the MAC of the Client.
The Extreme Wireless Controller should do the following:
1) Send MAC Authentication Request to Portal-System
2) Redirect any HTTP/HTTPS request to "https://:8443/ahsfasdzfgfaszdfd&mac=00-11-22-33-44-55"
3) After successfull authentication the Role of the client should be changed via RADIUS-CoA.
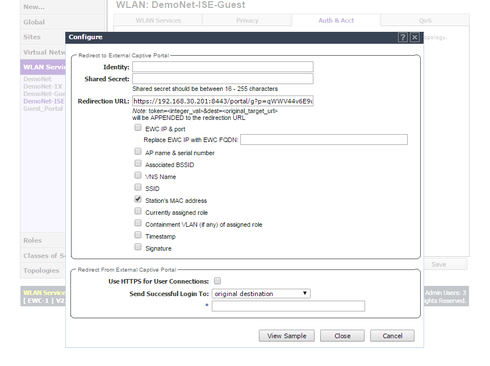
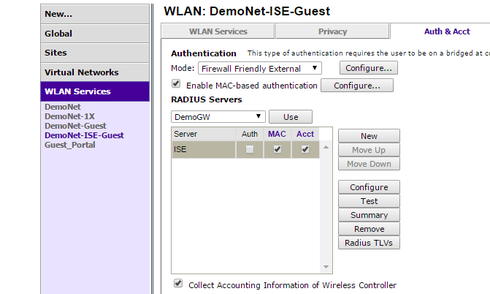
What I tried is the Firewall Friendly External Captive Portal with the following settings:
But unfortunately that configuration does not work.
1) If MAC Authentication is enabled no redirection is performed (The return Policy role is identical to the Unauthenticated Role in VNS settings). If I disable the MAC Authentication on the WLAN Service URL-Redirection is performed but with unexpected attributes:
Is there any way to disable the unwanted attributes dst, token and wlan?
How can I perform MAC Authentication and Redirection?
Any ideas?
Best Regards
Michael
I have a question regarding (Firewall friendly) External Captive Portal Redirection.
First my goal:
I need to integrate the Extreme Wireless Controller into an external Captive Portal System.
- The Portal System first needs a MAC Authentication Request via RADIUS (like Extreme NAC) - which is accepted.
- The Portal expects a URL-Request: "https://:8443/ahsfasdzfgfaszdfd&mac=00-11-22-33-44-55" where 00-11-22-33-44-55 is the MAC of the Client.
The Extreme Wireless Controller should do the following:
1) Send MAC Authentication Request to Portal-System
2) Redirect any HTTP/HTTPS request to "https://:8443/ahsfasdzfgfaszdfd&mac=00-11-22-33-44-55"
3) After successfull authentication the Role of the client should be changed via RADIUS-CoA.
What I tried is the Firewall Friendly External Captive Portal with the following settings:
But unfortunately that configuration does not work.
1) If MAC Authentication is enabled no redirection is performed (The return Policy role is identical to the Unauthenticated Role in VNS settings). If I disable the MAC Authentication on the WLAN Service URL-Redirection is performed but with unexpected attributes:
Is there any way to disable the unwanted attributes dst, token and wlan?
How can I perform MAC Authentication and Redirection?
Any ideas?
Best Regards
Michael
9 REPLIES 9
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-09-2015 04:05 PM
Hi Michael
To strip these values would require you to submit a feature request.
In your URL, what does the string ahsfasdzfgfaszdfd actually refer to?
-Gareth
To strip these values would require you to submit a feature request.
In your URL, what does the string ahsfasdzfgfaszdfd actually refer to?
-Gareth
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-09-2015 04:05 PM
Hi Gareth,
thanks a lot for your provided information. I checked the document and see that the unanwanted attributes are mandatory.
Do you see any chance to realize the requirement of the portal system?
Requirement is to redirect to a url like: https://%3cip/DNS%3E:8443/ahsfasdzfgfaszdfd&mac=001122334455
? -> Without token, ect.
Or would that be a feature request?
With best Regards
Michael
thanks a lot for your provided information. I checked the document and see that the unanwanted attributes are mandatory.
Do you see any chance to realize the requirement of the portal system?
Requirement is to redirect to a url like: https://%3cip/DNS%3E:8443/ahsfasdzfgfaszdfd&mac=001122334455
? -> Without token, ect.
Or would that be a feature request?
With best Regards
Michael
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-09-2015 03:19 PM
How to you have your policies setup roles? You have to makes sure that this information is allowed based on your policy.
If you go to VNS > Roles >
Verify that the services that you need to pass are allowed. Also please do not forget that the rules are run from top to bottom, so placement of your allows and denies are key
Please let me know if this does or does not work so I can assist further 🙂
If you go to VNS > Roles >
Verify that the services that you need to pass are allowed. Also please do not forget that the rules are run from top to bottom, so placement of your allows and denies are key
Please let me know if this does or does not work so I can assist further 🙂
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-09-2015 03:19 PM
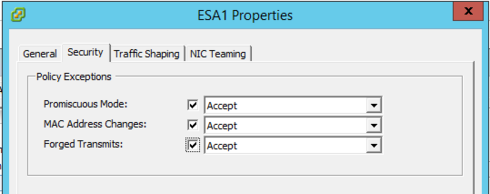
You are very welcome. I just had a thought. Is this a virtual controller or a physical controller?
The reason I ask is, now that I am thinking about it I had a similar issue with guest in the past. it ended up being the port group security on the VSwitch in VMWare. If it is indeed a virtual controller and in VMWare, can you verify that the security settings look like this for that particular port group?
Otherwise, VMWare won't let the MAC through
The reason I ask is, now that I am thinking about it I had a similar issue with guest in the past. it ended up being the port group security on the VSwitch in VMWare. If it is indeed a virtual controller and in VMWare, can you verify that the security settings look like this for that particular port group?
Otherwise, VMWare won't let the MAC through
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-09-2015 03:19 PM
Hi Joseph,
first - thanks for your advice. I double checked bute unfortunately all necessary traffic is allowed.
In fact
I allow ARP, BootP, DNS, IP to WLC, IP to Portal and deny the rest
Should be enough and the Role works if I do no MACAuth.
Thanks
Michael
first - thanks for your advice. I double checked bute unfortunately all necessary traffic is allowed.
In fact
I allow ARP, BootP, DNS, IP to WLC, IP to Portal and deny the rest
Should be enough and the Role works if I do no MACAuth.
Thanks
Michael