This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (Identifi)
- Lacking WLAN Features (Private PSKs, Per Client Qu...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Lacking WLAN Features (Private PSKs, Per Client Queueing)
Lacking WLAN Features (Private PSKs, Per Client Queueing)
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-17-2016 01:45 PM
While trying to replace existing wireless infrastructure systems from other vendors, we get confronted with several particular features which not seem to exist in Extreme WiFi.
1. Private PSKs, local and with RADIUS backend.
Some vendors support individual WPA2 PSKs for each connecting MAC Address.
The wireless system has a list of allowed mac addresses together with a unique PSK for each address.
This way every client can have its own WPA PSK, i.e. when you want to lock out one specific client from your wireless system, you do not have to change the WPA PSK on all devices.
It also prevents users from connecting other end devices to the wireless network as every PSK is bound to a specific MAC.
This is very handy to improve management and security in wireless network with clients which do not support WPA enterprise. And it minimizes the administrative overhead for 802.1x in smaller environments.
Other vendors support private PSKs also with RADIUS backends for centralized management.
We often have Extreme WiFi together with NAC, so this would be a perfect combination.
In NAC one would have to maintain PSKs for end systems and WiFi AP must be able to derive actual PSK from RADIUS response.
Source: Workshop Slides from other vendor, cf. page 78.
Are there any ideas or plans how this could be implemented with Extreme WiFi?
For me the only way right now seems to establish WPA enterprise which is more complicated for system administrators.
2. Per Client Queueing
Especially for guest networks we have to ensure a fair traffic priorization between all connected clients. Most of the time we want to limit each client, have a defined total maximum bandwidth (for example internet uplink) and we want this bandwidth to be fairly distributed between all clients.
So let's say we have an asymmetric internet connection with 50 Mbps downstream and 10 Mbps upstream which we want to be fairly distributed to all connected clients.
The simpliest thing would be something like this:
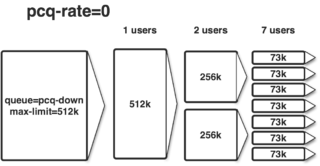
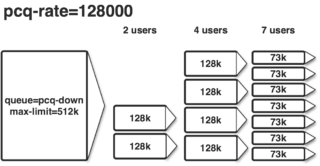
Our aim is to share the bandwidth amongst all users, i.e. if only one user is connected he may consume all bandwidth, if two are connected each gets half the bandwidth and so on.
A more sophisticated approach would additionally limit each client to a specific bandwidth and further reduce that assigned bandwidth if more clients a requesting bandwidth than totally available.
Illustration Source: Wiki Page
Are there any possibilities to achieve a similiar guaranteed fairly bandwidth distribution with Extreme WiFi?
A simple fixed rate limit does not work in real life since the actual per user bandwidth will depend on the current traffic/user situation.
We would be happy to get some brainstorming from Extreme community how you would handle these requirements. Or to definitely get the answer that it's simply not possible. When designind networks it is also important to know your limits.
Best regards, and looking forward to your ideas
David
1. Private PSKs, local and with RADIUS backend.
Some vendors support individual WPA2 PSKs for each connecting MAC Address.
The wireless system has a list of allowed mac addresses together with a unique PSK for each address.
This way every client can have its own WPA PSK, i.e. when you want to lock out one specific client from your wireless system, you do not have to change the WPA PSK on all devices.
It also prevents users from connecting other end devices to the wireless network as every PSK is bound to a specific MAC.
This is very handy to improve management and security in wireless network with clients which do not support WPA enterprise. And it minimizes the administrative overhead for 802.1x in smaller environments.
Other vendors support private PSKs also with RADIUS backends for centralized management.
We often have Extreme WiFi together with NAC, so this would be a perfect combination.
In NAC one would have to maintain PSKs for end systems and WiFi AP must be able to derive actual PSK from RADIUS response.
Source: Workshop Slides from other vendor, cf. page 78.
Are there any ideas or plans how this could be implemented with Extreme WiFi?
For me the only way right now seems to establish WPA enterprise which is more complicated for system administrators.
2. Per Client Queueing
Especially for guest networks we have to ensure a fair traffic priorization between all connected clients. Most of the time we want to limit each client, have a defined total maximum bandwidth (for example internet uplink) and we want this bandwidth to be fairly distributed between all clients.
So let's say we have an asymmetric internet connection with 50 Mbps downstream and 10 Mbps upstream which we want to be fairly distributed to all connected clients.
The simpliest thing would be something like this:
Our aim is to share the bandwidth amongst all users, i.e. if only one user is connected he may consume all bandwidth, if two are connected each gets half the bandwidth and so on.
A more sophisticated approach would additionally limit each client to a specific bandwidth and further reduce that assigned bandwidth if more clients a requesting bandwidth than totally available.
Illustration Source: Wiki Page
Are there any possibilities to achieve a similiar guaranteed fairly bandwidth distribution with Extreme WiFi?
A simple fixed rate limit does not work in real life since the actual per user bandwidth will depend on the current traffic/user situation.
We would be happy to get some brainstorming from Extreme community how you would handle these requirements. Or to definitely get the answer that it's simply not possible. When designind networks it is also important to know your limits.
Best regards, and looking forward to your ideas
David
5 REPLIES 5
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-17-2016 04:58 PM
1) I'd use 802.1X PEAP.
"We often have Extreme WiFi together with NAC, so this would be a perfect combination."
You'd create a NAC local user/pw repository for PEAP and also add the MACs to the database.
In that case you don't need any other external DB/devices and you'd do a lot more with NAC&roles.
The only difference is that the private key feature will allow also older clients that don't support 802.1X.
2) Doesn't work with the controller but I also like to see that function.
You'd search for "IAC box" - that is what I use in the meantime.
"We often have Extreme WiFi together with NAC, so this would be a perfect combination."
You'd create a NAC local user/pw repository for PEAP and also add the MACs to the database.
In that case you don't need any other external DB/devices and you'd do a lot more with NAC&roles.
The only difference is that the private key feature will allow also older clients that don't support 802.1X.
2) Doesn't work with the controller but I also like to see that function.
You'd search for "IAC box" - that is what I use in the meantime.