This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (WiNG)
- Can we stop WannaCry from being spread across netw...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Can we stop WannaCry from being spread across network?
Can we stop WannaCry from being spread across network?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-16-2017 11:04 AM
WannCry ransomware worm gets through SMB and other protocols.
There is a possible way to block these commands using ACL rule as follows:
ip access-list BROADCAST-MULTICAST-CONTROL
IP ACL shall be then used on every WLAN in outbound direction and optionally on physical interfaces also.
Some more details on web
Regards,
Ondrej
There is a possible way to block these commands using ACL rule as follows:
ip access-list BROADCAST-MULTICAST-CONTROL
- permit tcp any any rule-precedence 10 rule-description "permit all TCP traffic"
- permit udp any eq 67 any eq dhcpc rule-precedence 11 rule-description "permit DHCP replies"
- deny tcp any eq 445 any eq 445 rule-precedence 17 rule-description "deny SMB Traffic"
- deny tcp any eq 139 any eq netbios-ssn rule-precedence 18 rule-description "deny SMB Traffic"
- deny tcp any eq 137 any eq netbios-ns rule-precedence 19 rule-description "deny SMB Traffic"
- deny udp any range 137 138 any range 137 138 rule-precedence 20 rule-description "deny windows netbios"
- deny ip any 224.0.0.0/4 rule-precedence 21 rule-description "deny IP multicast"
- deny ip any host 255.255.255.255 rule-precedence 22 rule-description "deny IP local broadcast"
- permit ip any any rule-precedence 100 rule-description "permit all IP traffic"
IP ACL shall be then used on every WLAN in outbound direction and optionally on physical interfaces also.
Some more details on web
Regards,
Ondrej
10 REPLIES 10
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-17-2017 10:41 AM
Hi, all!
Some question from my colleagues:
- how is feel AD and Exchange authentication (user login) in domain-based network after deny all SMB traffic?
Thank you!
Some question from my colleagues:
- how is feel AD and Exchange authentication (user login) in domain-based network after deny all SMB traffic?
Thank you!
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-17-2017 10:41 AM
Alexandr,
Could you advise what particular guide you refer to?
In WiNG systems the direction respects the radio point of view
Direction outbound means Tx on radio.
Usin ACL in OUT direction will be then used to block outgoing traffic.
We usually use it to limit VLAN bcast.
Regards,
Ondrej
Could you advise what particular guide you refer to?
In WiNG systems the direction respects the radio point of view
Direction outbound means Tx on radio.
Usin ACL in OUT direction will be then used to block outgoing traffic.
We usually use it to limit VLAN bcast.
Regards,
Ondrej
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-17-2017 10:41 AM
OK.
You wrote that we have to put this ACL in outbound direction, BUT.
Client talk with server by ports 445, 137-139.
(By Wireless_User_Guide - outbound traffic in ACL is from Client to Network, inbound traffic is from Network to client)
So, we have to put this ACL in inbound direction? Isn't it?
Thank you!
You wrote that we have to put this ACL in outbound direction, BUT.
Client talk with server by ports 445, 137-139.
(By Wireless_User_Guide - outbound traffic in ACL is from Client to Network, inbound traffic is from Network to client)
So, we have to put this ACL in inbound direction? Isn't it?
Thank you!
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-17-2017 10:41 AM
Hi Alexandr,
as ACL blocks it only outbound, means that client will be able to get to the server and, if above description is correct, server will be able to get back to client.
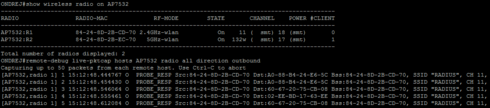
Honestly, we are shooting a fly with a bazooka, but if GPO are loose enough not to block SMBv1, then this might be very quick remedy to prevent worm from excessive spread. Not saying it is perfect though...
I cannot speak officially so for confirmation I strongly advise you to contact Microsoft support to get this correctly answered.
Regards,
Ondrej
as ACL blocks it only outbound, means that client will be able to get to the server and, if above description is correct, server will be able to get back to client.
Honestly, we are shooting a fly with a bazooka, but if GPO are loose enough not to block SMBv1, then this might be very quick remedy to prevent worm from excessive spread. Not saying it is perfect though...
I cannot speak officially so for confirmation I strongly advise you to contact Microsoft support to get this correctly answered.
Regards,
Ondrej