- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (WiNG)
- How I can configurate Radius authentication wtih i...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How I can configurate Radius authentication wtih internal controller Wing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-05-2020 11:33 PM
Hi every One
I try to configurate the Radius Authentication But It is not working, I saw the documentation in this link but I am not sure if my configuration it is ok
this is the link:
https://extremeportal.force.com/ExtrArticleDetail?an=000080864
and my configuration is:
aa-policy FabrilPolicy
authentication server 1 onboard controller
!
wlan VLAN400
ssid wirelessvlan400
vlan 400
bridging-mode tunnel
encryption-type ccmp
authentication-type eap
wpa-wpa2 psk 0 12345678
wireless-client count-per-radio 200
use aaa-policy FabrilPolicy
radius-group FabrilTest
rate-limit from-air 30000
rate-limit to-air 30000
policy inactivity-timeout 1800
!
radius-user-pool-policy UserRadius
user User2 password 0 1234567qwe group FabrilTest
user Mario password 0 12345678 group FabrilTest
user User1 password 0 87654321 group FabrilTest
!
radius-server-policy FabrilPolicy
use radius-user-pool-policy UserRadius
Could you help me, what is the problem for my configuration
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-05-2020 11:36 PM
Did you map the radius-server policy to the wireless controller at the device level?
From CLI:
enable [enter]
self [enter]
use radius-server-policy FabrilPolicy [enter]
end [enter]
commit write [enter]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-30-2020 11:34 PM
Hello Mario,
Your configuration shows internal radius to external LDAP user database. I have attached a document that covers LDAP integration using Wing internal radius.
Please ensure that the RFS4 is successfully binded to LDAP (all covered in the attached).
If issues are still persistent and if you have a current/valid support contract, please open a support case for further troubleshooting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-30-2020 10:03 PM
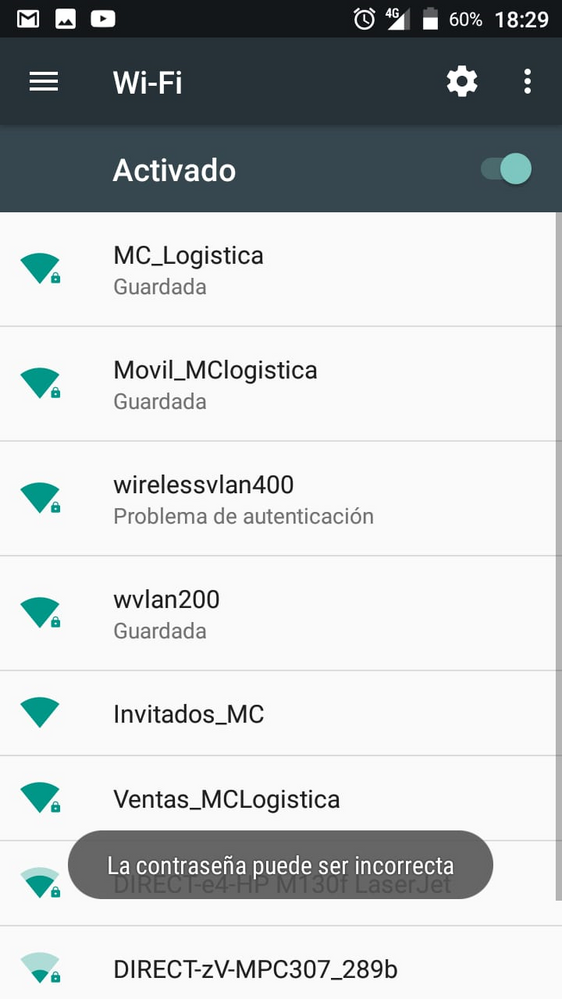
Hi I try a new configuration
and I see my bad configuration in wireless client but I have a one problem and I do not why
my recently configuration is
aaa-policy PolicyAAARadius
authentication server 1 onboard controller
wlan VLAN200
ssid VLAN200
vlan 200
bridging-mode tunnel
encryption-type ccmp
authentication-type eap
wpa-wpa2 psk 0 12345678
wireless-client count-per-radio 80
use wlan-qos-policy VLAN200QoS
use aaa-policy PolicyAAARadius
radius-group RadiusGroup
radius-server-policy ServerpolicyRa
authentication data-source ldap
authentication eap-auth-type peap-gtc
ldap-server primary host 192.168.200.20 port 389 login "(sAMAccountName=%{Stripped-User-Name:-%{User-Name}})" bind-dn "CN=Mario Martinez,CN=Users,DC=abstergo,DC=com" base-dn "CN=Users,DC=abstergo,DC=com" passwd 0 Banco2018 passwd-attr UserPassword group-attr cn group-filter "(|(&(objectClass=group)(member=%{Ldap-UserDn}))(&(objectClass=GroupOfUniqueNames)(uniquemember=%{Ldap-userDn})))" group-membership radiusGroupName net-timeout 10
use radius-group RadiusGroup
profile rfs4000 RFS4000-TEST
no autoinstall configuration
no autoinstall firmware
use radius-server-policy ServerpolicyRa
…
but always show me this message
Mar 31 16:05:22 2019: %DAEMON-6-INFO: radiusd[2490]: rlm_ldap (ldap_primary): Closing connection (10): Hit idle_timeout, was idle for 303 seconds
Mar 31 16:05:22 2019: %DAEMON-6-INFO: radiusd[2490]: rlm_ldap (ldap_primary): Closing connection (7): Hit idle_timeout, was idle for 303 seconds
Mar 31 16:05:22 2019: %DAEMON-6-INFO: radiusd[2490]: rlm_ldap (ldap_primary): Closing connection (9): Hit idle_timeout, was idle for 291 seconds
Mar 31 16:05:22 2019: %DAEMON-6-INFO: radiusd[2490]: rlm_ldap (ldap_primary): Closing connection (11): Hit idle_timeout, was idle for 291 seconds
Mar 31 16:05:22 2019: %DAEMON-6-INFO: radiusd[2490]: rlm_ldap (ldap_primary): Closing connection (8): Hit idle_timeout, was idle for 291 seconds
Mar 31 16:05:22 2019: %DAEMON-6-INFO: radiusd[2490]: rlm_ldap (ldap_primary): Opening additional connection (12), 1 of 32 pending slots used
Mar 31 16:05:22 2019: %DAEMON-6-INFO: radiusd[2490]: Need 2 more connections to reach min connections (3)
Mar 31 16:05:22 2019: %DAEMON-6-INFO: radiusd[2490]: rlm_ldap (ldap_primary): Opening additional connection (13), 1 of 31 pending slots used
Mar 31 16:05:22 2019: %DAEMON-5-NOTICE: radiusd[2490]: (10) auth: found User-Policy = Reject, rejecting user: [nescobar] (from client localhost port 1 cli B4-29-3D-19-1A-B1)
Mar 31 16:05:22 2019: %DAEMON-5-NOTICE: radiusd[2490]: (10) Login incorrect: [nescobar] (from client localhost port 1 cli B4-29-3D-19-1A-B1)
Mar 31 16:05:22 2019: ap7632-14E2D5 : %DOT11-5-EAP_FAILED: Client 'B4-29-3D-19-1A-B1' failed 802.1x/EAP authentication on wlan 'VLAN200' radio 'ap7632-14E2D5:R2'
I understand that it is due to bad EAP configuration in the wireless client but I already defined it to be PEAP-GTC and it is not working for me
this is my wireles client configuration
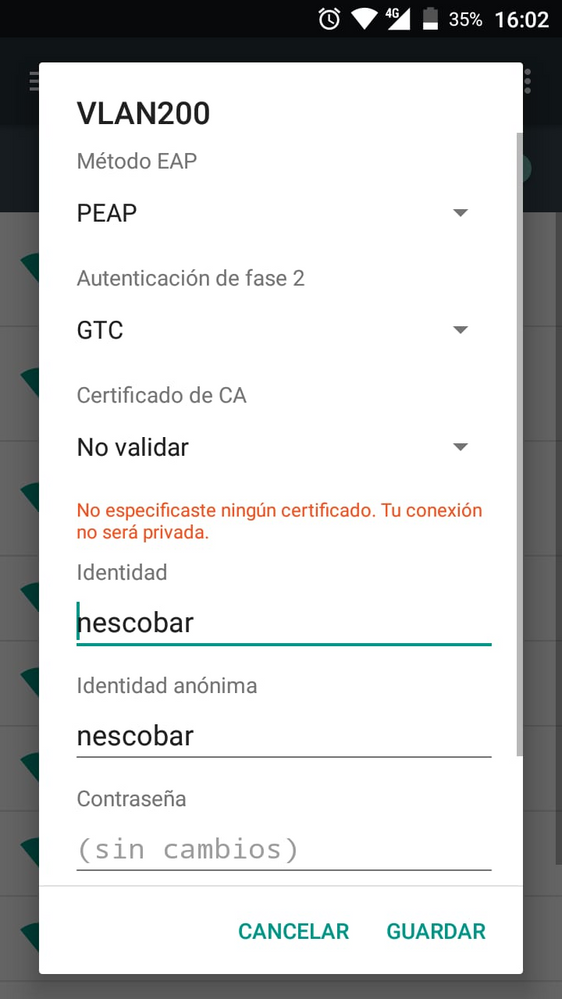
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-06-2020 04:36 PM
Have you configured the wireless client supplicant correctly?
What EAP method is the wireless client using?
I assume PEAP/MSCHAPv2 based on user/password. If using certificate, the RFS would need to be staged as such. If no certificate is being used, ensure that “no validate server cert” on wireless client supplicant is checked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-06-2020 12:32 AM
I try your comment, this is the controller configuration
rfs4000 B4-C7-99-FB-82-ED
use profile default-rfs4000
use rf-domain TEST
hostname rfs4000-FB82ED
license AP DEFAULT-6AP-LICENSE
license ADSEC DEFAULT-ADV-SEC-LICENSE
ip domain-name 8.8.4.4
ip default-gateway 192.168.200.1
use radius-server-policy FabrilPolicy
interface up1
switchport mode trunk
switchport trunk allowed vlan 1,200,400
switchport trunk native vlan 1
interface ge3
switchport mode access
switchport access vlan 200
interface vlan1
ip address dhcp
ip address 192.168.0.1/24 secondary
no ip dhcp client request options all
interface vlan200
ip address 192.168.200.50/24
ip dhcp client request options all
interface vlan400
ip address 192.168.4.50/24
use dhcp-server-policy TEST-DHCP
This message send me when I try to connect the wireless vlan400